延續前一篇 「Shift Left」 的概念,SAST 是最常見的左移實踐之一。
在程式碼提交階段就進行安全檢查,可以提前發現漏洞。
為什麼要在 CI Pipeline 中自動化?
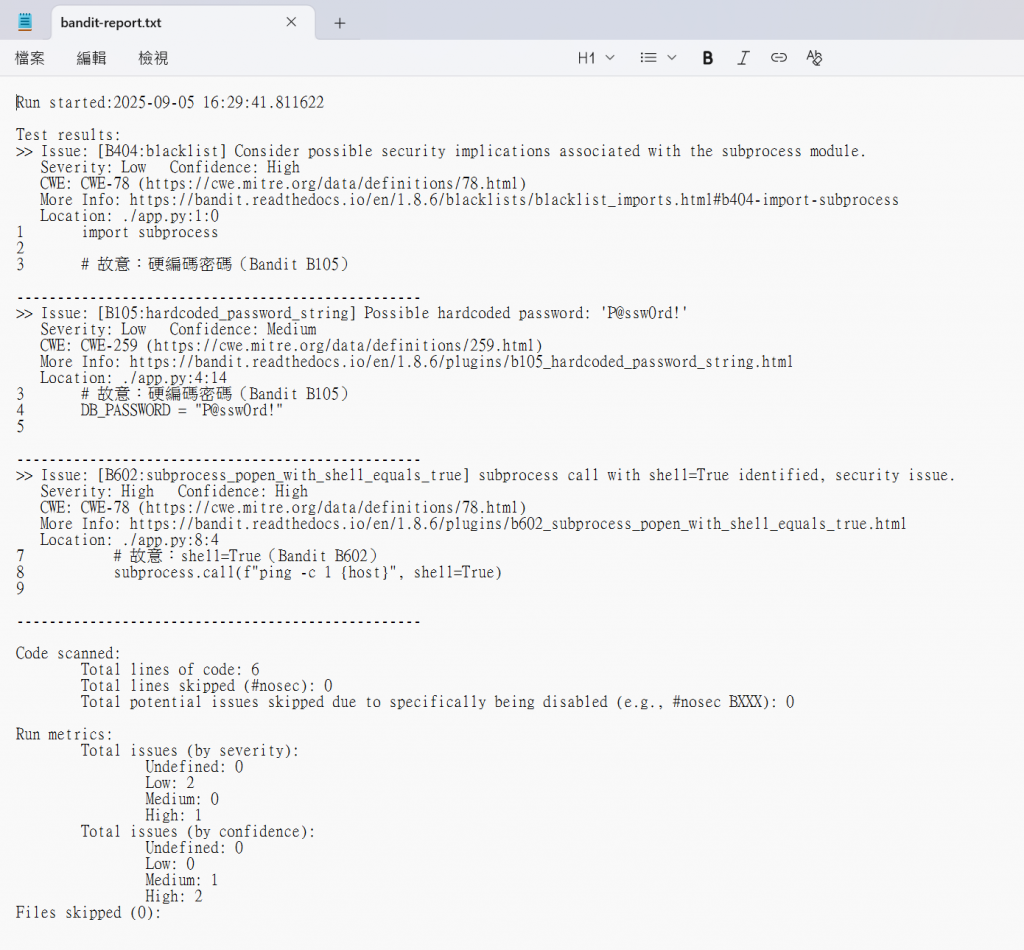
🔍 能檢測的問題:
✅ 優勢:快、能融入開發流程
❌ 限制:可能有誤報,無法檢測執行時的漏洞
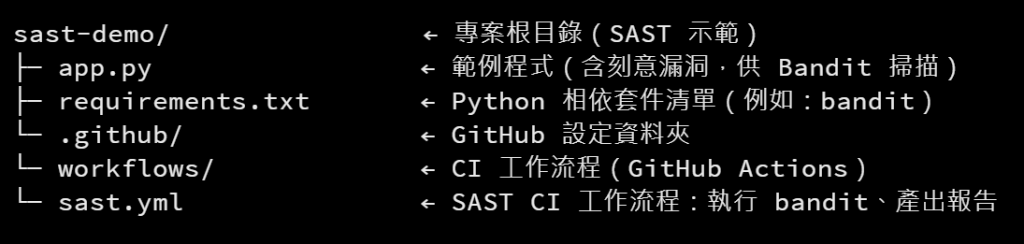
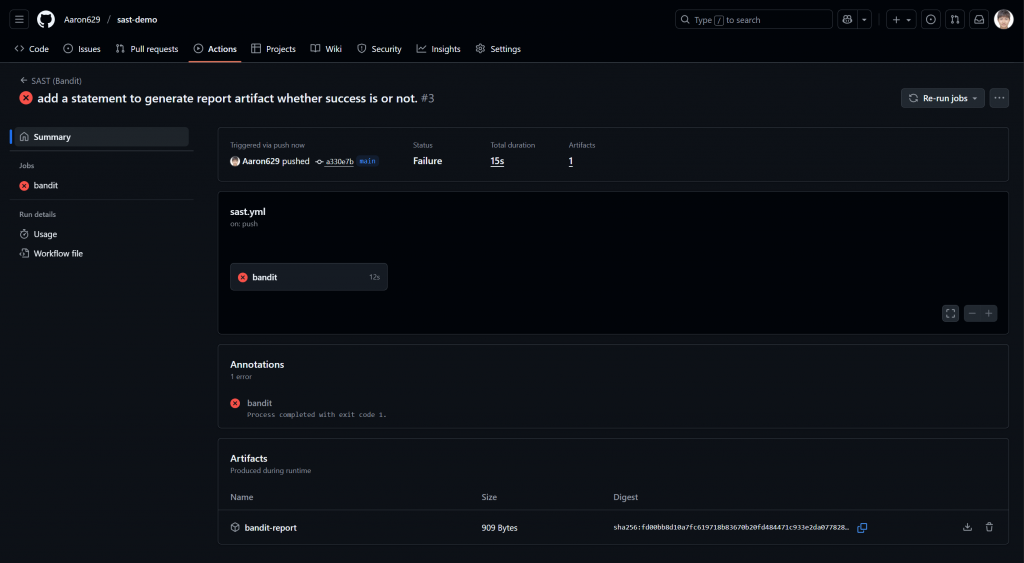
在 GitHub Actions Pipeline 中整合 SAST 工具(例如:Bandit):
import subprocess
# 故意:硬編碼密碼(Bandit B105)
DB_PASSWORD = "P@ssw0rd!"
def ping(host: str):
# 故意:shell=True(Bandit B602)
subprocess.call(f"ping -c 1 {host}", shell=True)
if __name__ == "__main__":
ping("127.0.0.1")
name: SAST (Bandit)
on:
push:
pull_request:
jobs:
bandit:
runs-on: ubuntu-latest
steps:
- name: Checkout
uses: actions/checkout@v4
- name: Setup Python
uses: actions/setup-python@v5
with:
python-version: '3.12'
- name: Install Bandit
run: |
python -m pip install --upgrade pip
pip install bandit
# 只掃 app.py(最小可行示範)
- name: Run Bandit (single file)
run: bandit app.py -f txt -o bandit-report.txt
- name: Upload report artifact
if: always()
uses: actions/upload-artifact@v4
with:
name: bandit-report
path: bandit-report.txt
bandit
👉指令 : pip install -r requirements.txt