這章針對CVE-2020-1472這類攻擊,試著用各種監控、防護手段去阻擋
首先評估可能可以偵測的方法有:
在多天以前從各大討論區、IThome開始警告有該漏洞,提醒先做好Windows到8月份的更新。
Windows重大漏洞Zerologon可讓駭客輕易掌控AD網域
https://www.ithome.com.tw/news/140014
Zerologon – hacking Windows servers with a bunch of zeros
https://nakedsecurity.sophos.com/2020/09/17/zerologon-hacking-windows-servers-with-a-bunch-of-zeros/
根據情資資訊,開始建立第二層防護 - 監控。
因為是透過網路進行攻擊的,通常會先試著從Snort等分析著手看看是否能偵測
從攻擊測試工具(https://github.com/dirkjanm/CVE-2020-1472)中,錄下封包
參考網路資訊 https://twitter.com/TalBeerySec/status/1306587772640083971 下filter
(ntlmssp.neg_flags.na8000000 == 0) && (netlogon.clientcred[0:7] == 00:00:00:00:00:00:00)
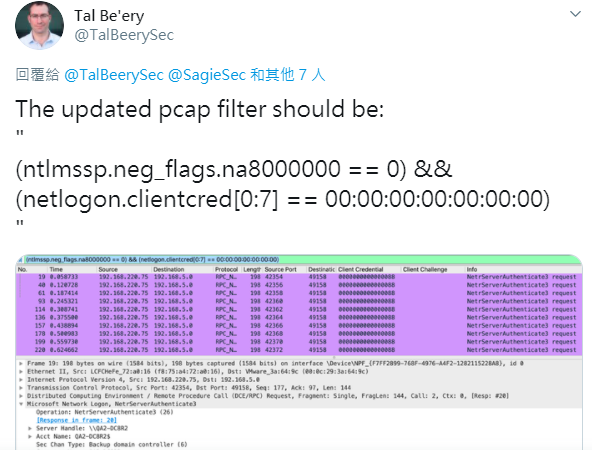
Filter下 rpc_netlogon會看到很多NetrServerAuthenticate跟NetServerReqChallenge的封包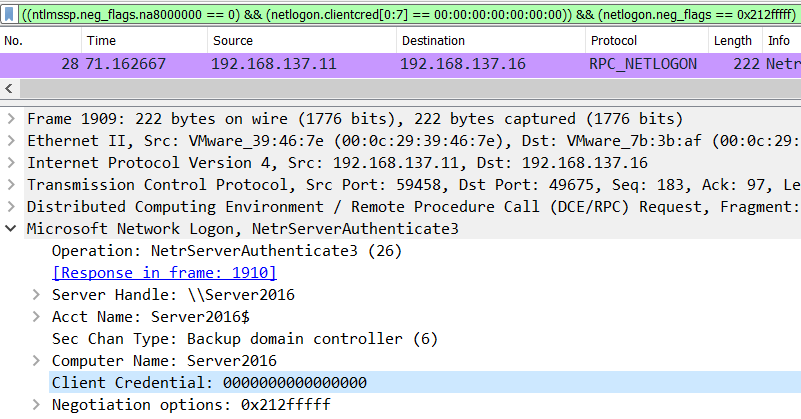
((ntlmssp.neg_flags.na8000000 == 0)
參考https://www.wireshark.org/docs/dfref/r/rpc_netlogon.html
Protocol field name: rpc_netlogon
FIELD NAME: ntlmssp.neg_flags.na8000000
DESCRIPTION: Authenticated RPC
(netlogon.clientcred[0:7] == 00:00:00:00:00:00:00))
參考 https://www.wireshark.org/docs/dfref/r/rpc_netlogon.html
Protocol field name: rpc_netlogon
FIELD NAME: netlogon.clientcred
DESCRIPTION: Client Credential
(netlogon.neg_flags == 0x212fffff)
觀察到都有這個flags我就加進去
可以將濾出的封包存成pcap檔,之後可以重送到snort確定規則是否OK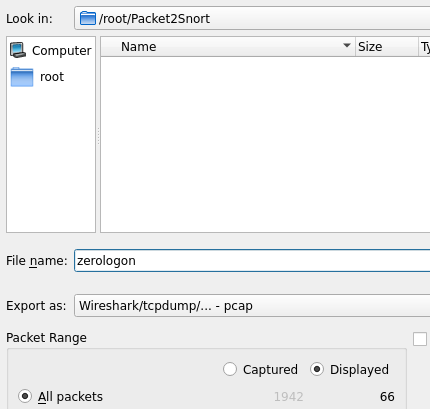
參考: https://github.com/bhdresh/SnortRules/blob/master/Exploit/CVE-2020-1472.rules
拿剛的pcap放到snort去偵測
snort.exe -c C:\Snort\etc\snort.conf -r zerologon.pcap
沒有跳Alert訊息出來,只好先自己重寫一個簡單規則試試,首先根據之前封包的特徵做比對
alert tcp any any -> any any (msg: "CVE-2020-1472 (zerologon)"; sid:10011; content:"|00 00 00 00 00 00 00 bf bf ff ff 2f 21|";)
修改後有偵測到訊息了,證明工具沒問題,繼續一條條規則增加上去(越多的比對會消耗資源,且容易漏報,但太少會誤報,為了避免告警疲乏,規則設嚴謹一點)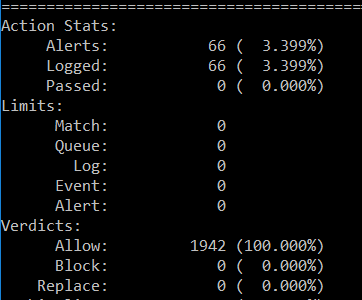
修了幾個判斷後,能正常運行了
alert tcp any any -> any any (msg: "Potential exploit attempt to CVE-2020-1472 (zerologon)"; sid:10011; content:"|05 00 00 03|"; offset: 0; depth:4; content:"|10 00 00 00|"; distance:0; depth:50; content:"|5C 00 5C 00|"; distance:0; content:"|24 00 00 00|";distance:0; content:"|00 00 00 00 00 00 00 bf bf ff ff 2f 21|";distance:0; reference: url, https://github.com/dirkjanm/CVE-2020-1472;)
