Day 17: 使用 AWS EC2 部署 Docker 容器
Day 18: AWS Elastic Kubernetes Service (EKS) 入門
Day 19: 設置 AWS ALB(Application Load Balancer)進行負載均衡
Day 20: AWS Auto Scaling 自動調整實例數量
Day 21: AWS S3 與容器化應用數據存儲
Day 22: 使用 AWS RDS 管理關聯式資料庫
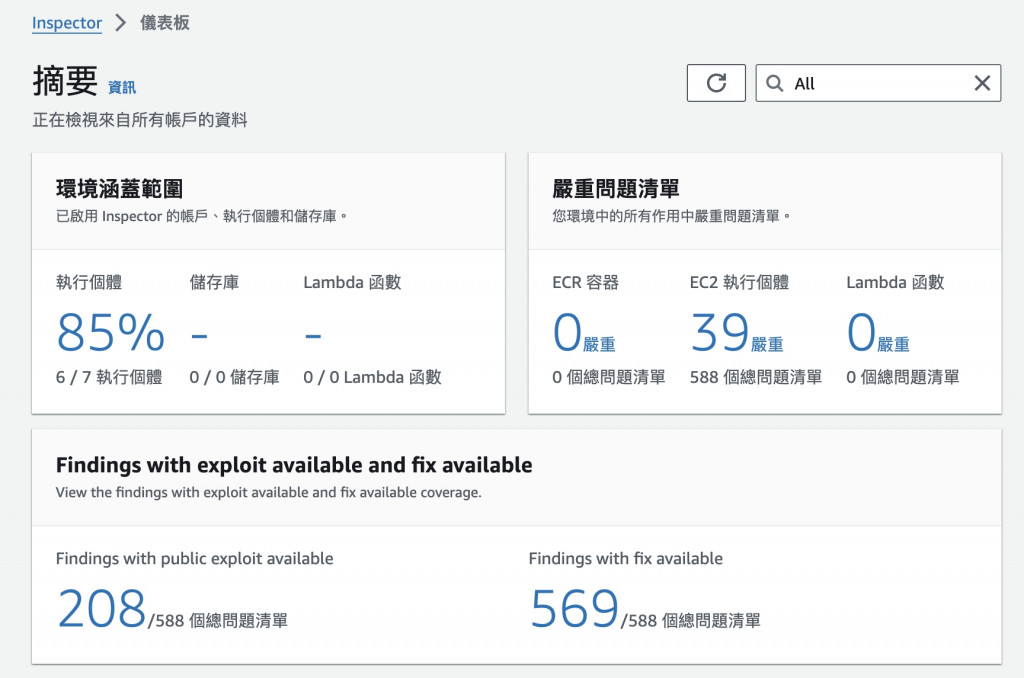
Day 23: 使用 AWS Inspector 進行安全性掃描與合規性檢查
Day18-23都會產生費用,不適用於免費方案,請斟酌練習喔!
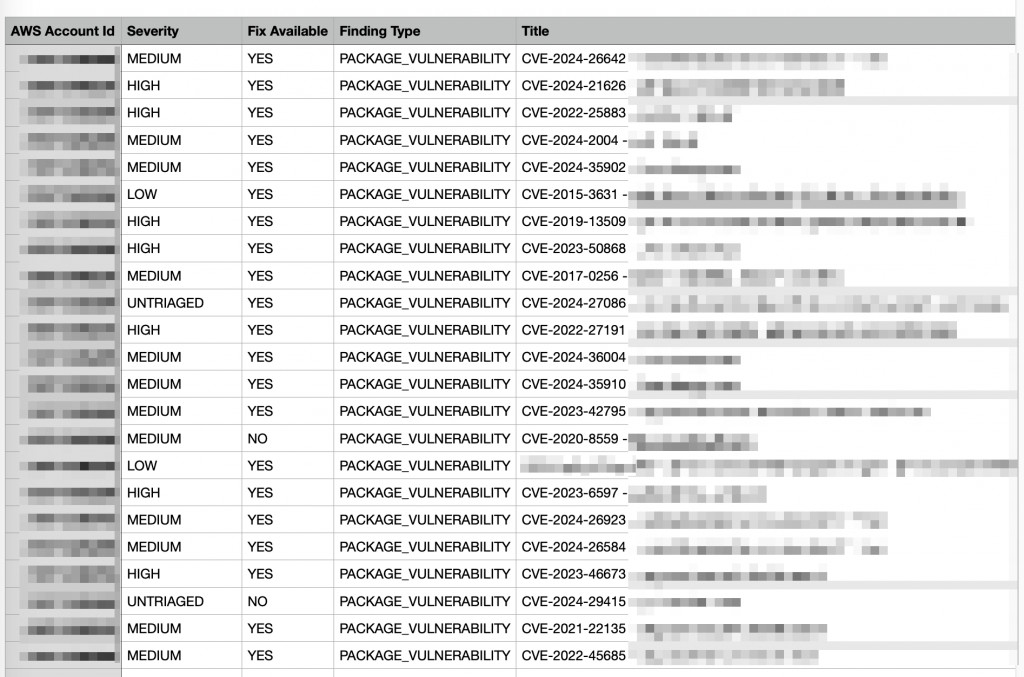
AWS Inspector 是一個自動化安全評估服務,用於掃描和分析 AWS 環境中的工作負載。它能夠檢測潛在的安全漏洞、配置問題和符合性風險,並提供修復建議。通過整合到 DevOps 流程中,AWS Inspector 有助於持續改進雲環境的安全性和合規性。
區域:
每月 EC2 掃描 (包括持續漏洞和網路連線掃描)
使用 SSM 代理程式型掃描每月掃描的平均 Amazon EC2 執行個體數* 每個執行個體 1.2528 USD
點擊啟用,就這麼簡單(?)
角色名稱:AWSServiceRoleForAmazonInspector2
以下政策文件包含 Inspector 所需的許可,以偵測和保護 AWS 環境中的資源。
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"directconnect:DescribeConnections",
"directconnect:DescribeDirectConnectGatewayAssociations",
"directconnect:DescribeDirectConnectGatewayAttachments",
"directconnect:DescribeDirectConnectGateways",
"directconnect:DescribeVirtualGateways",
"directconnect:DescribeVirtualInterfaces",
"directconnect:DescribeTags",
"ec2:DescribeTags",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeCustomerGateways",
"ec2:DescribeInstances",
"ec2:DescribeInternetGateways",
"ec2:DescribeManagedPrefixLists",
"ec2:DescribeNatGateways",
"ec2:DescribeNetworkAcls",
"ec2:DescribeNetworkInterfaces",
"ec2:DescribePrefixLists",
"ec2:DescribeRegions",
"ec2:DescribeRouteTables",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSubnets",
"ec2:DescribeTransitGatewayAttachments",
"ec2:DescribeTransitGatewayConnects",
"ec2:DescribeTransitGatewayPeeringAttachments",
"ec2:DescribeTransitGatewayRouteTables",
"ec2:DescribeTransitGatewayVpcAttachments",
"ec2:DescribeTransitGateways",
"ec2:DescribeVpcEndpointServiceConfigurations",
"ec2:DescribeVpcEndpoints",
"ec2:DescribeVpcPeeringConnections",
"ec2:DescribeVpcs",
"ec2:DescribeVpnConnections",
"ec2:DescribeVpnGateways",
"ec2:GetManagedPrefixListEntries",
"ec2:GetTransitGatewayRouteTablePropagations",
"ec2:SearchTransitGatewayRoutes",
"elasticloadbalancing:DescribeListeners",
"elasticloadbalancing:DescribeLoadBalancerAttributes",
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeRules",
"elasticloadbalancing:DescribeTags",
"elasticloadbalancing:DescribeTargetGroups",
"elasticloadbalancing:DescribeTargetHealth",
"network-firewall:DescribeFirewall",
"network-firewall:DescribeFirewallPolicy",
"network-firewall:DescribeResourcePolicy",
"network-firewall:DescribeRuleGroup",
"network-firewall:ListFirewallPolicies",
"network-firewall:ListFirewalls",
"network-firewall:ListRuleGroups",
"tiros:CreateQuery",
"tiros:GetQueryAnswer"
],
"Resource": [
"*"
]
},
{
"Effect": "Allow",
"Action": [
"codeguru-security:CreateScan",
"codeguru-security:GetScan",
"codeguru-security:ListFindings",
"codeguru-security:BatchGetFindings",
"codeguru-security:DeleteScansByCategory",
"iam:GetRole",
"iam:GetRolePolicy",
"iam:GetPolicy",
"iam:GetPolicyVersion",
"iam:ListAttachedRolePolicies",
"iam:ListPolicies",
"iam:ListPolicyVersions",
"lambda:ListVersionsByFunction"
],
"Resource": [
"*"
]
},
{
"Effect": "Allow",
"Action": [
"ecr:BatchGetImage",
"ecr:BatchGetRepositoryScanningConfiguration",
"ecr:DescribeImages",
"ecr:DescribeRegistry",
"ecr:DescribeRepositories",
"ecr:GetAuthorizationToken",
"ecr:GetDownloadUrlForLayer",
"ecr:GetRegistryScanningConfiguration",
"ecr:ListImages",
"ecr:PutRegistryScanningConfiguration",
"organizations:DescribeAccount",
"organizations:DescribeOrganization",
"organizations:ListAccounts",
"ssm:DescribeAssociation",
"ssm:DescribeAssociationExecutions",
"ssm:DescribeInstanceInformation",
"ssm:ListAssociations",
"ssm:ListResourceDataSync"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"lambda:ListFunctions",
"lambda:GetFunction",
"lambda:GetLayerVersion",
"cloudwatch:GetMetricData"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"ssm:CreateAssociation",
"ssm:StartAssociationsOnce",
"ssm:DeleteAssociation",
"ssm:UpdateAssociation"
],
"Resource": [
"arn:*:ec2:*:*:instance/*",
"arn:*:ssm:*:*:document/AmazonInspector2-*",
"arn:*:ssm:*:*:document/AWS-GatherSoftwareInventory",
"arn:*:ssm:*:*:managed-instance/*",
"arn:*:ssm:*:*:association/*"
]
},
{
"Effect": "Allow",
"Action": [
"ssm:CreateResourceDataSync",
"ssm:DeleteResourceDataSync"
],
"Resource": [
"arn:*:ssm:*:*:resource-data-sync/InspectorResourceDataSync-do-not-delete"
]
},
{
"Effect": "Allow",
"Action": [
"events:PutRule",
"events:DeleteRule",
"events:DescribeRule",
"events:ListTargetsByRule",
"events:PutTargets",
"events:RemoveTargets"
],
"Resource": [
"arn:*:events:*:*:rule/DO-NOT-DELETE-AmazonInspector*ManagedRule"
]
}
]
}
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "inspector2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "allow-inspector",
"Effect": "Allow",
"Principal": {
"Service": "inspector2.amazonaws.com"
},
"Action": [
"s3:PutObject",
"s3:PutObjectAcl",
"s3:AbortMultipartUpload"
],
"Resource": "arn:aws:s3:::<S3儲存桶名稱>/*",
"Condition": {
"StringEquals": {
"aws:SourceAccount": "<AWS帳戶號碼>"
},
"ArnLike": {
"aws:SourceArn": "arn:aws:inspector2:ap-southeast-1:<AWS帳戶號碼>:report/*"
}
}
}
]
}
{
"Version": "2012-10-17",
"Id": "key-consolepolicy-3",
"Statement": [
{
"Sid": "Allow Amazon Inspector to use the key",
"Effect": "Allow",
"Principal": {
"Service": "inspector2.amazonaws.com"
},
"Action": [
"kms:Decrypt",
"kms:GenerateDataKey*"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:SourceAccount": "<AWS帳戶號碼>"
},
"ArnLike": {
"aws:SourceArn": "arn:aws:inspector2:ap-southeast-1:<AWS帳戶號碼>:report/*"
}
}
},
{
"Sid": "Enable IAM User Permissions",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<AWS帳戶號碼>:root"
},
"Action": "kms:*",
"Resource": "*"
},
{
"Sid": "Allow access for Key Administrators",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<AWS帳戶號碼>:role/aws-service-role/inspector2.amazonaws.com/AWSServiceRoleForAmazonInspector2"
},
"Action": [
"kms:Create*",
"kms:Describe*",
"kms:Enable*",
"kms:List*",
"kms:Put*",
"kms:Update*",
"kms:Revoke*",
"kms:Disable*",
"kms:Get*",
"kms:Delete*",
"kms:TagResource",
"kms:UntagResource",
"kms:ScheduleKeyDeletion",
"kms:CancelKeyDeletion",
"kms:RotateKeyOnDemand"
],
"Resource": "*"
},
{
"Sid": "Allow use of the key",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<AWS帳戶號碼>:role/aws-service-role/inspector2.amazonaws.com/AWSServiceRoleForAmazonInspector2"
},
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "*"
},
{
"Sid": "Allow attachment of persistent resources",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<AWS帳戶號碼>:role/aws-service-role/inspector2.amazonaws.com/AWSServiceRoleForAmazonInspector2"
},
"Action": [
"kms:CreateGrant",
"kms:ListGrants",
"kms:RevokeGrant"
],
"Resource": "*",
"Condition": {
"Bool": {
"kms:GrantIsForAWSResource": "true"
}
}
}
]
}
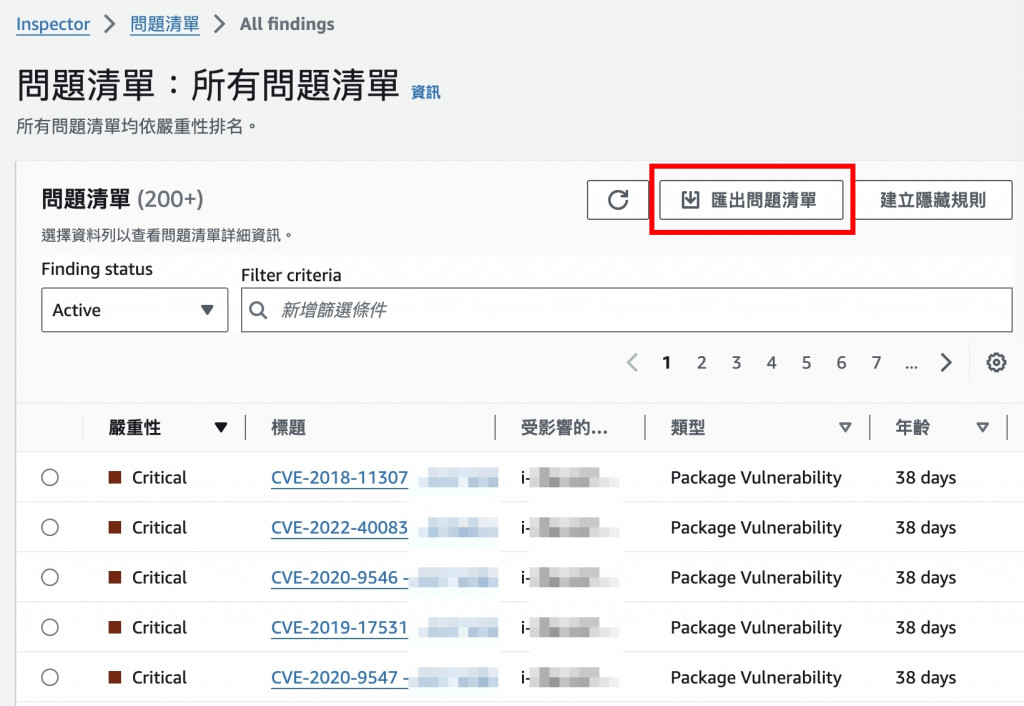
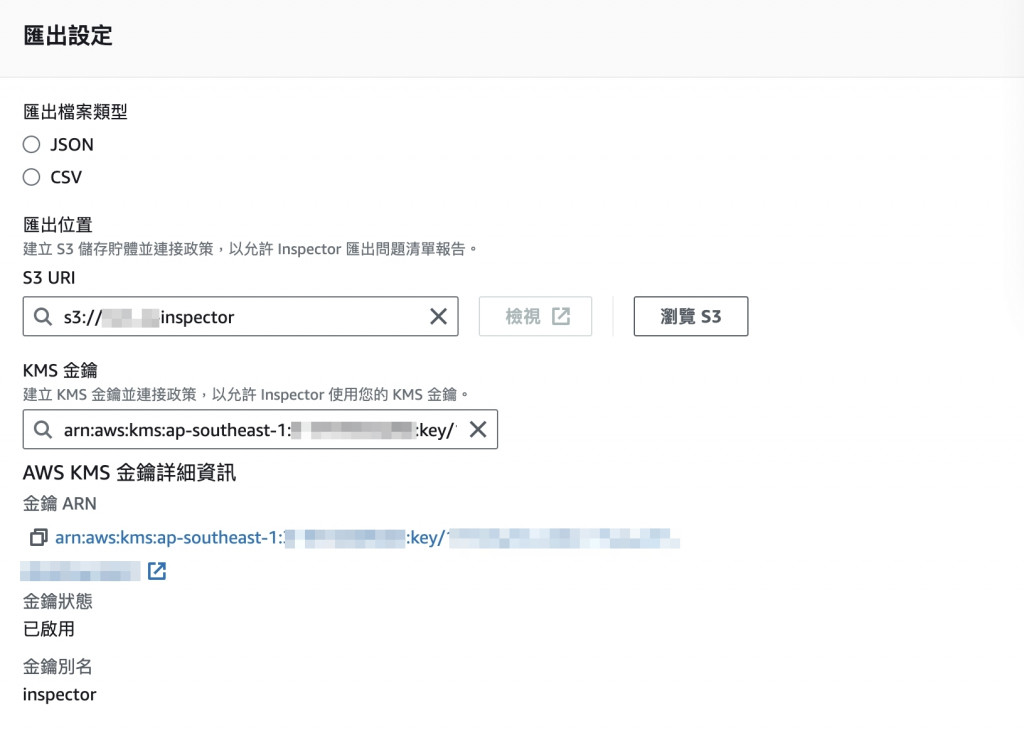
辛苦了,在三者打通之後就能查看產出的報告
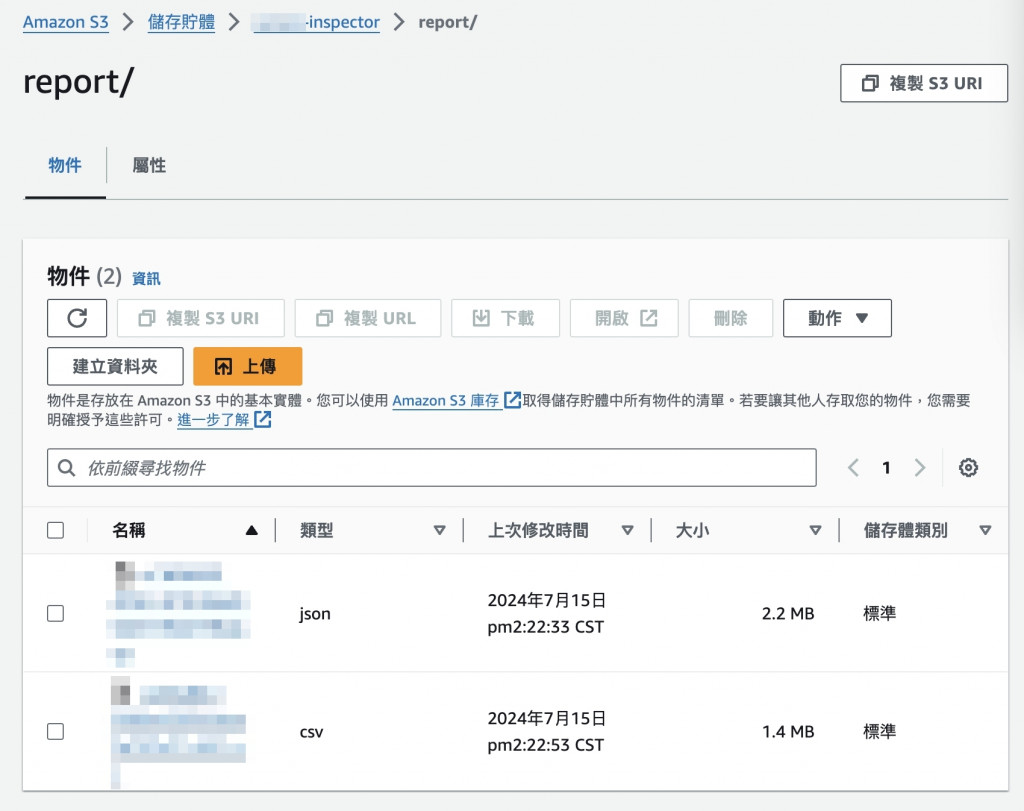
json格式
csv格式