這篇文章整理了筆者在練習 CTF 題目時常用的工具,有些工具在後續也會頻繁使用。另外,如果你有興趣一起跟著文章進行練習,可以使用文中提供的 Docker 環境,裡面已經包含了後續教學中會使用到的工具,此 repo 包含後面的題目及環境
Dockerfile
FROM ubuntu:22.04
MAINTAINER YJK
RUN apt-get update
RUN yes | unminimize
RUN apt-get install -y tini iproute2 iputils-ping net-tools netcat
RUN apt-get install -y openssh-server sudo vim grep gawk rsync tmux diffutils file
RUN apt-get install -y gcc gdb make yasm nasm tcpdump python3 python3-pip python3-virtualenv
RUN apt-get install -y gcc-multilib g++-multilib
RUN apt-get install -y libc6-dbg dpkg-dev
RUN apt-get install -y curl git zsh
RUN apt-get install -y ruby-dev wget
RUN pip3 install pwntools capstone filebytes keystone-engine ropper
RUN gem install seccomp-tools
RUN gem install one_gadget
RUN mkdir /var/run/sshd
RUN echo 'PermitEmptyPasswords yes' >> /etc/ssh/sshd_config
RUN sed -i 's/nullok_secure/nullok/' /etc/pam.d/common-auth
RUN echo '%sudo ALL=(ALL) NOPASSWD:ALL' >> /etc/sudoers
USER root
RUN git clone https://github.com/pwndbg/pwndbg ~/pwndbg
RUN cd ~/pwndbg && ./setup.sh
RUN git clone https://github.com/scwuaptx/Pwngdb.git ~/Pwngdb
RUN cp ~/Pwngdb/.gdbinit ~/
RUN rm -rf ~/.gdbinit
RUN echo "source ~/pwndbg/gdbinit.py" >> ~/.gdbinit
RUN echo "source ~/Pwngdb/pwngdb.py" >> ~/.gdbinit
RUN echo "source ~/Pwngdb/angelheap/gdbinit.py" >> ~/.gdbinit
RUN echo "define hook-run" >> ~/.gdbinit
RUN echo "python" >> ~/.gdbinit
RUN echo "import angelheap" >> ~/.gdbinit
RUN echo "angelheap.init_angelheap()" >> ~/.gdbinit
RUN echo "end" >> ~/.gdbinit
RUN echo "end" >> ~/.gdbinit
USER root
# run the service
EXPOSE 22
ENTRYPOINT ["/usr/bin/tini", "--"]
CMD ["/usr/sbin/sshd", "-D"]
docker-compose.yml
version: '2'
services:
main:
build: .
restart: unless-stopped
privileged: true
ports:
- "22224:22"
environment:
- EDITOR=vim
volumes:
- ./share:/home
networks:
default:
networks:
default:
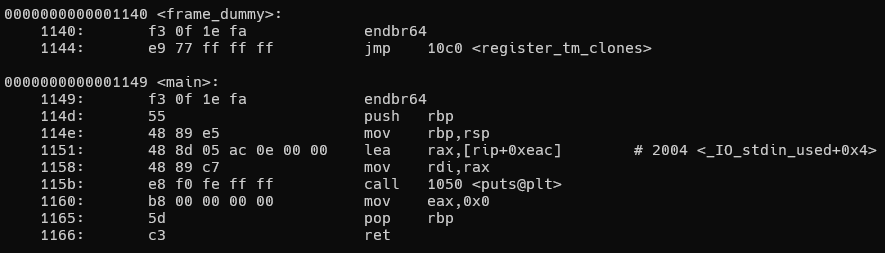
objdump -M intel -d chal,-M intel 指定架構為 Intel,-d chal 指定要反組譯的檔案為 chal
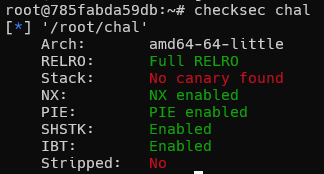
checksec.sh
rbp 和 return address,就有機會使用 one_gadget 取得 shell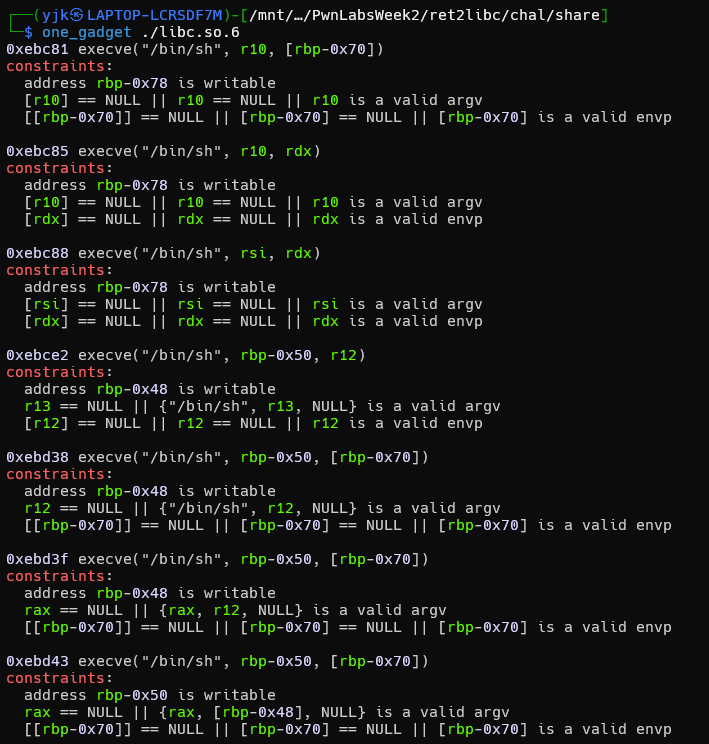
nc 進行連線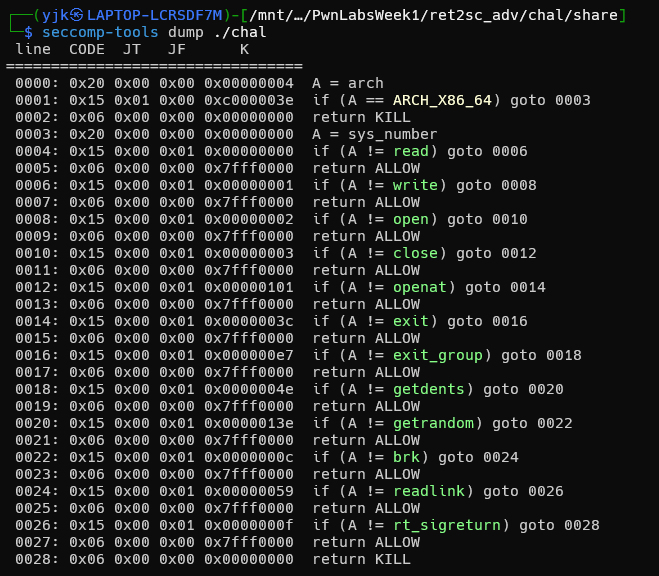
筆者提供的 Docker 環境即包含 pwndbg 和 pwngdb。
from pwn import *
remote('IP address', port)
process('./chal')
r.send(payload):傳送 payloadr.sendline(payload):傳送 payload 並換行r.sendafter(string, payload):在收到指定 string 後傳送 payloadr.sendlineafter(string, payload):在收到指定 string 後傳送 payload 並換行r.recv(n):接收 n 個字元r.recvline():接收一行資料r.recvlines(n):接收 n 行資料r.recvuntil(string):接收到指定的 string 為止r.interactive()
p32(0xdeadbeef)
p64(0xdeadbeef)
hex(u32(b'\xef\xbe\xad\xde'))
hex(u64(b'\xef\xbe\xad\xde\x00\x00\x00\x00'))
gdb.attach(r)
context.terminal = ["tmux", "splitw", "-h"]
