檢查異狀最簡單的方式就是用比對法,這章重點將設定檔複製出來,每日做比對。
The more you know the machine in its clean state, the more chances you have to detect any fraudulent activity running from it.
參考
https://cert.tanet.edu.tw/pdf/Windows.pdf
TACERT 臺灣學術網路危機處理中心
原文出處:
https://github.com/certsocietegenerale/IRM/blob/master/EN/IRM-2-WindowsIntrusion.pdf
[A]DNSnetsh dump
[C]Accountnet localgroup administrators
[A]Firewallnetsh advfirewall firewall show rule name=all
[A]Processtasklist
[A]Servicenet start
[A]Portnetstat -n |find /V "127.0.0.1"
[A]netusenet usenet view \\127.0.0.1
[A]schtasksschtasks
[I]Eventwevtutil qe Application /q:"*[System[TimeCreated[@SystemTime>='2018-10-09T00:00:00' and @SystemTime<'2018-10-10T00:00:00']]]" /f:text
每日比對FC
開機執行
RUN => shell:startup
時間不夠自己寫幾個script測試,有空再回來整理成工具
檢查原則分析程式工具
Microsoft Security Compliance Toolkit
https://docs.microsoft.com/zh-tw/windows/security/threat-protection/security-compliance-toolkit-10
policy比對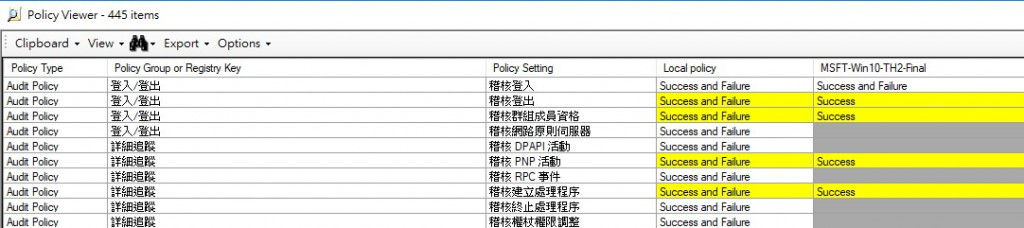
Microsoft Security Guidance blog
https://blogs.technet.microsoft.com/secguide/
