接續上一章,寫出規則,並開始監控一段時間後,收到了新的情資,該漏洞被武器化了,搭配Mimikatz 並將流量加密,之前的規則已經偵測不到了。
三秒入侵 Windows AD:Zerologon 災難級漏洞的完整解析
https://medium.com/cycraft/cve-2020-1472-zerologon-aa24b97e3fe2
實作用mimikatz打Zerologon的攻擊封包Authenticate部分已經加密了,之前的Rule 偵測不到該行為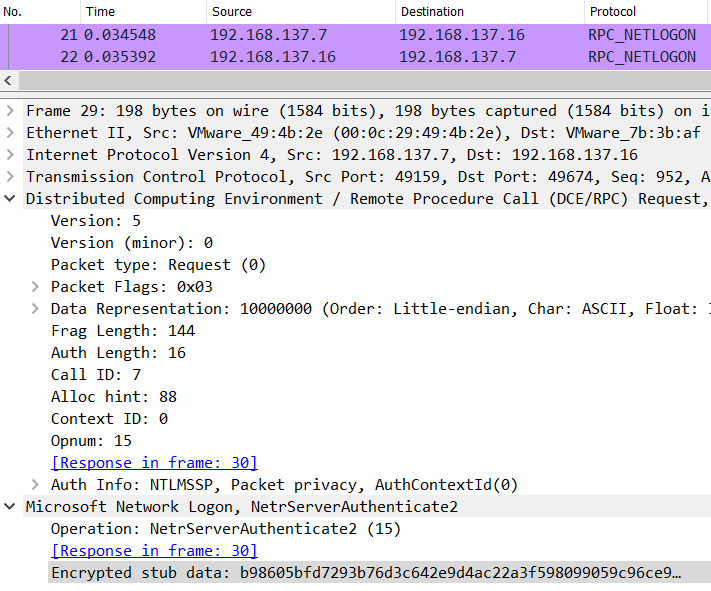
網路上已經有分享Rule,這邊就不再重複說明,然而駭客有意去改寫單純用Snort Rule就很難偵測到
Mimikatz CVE-2020-1472 Zerologon snort suricata
https://gist.github.com/silence-is-best/435ddb388f872b1a2e332b6239e9150b
換個角度,從受害端電腦一定有蛛絲馬跡可循,這邊重建一台Server2016為受害的主機,清空Eventlog,試著發送攻擊。
Security EvenID 4624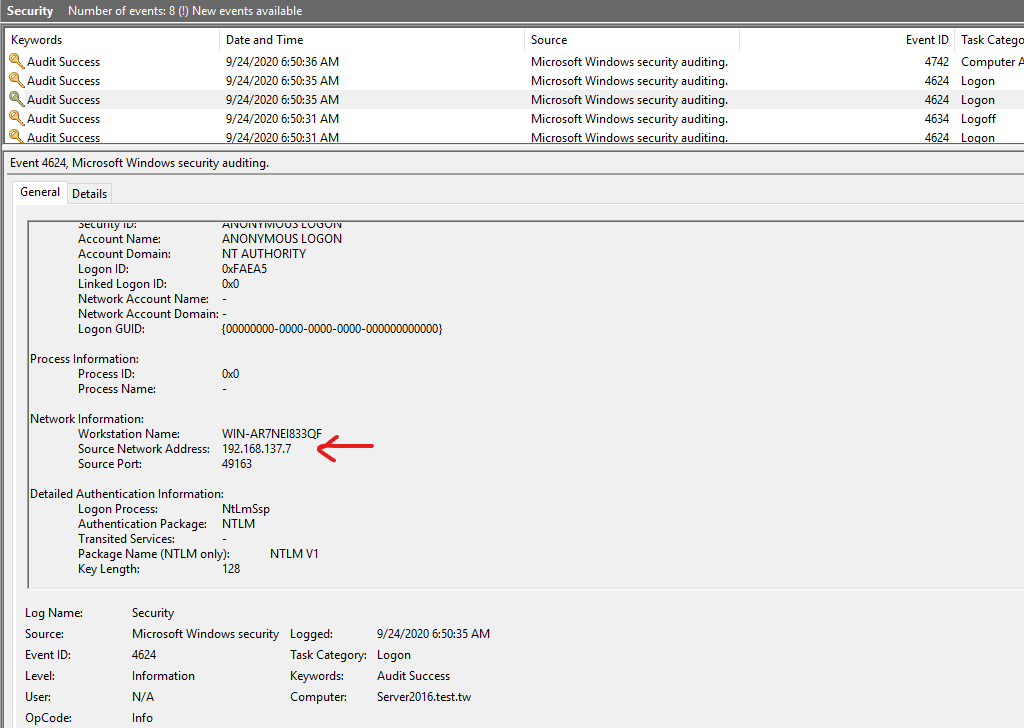
其中有匿名登錄的異常行為,並且看到攻擊端的IP
New Logon:
Security ID: ANONYMOUS LOGON
Account Name: ANONYMOUS LOGON
Account Domain: NT AUTHORITY
Security EventID 4742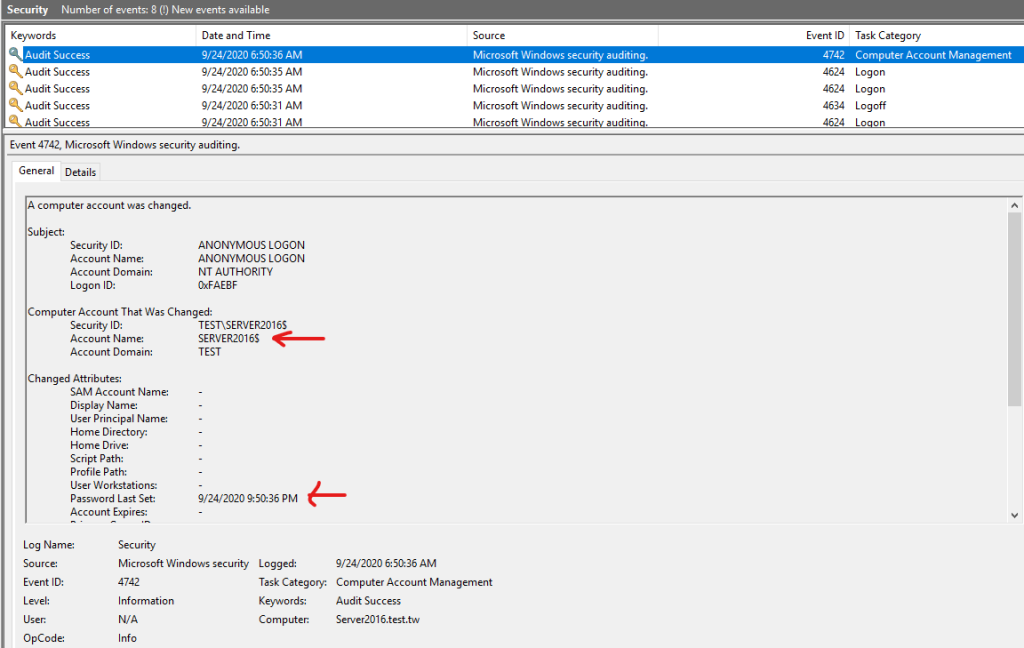
DC帳號更改密碼的異常行為
Computer Account That Was Changed:
Security ID: TEST\SERVER2016$
Account Name: SERVER2016$
Account Domain: TEST
Changed Attributes:
Password Last Set: 9/24/2020 9:50:36 PM
根據上面觀察到的兩個現象,可以設定規則去監控
(EvenID:4624) AND (Account_Name:"ANONYMOUS LOGON")
(EvenID:4742) AND (Account_Name:"ANONYMOUS LOGON") AND "Computer Account That Was Changed"
在分析途中,關鍵字拿去Google問可以獲得許多分享出來的偵測方式
from-lares-labs-defensive-guidance-for-zerologon這篇文章就是利用相同方式寫Splunk Rule去偵測
https://www.lares.com/blog/from-lares-labs-defensive-guidance-for-zerologon-cve-2020-1472/
