今天電腦重開機,重啟was的container,要登入console時發現
壞了
雖然console壞掉,但掛在上面的程式還是能正常運作
合理懷疑應該是之前調整SSL設定導致的
但是要還原設定,卻又沒辦法從console去做操作怎麼辦呢?
這邊我先下指令建一個新的環境
docker run --name test-was2 -p 9043:9043 -p 9060:9060 -p 9080:9080 -p 9443:9443 -d ibmcom/websphere-traditional:8.5.5.20
重建一個container,把舊的刪掉就好了
登入新的console ,
左側選單 > SSL certificate and key management > SSL configurations > NodeDefaultSSLSettings > Quality of protection (QoP) settings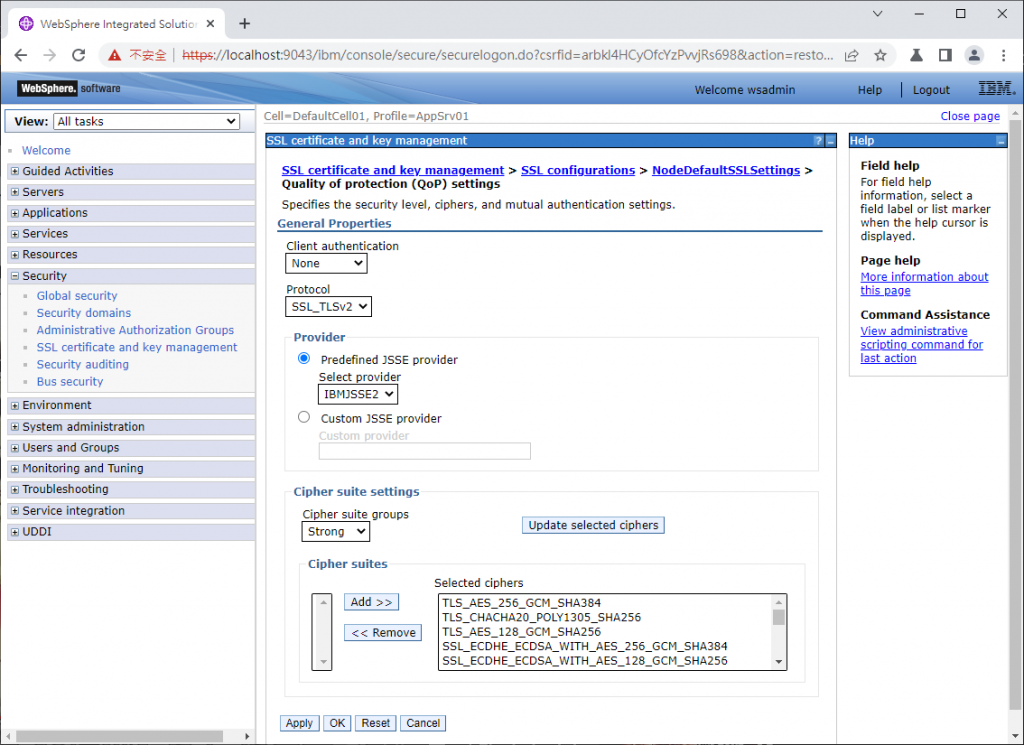
來到QoP頁面
可以看到畫面右方有個View administrative scripting command for last action
點擊後跳出視窗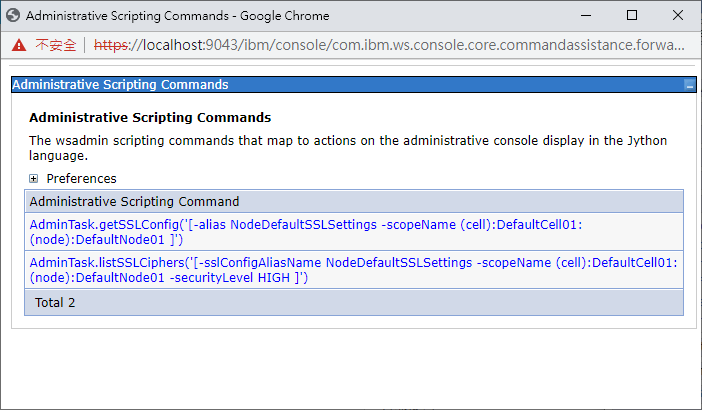
這裡會列出我們在console上所做的動作對應的jython指令
AdminTask.getSSLConfig('[-alias NodeDefaultSSLSettings -scopeName (cell):DefaultCell01:(node):DefaultNode01 ]')
AdminTask.listSSLCiphers('[-sslConfigAliasName NodeDefaultSSLSettings -scopeName (cell):DefaultCell01:(node):DefaultNode01 -securityLevel HIGH ]')
我在console上調整protocol,小視窗也對應的顯示一樣動作的指令
AdminTask.modifySSLConfig('[-alias NodeDefaultSSLSettings -scopeName (cell):DefaultCell01:(node):DefaultNode01 -keyStoreName NodeDefaultKeyStore -keyStoreScopeName (cell):DefaultCell01:(node):DefaultNode01 -trustStoreName NodeDefaultTrustStore -trustStoreScopeName (cell):DefaultCell01:(node):DefaultNode01 -jsseProvider IBMJSSE2 -sslProtocol SSL_TLSv2 -clientAuthentication false -clientAuthenticationSupported false -securityLevel HIGH -enabledCiphers ]')
AdminTask.modifySSLConfig('[-alias NodeDefaultSSLSettings -scopeName (cell):DefaultCell01:(node):DefaultNode01 -keyStoreName NodeDefaultKeyStore -keyStoreScopeName (cell):DefaultCell01:(node):DefaultNode01 -trustStoreName NodeDefaultTrustStore -trustStoreScopeName (cell):DefaultCell01:(node):DefaultNode01 -jsseProvider IBMJSSE2 -sslProtocol SSL_TLSv2 -clientAuthentication false -clientAuthenticationSupported false -securityLevel CUSTOM -enabledCiphers "SSL_DHE_DSS_WITH_AES_128_CBC_SHA SSL_DHE_DSS_WITH_AES_128_CBC_SHA256 SSL_DHE_DSS_WITH_AES_128_GCM_SHA256 SSL_DHE_DSS_WITH_AES_256_CBC_SHA SSL_DHE_DSS_WITH_AES_256_CBC_SHA256 SSL_DHE_DSS_WITH_AES_256_GCM_SHA384 SSL_DHE_RSA_WITH_AES_128_CBC_SHA SSL_DHE_RSA_WITH_AES_128_CBC_SHA256 SSL_DHE_RSA_WITH_AES_128_GCM_SHA256 SSL_DHE_RSA_WITH_AES_256_CBC_SHA SSL_DHE_RSA_WITH_AES_256_CBC_SHA256 SSL_DHE_RSA_WITH_AES_256_GCM_SHA384 SSL_ECDHE_ECDSA_WITH_AES_128_CBC_SHA SSL_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 SSL_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 SSL_ECDHE_ECDSA_WITH_AES_256_CBC_SHA SSL_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 SSL_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 SSL_ECDHE_RSA_WITH_AES_128_CBC_SHA SSL_ECDHE_RSA_WITH_AES_128_CBC_SHA256 SSL_ECDHE_RSA_WITH_AES_128_GCM_SHA256 SSL_ECDHE_RSA_WITH_AES_256_CBC_SHA SSL_ECDHE_RSA_WITH_AES_256_CBC_SHA384 SSL_ECDHE_RSA_WITH_AES_256_GCM_SHA384 SSL_ECDH_ECDSA_WITH_AES_128_CBC_SHA SSL_ECDH_ECDSA_WITH_AES_128_CBC_SHA256 SSL_ECDH_ECDSA_WITH_AES_128_GCM_SHA256 SSL_ECDH_ECDSA_WITH_AES_256_CBC_SHA SSL_ECDH_ECDSA_WITH_AES_256_CBC_SHA384 SSL_ECDH_ECDSA_WITH_AES_256_GCM_SHA384 SSL_ECDH_RSA_WITH_AES_128_CBC_SHA SSL_ECDH_RSA_WITH_AES_128_CBC_SHA256 SSL_ECDH_RSA_WITH_AES_128_GCM_SHA256 SSL_ECDH_RSA_WITH_AES_256_CBC_SHA SSL_ECDH_RSA_WITH_AES_256_CBC_SHA384 SSL_ECDH_RSA_WITH_AES_256_GCM_SHA384 SSL_RSA_WITH_AES_128_CBC_SHA SSL_RSA_WITH_AES_128_CBC_SHA256 SSL_RSA_WITH_AES_128_GCM_SHA256 SSL_RSA_WITH_AES_256_CBC_SHA SSL_RSA_WITH_AES_256_CBC_SHA256 SSL_RSA_WITH_AES_256_GCM_SHA384 TLS_AES_128_GCM_SHA256 TLS_AES_256_GCM_SHA384 TLS_CHACHA20_POLY1305_SHA256 TLS_DHE_RSA_WITH_CHACHA20_POLY1305_SHA256 TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256" ]')
指令先複製起來放著,
接著回到壞掉的WebSphere,以docker指令進入container
docker exec -it test-was8.5.5.20 bash
進入container後
cd /opt/IBM/WebSphere/AppServer/bin
./wsadmin.sh -lang jython
正常情況下可以進入wsadmin介面下指令,不過現在看起來連soap連線都有問題...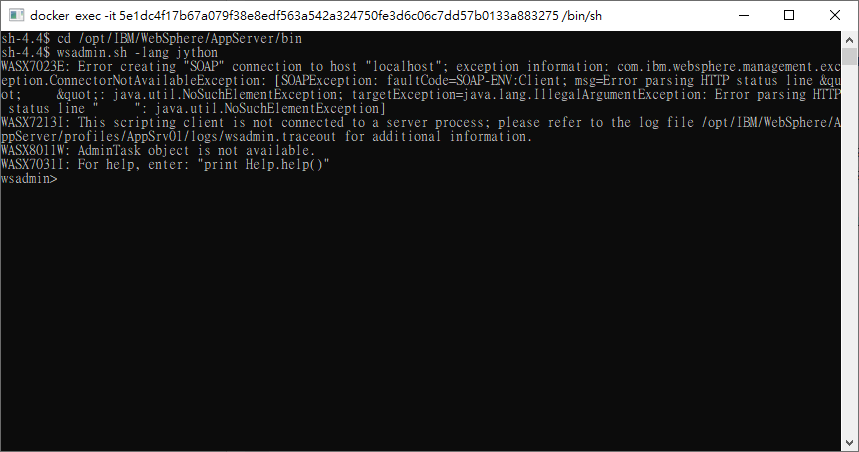
不過沒關係,還有別的辦法,就是直接修改xml設定檔
先回到新建的WebSphere環境,
一般在console做異動時,我們都會直接按save存檔,這裡先不save,按review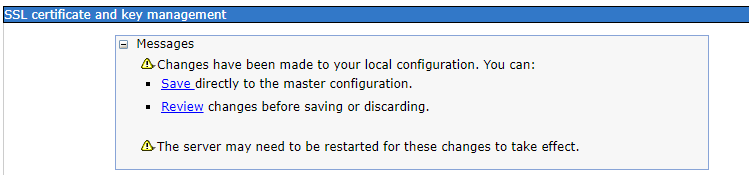
此時就可以看到我們做的異動是修改了哪個檔案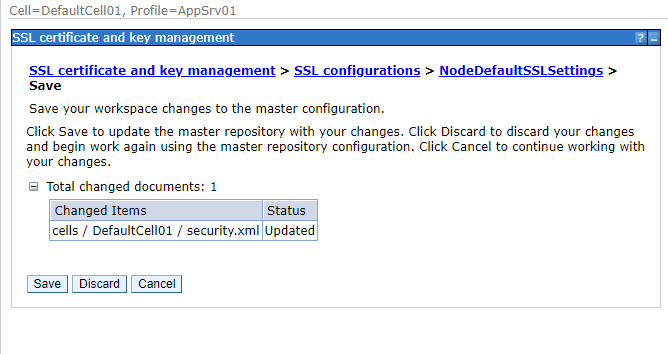
知道了是修改 security.xml 後,就可以手動調整了
這個檔案的位置在此
/opt/IBM/WebSphere/AppServer/profiles/AppSrv01/config/cells/DefaultCell01
來到壞掉的WebSphere環境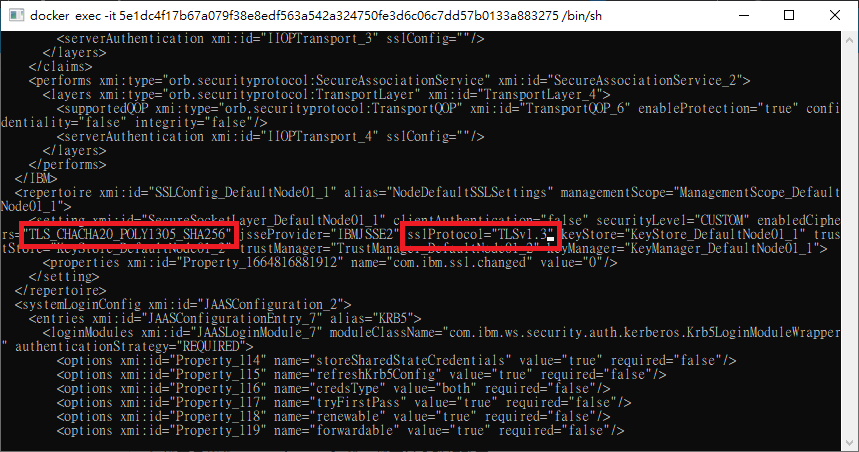
進入後可以看到protocol跟cipher就寫在這裡,
我把protocol改回SSL_TLSv2
cipher改回上面貼的那一大串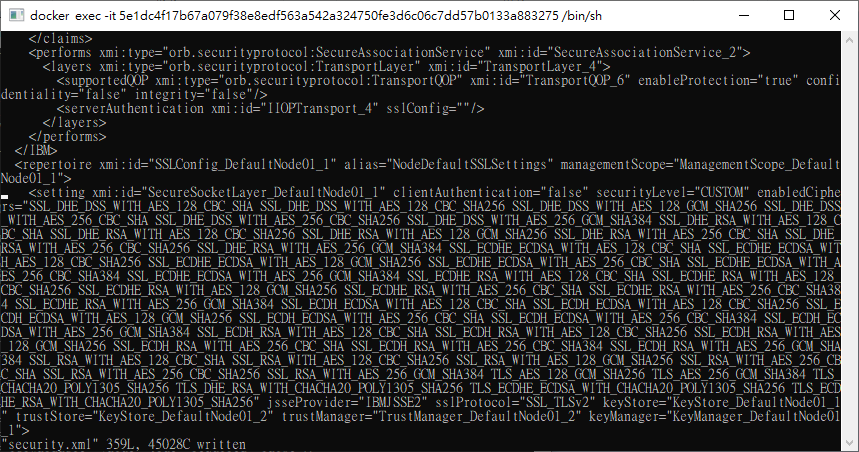
存檔後重啟,
果然就恢復正常了。
最後再補充,正常情況下的wsadmin.sh,
cd /opt/IBM/WebSphere/AppServer/bin
./wsadmin.sh -lang jython
輸入跟console一樣的wsadmin帳密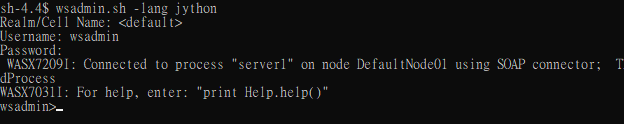
接著就可以執行前面貼出來的script了
還有很多操作能夠執行,可參閱IBM文件
https://www.ibm.com/docs/en/was/8.5.5?topic=concepts-using-wsadmin-scripting-jython
