各位IT的先進好:
目前我們mailserver環境為postfix+Mailsanner+sapmassain,最近常收到一種比特幣的詐騙信,覺得很疑惑,煩請知道的人幫我釋疑,我在postfix main.cf上有設定以下限制,理論上對方如果假冒我們網域寄信來應該會直接被丟棄。
smtpd_sender_restrictions = permit_mynetworks,
permit_sasl_authenticated,
**check_sender_access hash:/etc/postfix/check_sender**
check_sender內容為mail.example.com DISCARD
但是奇怪的是,user收下後發現寄件者是他自己,我看一下mail擋頭有兩個from,但不知道為何user端是顯示下面一組假冒的email,但我實際上又複查maillog,當時寄件進來的是第一組真實的from位址,所以才沒被上面限制所擋下,我很疑惑如何產生第二組假冒的from email,又該如何防堵呢?
郵件擋頭
From camille.voisin@radiopole-artois.com 實際寄信位址 Sun May 5 19:51:31 2019
Return-Path: <camille.voisin@radiopole-artois.com>
X-Spam-Status: Yes
X-example-MailScanner-From: camille.voisin@radiopole-artois.com
X-example-MailScanner-SpamScore: sssssssssssssss
X-example-MailScanner-SpamCheck: spam, SpamAssassin (not cached,
score=15.198, required 5, FORGED_MUA_MOZILLA 1.60,
HEADER_FROM_DIFFERENT_DOMAINS 5.00, HTML_IMAGE_ONLY_04 0.34,
HTML_MESSAGE 0.00, LOCALPART_IN_SUBJECT 0.73, MIME_HTML_MOSTLY 0.00,
MPART_ALT_DIFF 0.72, RCVD_IN_BL_SPAMCOP_NET 1.25,
RCVD_IN_DNSWL_NONE -0.00, RCVD_IN_SBL_CSS 3.56,
TO_NO_BRKTS_HTML_IMG 2.00)
X-example-MailScanner: Found to be clean
X-example-MailScanner-ID: A5E8940ED698.A2F81
X-example-MailScanner-Information: Scaned by mail.example.com
Received: from webmail.radiopole-artois.com (radiopole-artois.com [92.103.138.147])
(using TLSv1.2 with cipher AECDH-AES256-SHA (256/256 bits))
(No client certificate requested)
by mail.example.com (Postfix) with ESMTPS id A5E8940ED698
for <user1@mail.example.com>; Sun, 5 May 2019 19:50:46 +0800 (CST)
DKIM-Filter: OpenDKIM Filter v2.11.0 mail.example.com A5E8940ED698
Received: from localhost (localhost [127.0.0.1])
by webmail.radiopole-artois.com (Postfix) with ESMTP id 584FF37AB22
for <user1@mail.example.com>; Sun, 5 May 2019 13:29:14 +0200 (CEST)
Received: from webmail.radiopole-artois.com ([127.0.0.1])
by localhost (webmail.radiopole-artois.com [127.0.0.1]) (amavisd-new, port 10032)
with ESMTP id UpWpT5P9WE86 for <user1@mail.example.com>;
Sun, 5 May 2019 13:29:14 +0200 (CEST)
Received: from localhost (localhost [127.0.0.1])
by webmail.radiopole-artois.com (Postfix) with ESMTP id 3F4CD37A98A
for <user1@mail.example.com>; Sun, 5 May 2019 13:29:14 +0200 (CEST)
X-Virus-Scanned: amavisd-new at webmail.radiopole-artois.com
Received: from webmail.radiopole-artois.com ([127.0.0.1])
by localhost (webmail.radiopole-artois.com [127.0.0.1]) (amavisd-new, port 10026)
with ESMTP id n1WSP56lQp_M for <user1@mail.example.com>;
Sun, 5 May 2019 13:29:13 +0200 (CEST)
Received: from [85-192-163-151.dsl.esoo.ru] (85-192-163-151.dsl.esoo.ru [85.192.163.151])
by webmail.radiopole-artois.com (Postfix) with ESMTPSA id DE856379F69
for <user1@mail.example.com>; Sun, 5 May 2019 13:29:05 +0200 (CEST)
From: <user1@mail.example.com> <--被假冒的位址,並會顯示在outlook寄件者上
X-aid: 3501491858
Errors-To: update+6yz8bu0be@radiopole-artois.com
Content-Type: multipart/related;
boundary="elgunmdruh-E01AD30BC3700B170D9-gqkrhyrzxe-3D501A5C5C397-qgqhontzg-08E67D"
MIME-Version: 1.0
To: user1@mail.example.com
X-Priority: Critical
maillog內容,postfix記錄的是camille.voisin@radiopole-artois.com寄給user1@mail.example.com,所以才沒被擋下
May 5 19:50:45 mail postfix/smtpd[4808]: connect from radiopole-artois.com[92.103.138.147]
May 5 19:50:46 mail postfix/smtpd[4808]: Anonymous TLS connection established from radiopole-artois.com[92.103.138.147]: TLSv1.2 with cipher AECDH-AES256-SHA (256/256 bits)
May 5 19:50:46 mail postfix/smtpd[4808]: A5E8940ED698: client=radiopole-artois.com[92.103.138.147]
May 5 19:50:46 mail postfix/cleanup[4814]: A5E8940ED698: hold: header Received: from webmail.radiopole-artois.com (radiopole-artois.com [92.103.138.147])??(using TLSv1.2 with cipher AECDH-AES256-SHA (256/256 bits))??(No client certificate requested)??by mail.example.com from radiopole-artois.com[92.103.138.147]; from=<camille.voisin@radiopole-artois.com> to=<user1@mail.example.com> proto=ESMTP helo=<webmail.radiopole-artois.com>

像這個 Header 解析程式, 就是把後面的 From 覆蓋前面, 所以只會顯示最後面那個 From:
MXToolbox: Header Analyzed
順便一提, 從上面的分析可以看到, 發送者的主機 address 是被列入 black list 的:
85-192-163-151.dsl.esoo.ru 85.192.163.151
webmail.radiopole-artois.com 92.103.138.147
所以你可以嘗試在 Postfix 裡面加入 RBL 的黑名單判斷, 輔助阻擋這類信件: How-To: Fight SPAM with Postfix RBL, 但因很多企業郵件主機的管理員, 並沒有妥善管理自己 Email Server 的黑名單 Reputation, 所以採用 RBL 的時候, 常常會因為誤判而阻擋了正常的企業郵件, 不過這可以搭配白名單機制, 將有往來的企業網域排除掉 RBL檢查...
---- 我是分隔線 ---
我剛注意到: 你第一個 From 後面沒有冒號 :
請問是您不小心拿掉的? 還是原本就沒有?
如果原本就沒有的話, 那上面的分析就不正確, 因為只有 From: 才是有效的 Header, From 不是. 但有可能 Postfix 會誤吃第一個 From, 忽略第二個....
感謝前輩的回答!
1.我再看一下mail擋頭,我發現有一點很奇怪,就是我從webmin直接看信時,有第一行From camille.voisin@radiopole-artois.com,的確是沒有加:,但是outlook收下後,第一行不見了,但在webmin及outlook的寄件者是假冒的user1@mail.example.com
2.本地端的擋頭不是應該是由我這端的postfix加上,排除被入侵的可能,如果是經由本地user認證的,會加認證user在擋頭,遠端應該不能任意變造吧,我的疑問是postfix log記錄的是camille.voisin@radiopole-artois.com,為何在擋頭那沒有加上正確的,第二假冒的user1@mail.example.com是遠端就傳送假冒的data這樣的緣故嗎?
3.感謝提供RBL的建議,當初沒設上是因為RBL主機可能因不穩或缺少維護或誤擋,目前防火牆有一層過濾加上spamassassin的規則設比較嚴,目前都有抓到,但我還是想知道確切的原因。
raytracy大神,
我看到一篇文章如下:
The "really from" address comes from the "from:" dialog in the SMTP conversation.
The "fake from" comes from exploiting the common practice in email clients of displaying the various header fields as laid out in the Data portion of the SMTP conversation.
If you had left out the "from:" and "to:" lines in the Data portion, it would have displayed the actual envelope sender and recipient.
我在想上述那封fake email是不是這樣產生的。
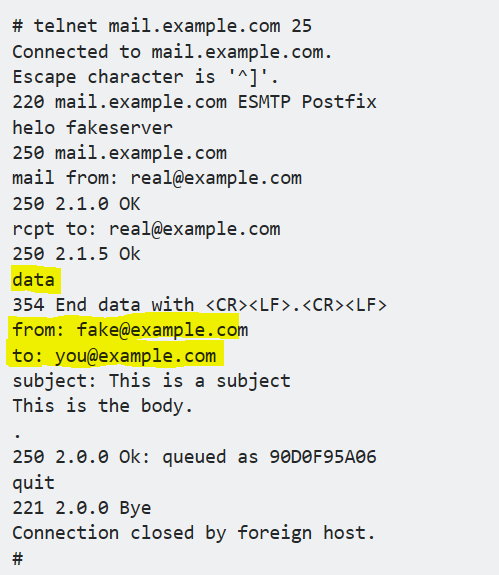
沒錯, 我要說的就是這個狀況...