Snort 這類IDS/IPS為了傳輸效能,通常比對沒問題就放行了,因此針對網站等服務就有WAF來進行應用層行為偵測阻擋
攻擊方使用base64編碼,讓Snort規則無法偵測
sqlmap -u "http://192.168.190.140/vulnerabilities/sqli/?id=1&Submit=Submit" --cookie="PHPSESSID=02i0f0vqse9t37qlusttllvta3; security=low" -v 4 -tamper base64encode
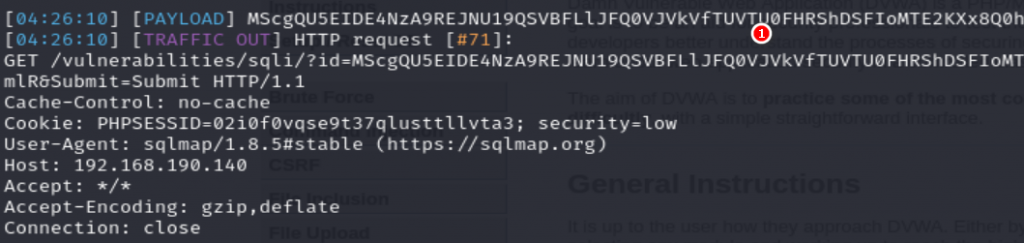
(1)access.log紀錄都是編碼過的資訊,忽略掉sqlmap的tag(攻擊者可以修改掉)無法直接發現問題
(2)Snort未偵測攻擊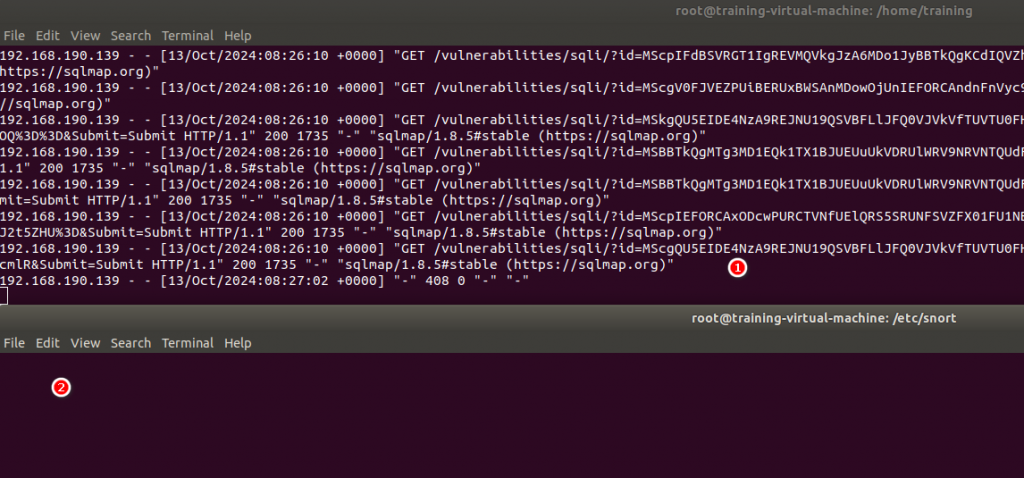
OWASP Coraza 是一個 golang 企業級 Web 應用防火牆框架,之前相應的OpenSource是Modsecurity,Modsecurity有公告EOS了,因此試著換Coraza,兩個產品規則都是用OWASP CRS(a set of generic attack detection rules for use with ModSecurity or compatible web application firewalls)
建立一個docker-compose.yml
docker-compose up 啟動
version: '3.8'
services:
dvwa:
image: vulnerables/web-dvwa
networks:
- dvwa
## Coraza WAF running on Caddy
caddy:
image: gbe0/coraza:latest
depends_on:
- dvwa
networks:
- dvwa
ports:
- "80:80"
environment:
- CADDY_REVERSE_PROXY=dvwa:80
- CORAZA_SECRULEENGINE=On
## Networks used by the above services
networks:
## Basic network used for the containers
dvwa:
網頁輸入攻擊指令,偵測並阻擋(網頁無回應),後端access.log 沒紀錄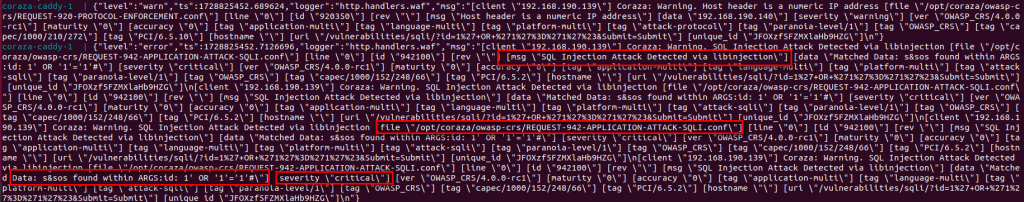
SQLMAP 使用 tamper base64encode,一下就被阻擋了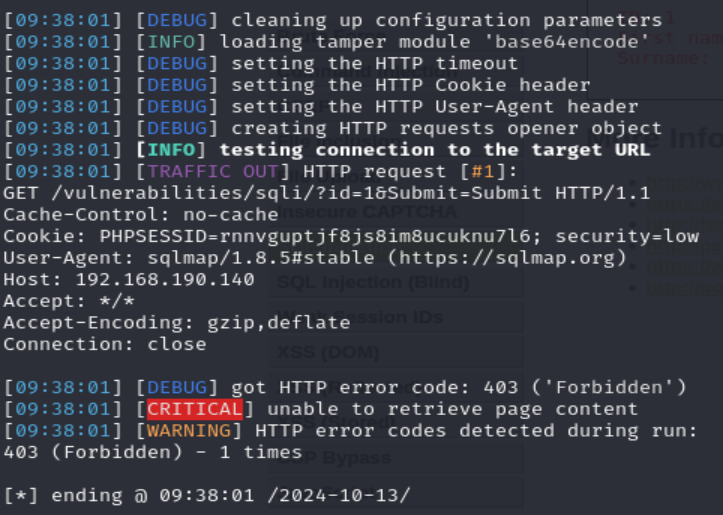
Coraza 阻擋(REQUEST-913-SCANNER-DETECTION.conf)紀錄偵測 User-agent是sqlmap阻擋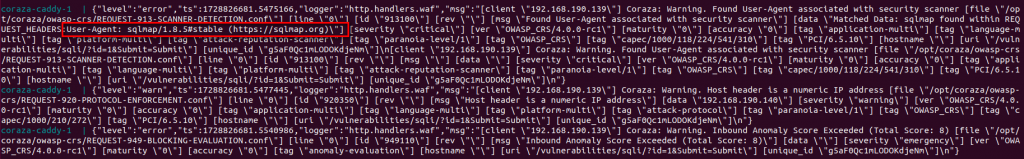
把scanners-user-agents.data的sqlmap刪掉 (裡面有將近70多個掃描工具名稱)
重啟Coraza再打一次sqlmap tamper base64encode,這次沒有偵測及阻擋
官網說明有base64Decode的模組,我們需要解編譯後再比對規則
https://coraza.io/docs/seclang/transformations/
參考https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/369 解碼非常耗資源,且容易誤判,攻擊方可以用編碼再編碼的方式再次繞過,最好的方式還是修補程式,減少可被利用的破口
Tips and Tricks for Effective SQL Injection Testing using SQLMap Tamper Scripts
https://muhdaffa.medium.com/tips-and-tricks-for-effective-sql-injection-testing-using-sqlmap-tamper-scripts-ed4bfa5717e7
sqlmapproject/sqlmap
https://github.com/sqlmapproject/sqlmap/tree/master/tamper
kh4sh3i/WAF-Bypass
https://github.com/kh4sh3i/WAF-Bypass
OSS WAF stack using Coraza, Caddy, and Elastic
https://medium.com/@jptosso/oss-waf-stack-using-coraza-caddy-and-elastic-3a715dcbf2f2
SQLMap - CheatSheet
https://book.hacktricks.xyz/pentesting-web/sql-injection/sqlmap
