各位大師
小弟是剛接觸網路&防火牆的新手,最近在設定sslvpn讓外網可以透過sslvpn連線進內網的不同網段,但是sslvpn是設定好了 可以連線成功 但是卻無法ping到內網的設備...
FortiGate 100E:
interface port3 = NAS > Vlan 500(172.16.1.254/24)
Policy :
sslvpn > vlan500
sslvpn > wan
vlan500 > sslvpn
vlan500 > wan
Cisco 9300:
vlan 100
vlan 200
vlan 300
vlan 400
valn 500 vlanip 172.16.1.253
ip route = 0.0.0.0/172.16.1.254
再請高手解惑了...
抱歉 新手被限制回應 我就回應在此了
SSLVPN連通後 可以ping到Forti port172.16.1.254
架構圖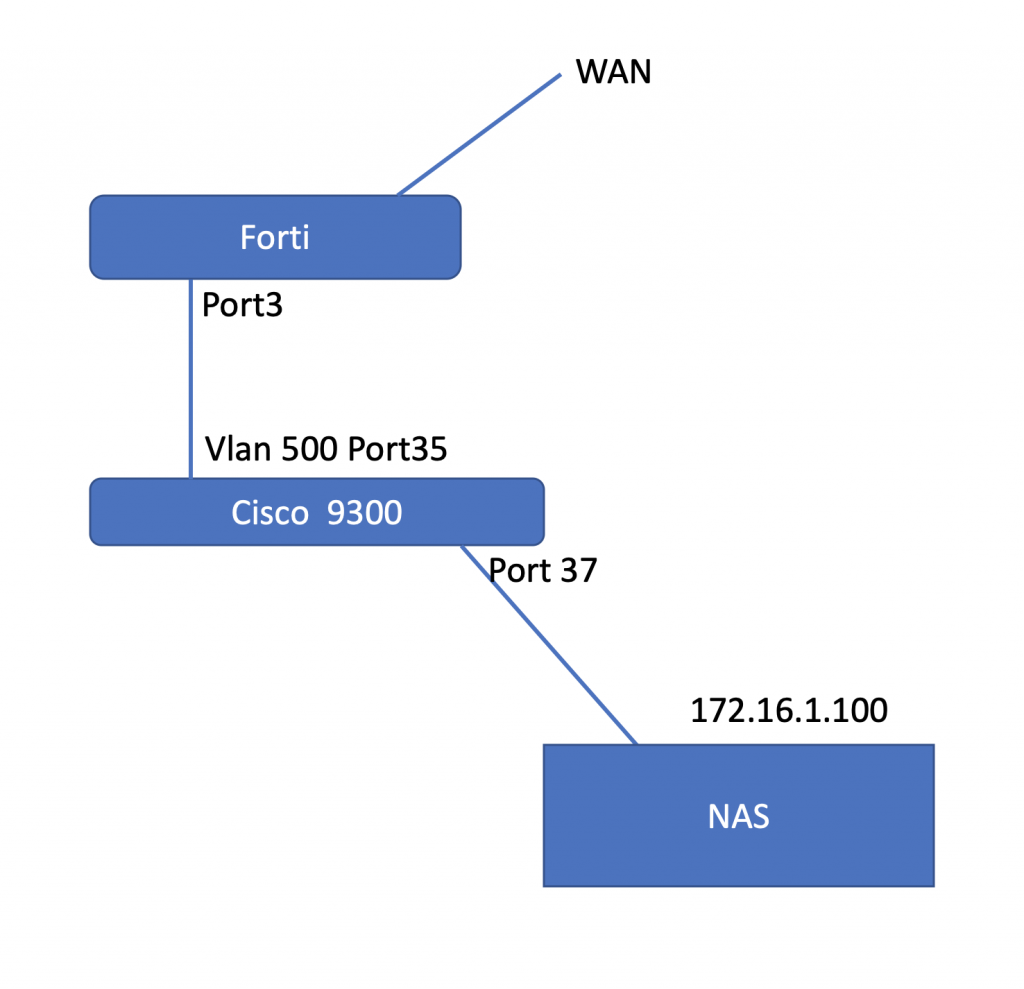
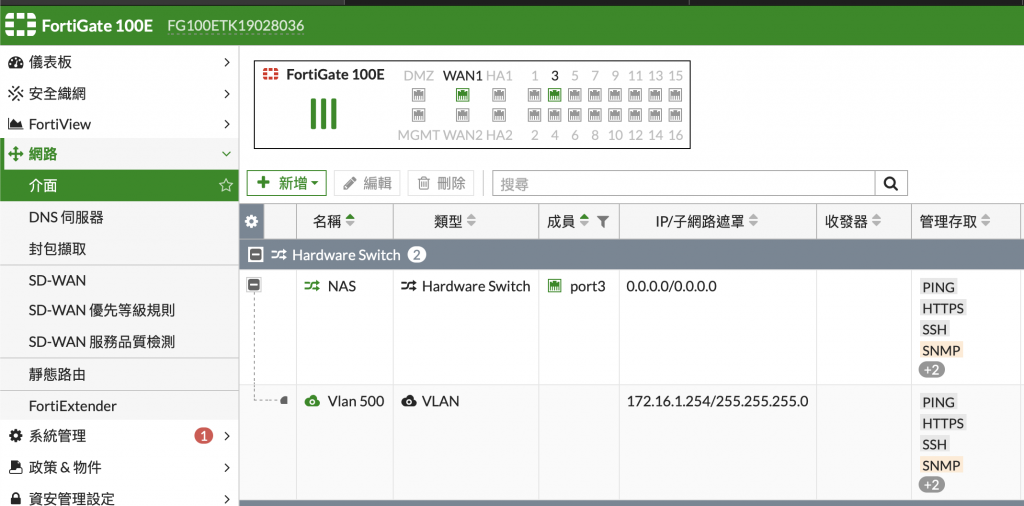
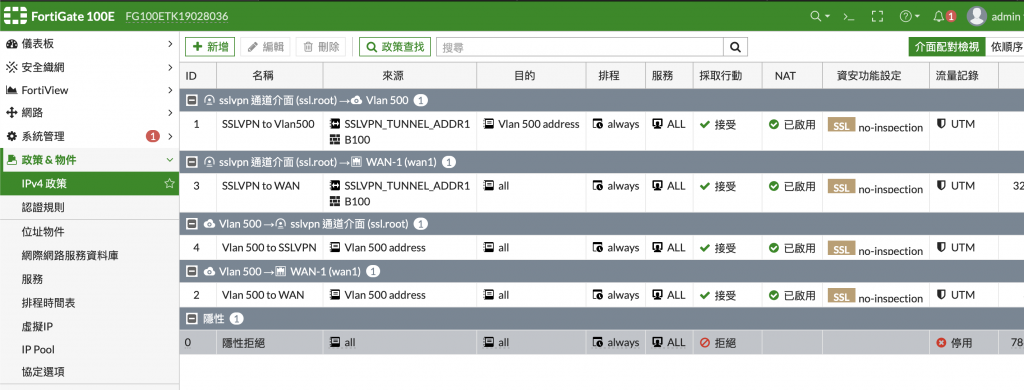
Cisco config
!Command: show running-config
!Running configuration last done at: Mon Jun 1 05:44:35 2020
!Time: Mon Jun 1 05:50:48 2020
version 9.3(3) Bios:version 07.66
switchname 9300
vdc 9300 id 1
limit-resource vlan minimum 16 maximum 4094
limit-resource vrf minimum 2 maximum 4096
limit-resource port-channel minimum 0 maximum 511
limit-resource u4route-mem minimum 248 maximum 248
limit-resource u6route-mem minimum 96 maximum 96
limit-resource m4route-mem minimum 58 maximum 58
limit-resource m6route-mem minimum 8 maximum 8
feature telnet
cfs eth distribute
feature ospf
feature interface-vlan
feature vpc
username admin password 5
role network-admin
ip domain-lookup
system default switchport
copp profile strict
snmp-server user admin network-admin auth md5 0x9543e1b36fcf94a86648d257d4487b6b
priv 0x9543e1b36fcf94a86648d257d4487b6b localizedkey
rmon event 1 description FATAL(1) owner PMON@FATAL
rmon event 2 description CRITICAL(2) owner PMON@CRITICAL
rmon event 3 description ERROR(3) owner PMON@ERROR
rmon event 4 description WARNING(4) owner PMON@WARNING
rmon event 5 description INFORMATION(5) owner PMON@INFO
ip route 0.0.0.0/0 172.16.1.254
vlan 1,100,200,300,400,500
vlan 100
name WAN
vlan 200
name DMZ
vlan 300
name DemoLab
vlan 400
name OBS
vlan 500
name NAS
vrf context management
vlan configuration 100
interface Vlan1
interface Vlan100
no shutdown
interface Vlan200
no shutdown
management
ip address 10.1.1.253/24
interface Vlan300
no shutdown
management
ip address 10.10.0.253/16
interface Vlan400
no shutdown
management
ip address 10.100.1.253/24
interface Vlan500
no shutdown
management
ip address 172.16.1.253/24
.
.
.
省略
interface Ethernet1/35
description NAS
shutdown
switchport mode trunk
switchport access vlan 500
switchport trunk allowed vlan 100,200,300,400,500
更新...
非常感謝m大的提示 實在有不得已的原因 才上來求問 請各位大師幫解
我加了一筆路由 但是還是無法ping到253...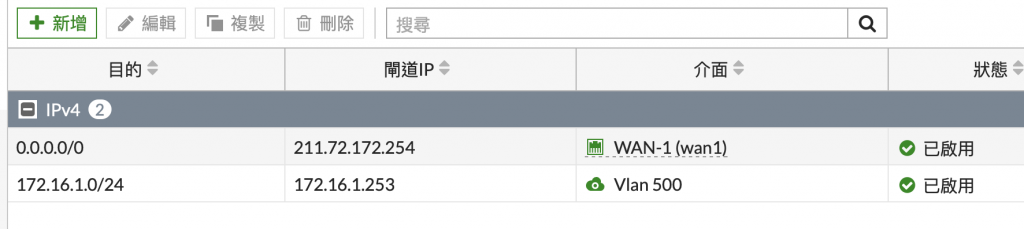
更新
Cisco端可以ping到我vpn上去的ip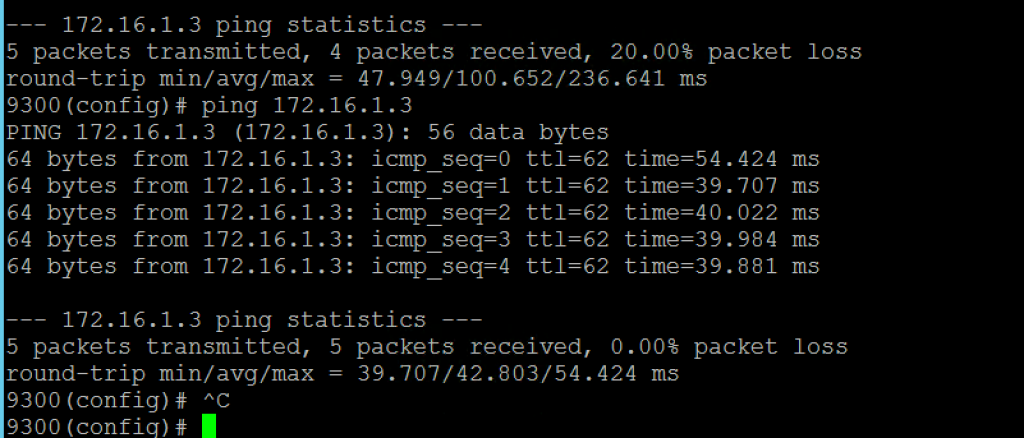
6/1 16:40 更新
找到問題了~感謝各位M大的解析 , 獲益良多! 兇手就是 SSLVPN_TUNNEL_ADDR1的IP不能重疊在任何設備上! 也就是給予的這段IP必須要保留下來給VPN Client撥進來取用的 謝謝給予意見的大大們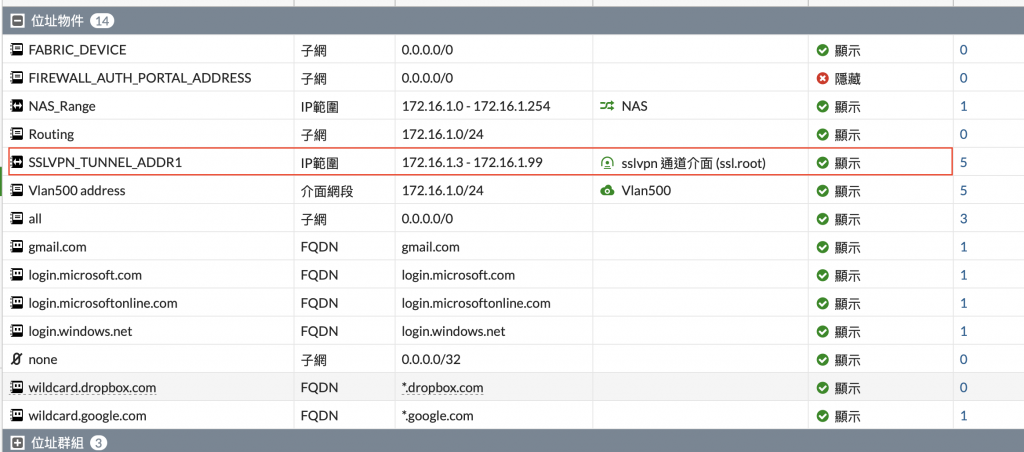

樓主如果有架構圖會更好研判點
請問目前SSLVPN連通後,可以ping到哪裡?
是只能到SSLVPN的介面嗎?
其他Fortigate的介面IP呢?
非常有可能如果是Cisco下面的內網連不到
這樣需要加CISCO下的網段路由
這樣SSLVPN的網段與CISCO才能互通
連上SSLVPN後,檢查一下該電腦的路由,是否有內部網路的路由,以板大的例子,連上VPN的電腦應該要加5筆路由vlan100~vlan500