設備: FortiGate 90D
韌體: v6.0.6 build0272 (GA)
我家裡有一台二手的FortiGate,目前想讓朋友(外部)連VPN,
可以一起用遊戲的區網連線一起玩遊戲。
但目前在家裡內部區網都搜尋得到房間,但朋友怎樣都看不到。
本身是碼農對網路設備沒有這麼熟,有些抓包技巧不太會
只熟自己的linux +php +apache +js +一點點python
可能要讓各位大神見笑了
所以感覺基本的VPN設定跟政策應該沒有什麼大問題
但不知道是不是VPN狀況下有什麼封包被擋了,
不知道會不會是有用到udp 或是 廣播封包被丟棄?
推測遊戲尋找房間的時候應該會先發廣播(不知道有沒有被丟了)
之後查找指定的UDP或TCP PORT(不知道有沒有被擋住)
開房的遊戲也會對VPN的電腦做交握?(不知道VPN端的電腦有沒有可能被擋)
FortiGate 192.168.100.1
外部電腦VPN 192.168.100.230
內部電腦 192.168.100.150
id=20085 trace_id=233 func=print_pkt_detail line=5452 msg="vd-root received a packet(proto=17, 192.168.100.230:42804->255.255.255.255:42805) from ssl.root. "
id=20085 trace_id=233 func=init_ip_session_common line=5611 msg="allocate a new session-0288bca5"
id=20085 trace_id=233 func=vf_ip4_route_input line=1604 msg="find a route: flags=90000000 gw-255.255.255.255 via root"
id=20085 trace_id=233 func=fw_local_in_handler line=400 msg="iprope_in_check() check failed on policy 0, drop"
id=20085 trace_id=399 func=print_pkt_detail line=5452 msg="vd-root received a packet(proto=6, 192.168.100.150:7070->192.168.100.1:22725) from internal. flag [.], seq 3307694761, ack 3721327633, win 1024"
id=20085 trace_id=399 func=resolve_ip_tuple_fast line=5527 msg="Find an existing session, id-0288b382, reply direction"
id=20085 trace_id=399 func=__ip_session_run_tuple line=3292 msg="DNAT 192.168.100.1:22725->192.168.100.230:22725"
id=20085 trace_id=399 func=npu_handle_session44 line=921 msg="Trying to offloading session from internal to ssl.root, skb.npu_flag=00000400 ses.state=01000200 ses.npu_state=0x00040000"
id=20085 trace_id=399 func=__ip_session_run_tuple line=3329 msg="run helper-rtsp(dir=reply)"
id=20085 trace_id=400 func=print_pkt_detail line=5452 msg="vd-root received a packet(proto=6, 192.168.100.230:22725->192.168.100.150:7070) from ssl.root. flag [.], seq 3721327780, ack 3307694761, win 32760"
id=20085 trace_id=400 func=resolve_ip_tuple_fast line=5527 msg="Find an existing session, id-0288b382, original direction"
id=20085 trace_id=400 func=npu_handle_session44 line=921 msg="Trying to offloading session from ssl.root to internal, skb.npu_flag=00000400 ses.state=01000200 ses.npu_state=0x00040000"
id=20085 trace_id=400 func=__ip_session_run_tuple line=3278 msg="SNAT 192.168.100.230->192.168.100.1:22725"
id=20085 trace_id=400 func=__ip_session_run_tuple line=3329 msg="run helper-rtsp(dir=original)"
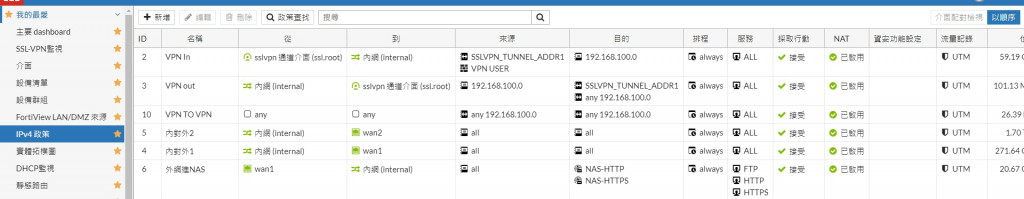

SSL VPN 進來的介面叫 ssl.root
內部電腦的走的是 internal
假設遊戲只能在 同個網段裡面找到房間
那實際上你們就在不同網段,就算你靠 NAT 弄成同樣192.168.100.x 的 IP
最簡單的做法 你在內網一樣連 SSLVPN 就解決了
建議你提供一下是哪款遊戲
看能不能清楚他遊戲房間搜尋模式,才做出對應的設定
根據遊戲需求環境解說如下:
Common Multiplayer Issues and Solutions:
This is a technology that allows an application (like Grim Dawn) to communicate with your router. If your router supports UPnP (most do), Grim Dawn can tell your router to allow other people to connect to your computer when you are hosting a game.
Why is this needed? Routers by default are designed to BLOCK anyone connecting to your computer. This is a security thing. You don’t want random/malicious computers connecting to your computer unless you explicitly allow it.
A port is designated by a number. In the case of Grim Dawn this number is 27016. Think of this as a phone number. As we mentioned above, a router by default is configured to say, “I’m sorry, that number is unreachable”, to anyone who tries to call you on any number. So if nothing was configured, you would host your Grim Dawn game, the game would tell Steam that you have a game ready, Steam would call you up on 27016 and your router would tell Steam, “I’m sorry, that number is unreachable”, and no game would be shown as available to anyone else.
回到Fortigate身上!
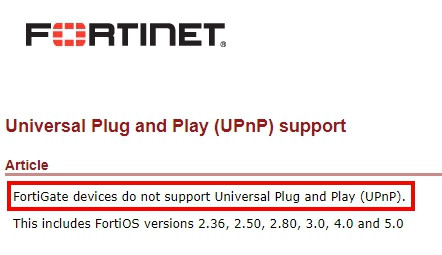
很不幸的 Fortigate並不支援 UPnP (如果有誤,請導正)
所以樓主的遊戲如果網路流量穿過Fortigate應該就會不能玩
結案!
但是UPnP正常是對外,才需要這個功能
目前我是朋友開VPN連入後
用LAN模式搜尋房間的說
正常應該是依照內網的協定才對
在我家開兩台電腦是可以互相看得到房間的
但VPN進來就是不行,才覺得奇怪
總覺得VPN進來的USER跟內網不知道哪裡被隔離開了
但就一直查不到
因為大部分的測試都是通的
樓主基本上網路觀念是比較不清楚的
對於所有SSLVPN進入的都是ssl.root介面進入
即便是由內網豋VPN也是一樣
所以網路流量必定會穿過Fortigate
故即便其他網路通訊都會通,就UPnP不能通過
原因如前述,這是不爭的事實
但是家裡開兩台電腦(這是內網)
可能有接switchhub或是在FG的switch port上
根本網路流量不需要經過Fortigate介面交換
Fortigate無從做UPnP的阻擋(不支援)
所以當然遊戲可以暢通
樓主錄的封包裡,完全沒有UPnP的通訊
等有看到(錄到)UPnP
再來判斷什麼東西擋到也不遲
是呀~雖然是碼農對coding跟server比較熟
但網路層面 還是很生疏
只知道一些皮毛
要抓包什麼的就真的很弱了
目前家裡所有網路線都是直接接在FG上面
電腦都走網路線
以前會挑90D就是因為他接口夠多XD
我要怎麼錄製UPnP的通訊呢?
抓27016 port?
我有用過
diag debug enable
diag debug flow filter dport 27016
diag debug flow trace start 100
都沒錄到東西
從我上面錄製的幾段訊息感覺
他好像用了好幾port在做不同的事情
好像會廣播問255.255.255.255:42805
好像還會用到 22725 7070
但我不知道做什麼的
開房間的電腦好像會開 22725 port
netstat 好像有看到
但不知為啥 沒看到使用 27016
還請大大多多指教
樓主誤會了
在下是認為不會有UPnP的封包
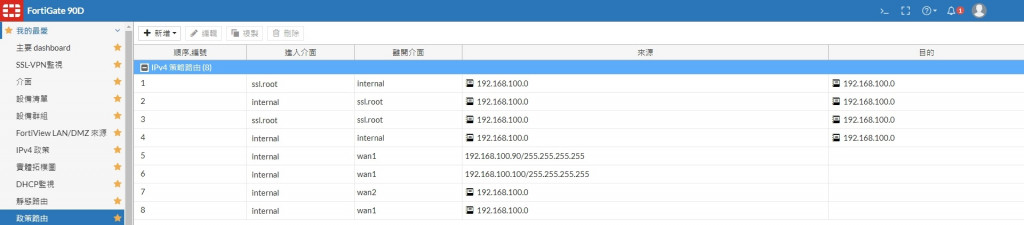
也不認為是政策路由的關係(雖然政策路由全錯)
不知道樓主怎麼能把ssl.root搞得跟internal同一個網段
(基本上應該是不可能做到,因為每個介面都應該不同網段)
(UPnP也跟27016port不是同一件事)
所以認為是Forigate不支援這個遊戲
不是防火牆擋掉了什麼通訊
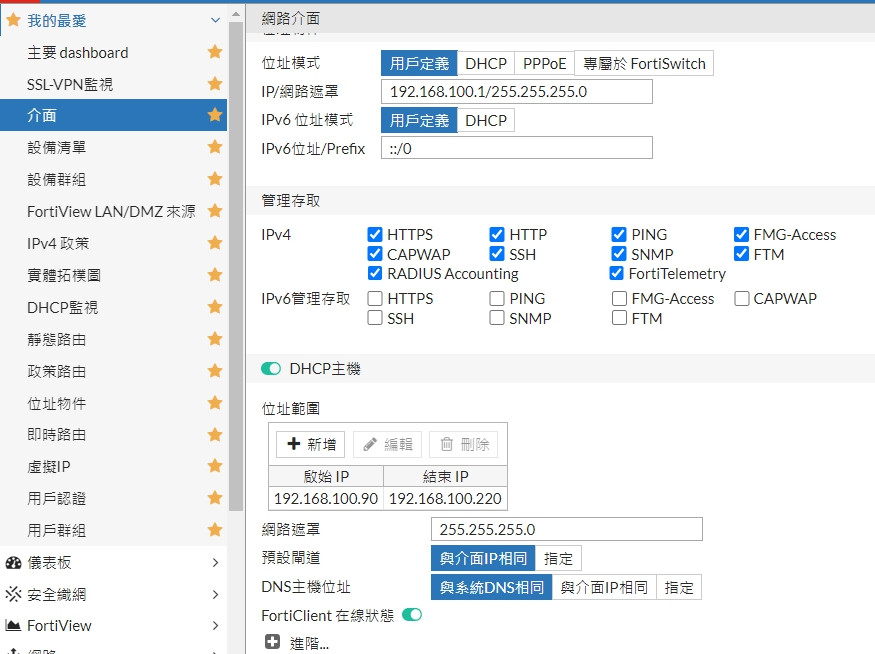
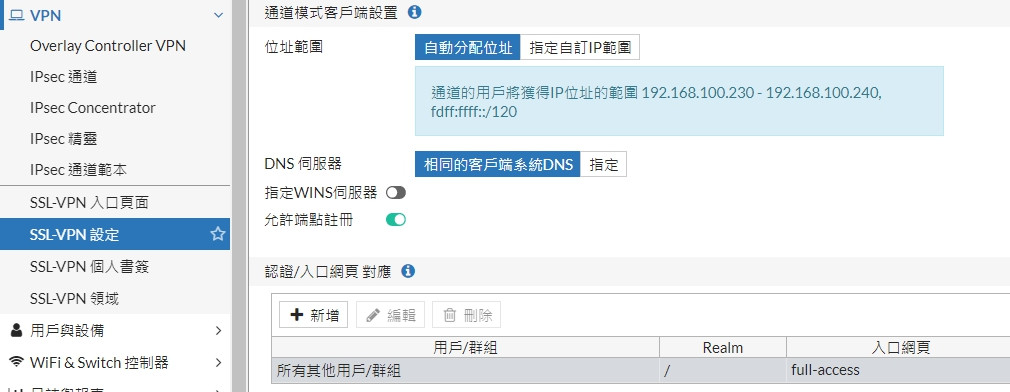
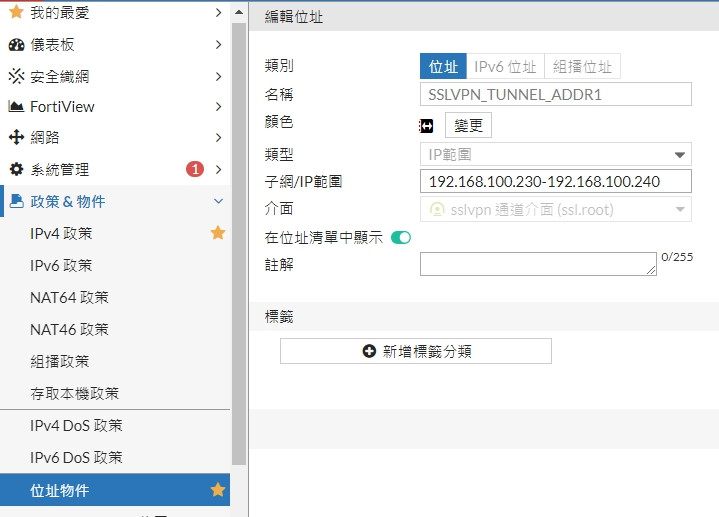
只是DHCP 192.168.100.90~192.168.100.220
VPN 在 192.168.100.230~192.168.100.240
之前我朋友叫我嘗試的,把他們擠在同一段試試
之前我曾經要用火炬之光2的區網連線
也是一樣不行的時候也是這樣
之後只好繼續用爛爛的官方伺服器(常找不到房)
今天有嘗試在內網互找房間抓包,看有什麼端倪
已經盡量濾掉一些沒用的值了
internal13 是主機房的端口 192.168.100.111
internal2 是找房間的端口 192.168.100.150
diag sniffer packet internal "host !192.168.100.104 and host !192.168.100.150 and host !192.168.100.97 and port !3389 and port !80 and port !443 and host !192.168.66" 4 0
0.846598 internal -- BPDU 'internal10' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.800a
0.956314 internal -- 192.168.100.150.8329 -> 112.121.116.204.6600: psh 3396148699 ack 2532956481
0.959903 internal -- 112.121.116.204.6600 -> 192.168.100.150.8329: psh 2532956481 ack 3396148737
1.000478 internal -- 192.168.100.150.8329 -> 112.121.116.204.6600: ack 2532956512
1.026245 internal -- arp who-has 192.168.100.200 tell 192.168.100.1
1.026555 internal -- arp reply 192.168.100.200 is-at 28:6c:7:5e:45:ed
1.065813 internal -- arp who-has 192.168.100.92 tell 192.168.100.108
1.075809 internal -- arp who-has 192.168.100.154 tell 192.168.100.108
1.402110 internal -- arp who-has 192.168.100.1 tell 192.168.100.96
1.402261 internal -- arp reply 192.168.100.1 is-at 8:5b:e:3d:c5:6c
1.752317 internal -- 192.168.100.150.56355 -> 168.95.192.1.53: udp 53
1.755473 internal -- 168.95.192.1.53 -> 192.168.100.150.56355: udp 69
1.846403 internal -- BPDU 'internal13' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.800f
1.846527 internal -- BPDU 'internal14' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.800e
1.846679 internal -- BPDU 'internal8' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.8008
1.846825 internal -- BPDU 'internal5' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.8005
1.846990 internal -- BPDU 'internal2' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.8002
2.323662 internal -- 192.168.100.150.42804 -> 255.255.255.255.42805: udp 28
2.846555 internal -- BPDU 'internal10' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.800a
3.017873 internal -- arp who-has 192.168.100.1 tell 192.168.100.150
3.017994 internal -- arp reply 192.168.100.1 is-at 8:5b:e:3d:c5:6c
3.087886 internal -- arp who-has 192.168.100.92 tell 192.168.100.108
3.088113 internal -- arp who-has 192.168.100.154 tell 192.168.100.108
3.227996 internal -- 192.168.100.2.2051 -> 255.255.255.255.7437: udp 173
3.555920 internal -- 192.168.100.150.42804 -> 255.255.255.255.42805: udp 28
3.846484 internal -- BPDU 'internal13' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.800f
3.846610 internal -- BPDU 'internal14' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.800e
3.846762 internal -- BPDU 'internal8' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.8008
3.846909 internal -- BPDU 'internal5' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.8005
3.847073 internal -- BPDU 'internal2' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.8002
3.888869 internal -- 192.168.100.150.42804 -> 255.255.255.255.42805: udp 28
4.085808 internal -- arp who-has 192.168.100.92 tell 192.168.100.108
4.085986 internal -- arp who-has 192.168.100.154 tell 192.168.100.108
4.296411 internal -- 192.168.100.150.42804 -> 255.255.255.255.42805: udp 28
4.322509 internal -- 192.168.100.150.42804 -> 255.255.255.255.42805: udp 28
4.631948 internal -- 192.168.100.150.42804 -> 255.255.255.255.42805: udp 28
4.674796 internal -- 192.168.100.150.42804 -> 255.255.255.255.42805: udp 28
4.846454 internal -- BPDU 'internal10' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.800a
4.899530 internal -- 192.168.100.150.42804 -> 255.255.255.255.42805: udp 28
5.085782 internal -- arp who-has 192.168.100.92 tell 192.168.100.108
5.085916 internal -- arp who-has 192.168.100.154 tell 192.168.100.108
5.104649 internal -- 192.168.100.150.42804 -> 255.255.255.255.42805: udp 28
5.220039 internal -- 192.168.100.108.8000 -> 1.1.1.100.6739: udp 296
5.756293 internal -- 192.168.100.108.55430 -> 47.111.162.113.8202: udp 8
5.846424 internal -- BPDU 'internal13' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.800f
5.846550 internal -- BPDU 'internal14' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.800e
5.846704 internal -- BPDU 'internal8' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.8008
5.846852 internal -- BPDU 'internal5' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.8005
5.847021 internal -- BPDU 'internal2' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.8002
5.936230 internal -- arp who-has 192.168.100.90 tell 192.168.100.1
5.936402 internal -- arp reply 192.168.100.90 is-at 0:11:32:3d:a1:3d
6.234162 internal -- 192.168.100.2.2051 -> 255.255.255.255.7437: udp 173
6.846460 internal -- BPDU 'internal10' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.800a
7.094236 internal -- arp who-has 192.168.100.92 tell 192.168.100.108
7.094429 internal -- arp who-has 192.168.100.154 tell 192.168.100.108
7.566222 internal -- arp who-has 192.168.100.91 tell 192.168.100.1
7.568306 internal -- arp reply 192.168.100.91 is-at b4:43:d:38:41:bb
7.846552 internal -- BPDU 'internal13' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.800f
7.846679 internal -- BPDU 'internal14' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.800e
7.846828 internal -- BPDU 'internal8' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.8008
7.846976 internal -- BPDU 'internal5' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.8005
7.847139 internal -- BPDU 'internal2' stp 802.1w, rapid stp, flags [proposal, agreement], bridge-id 8000.08:5b:0e:3d:c5:6c.8002
8.085805 internal -- arp who-has 192.168.100.92 tell 192.168.100.108
8.085941 internal -- arp who-has 192.168.100.154 tell 192.168.100.108
我只是覺得正常流程應該是
192.168.100.150.42804 -> 255.255.255.255.42805: udp 28
這是找房間的廣播,最明顯
我按了好幾下,他就跳好幾個
但我覺得應該會有回應的封包
但就....好像沒看到
然後畫面上的房間就刷新了
(因為在內網所以找得到)
我以為會看到SYN、ACK 之類的
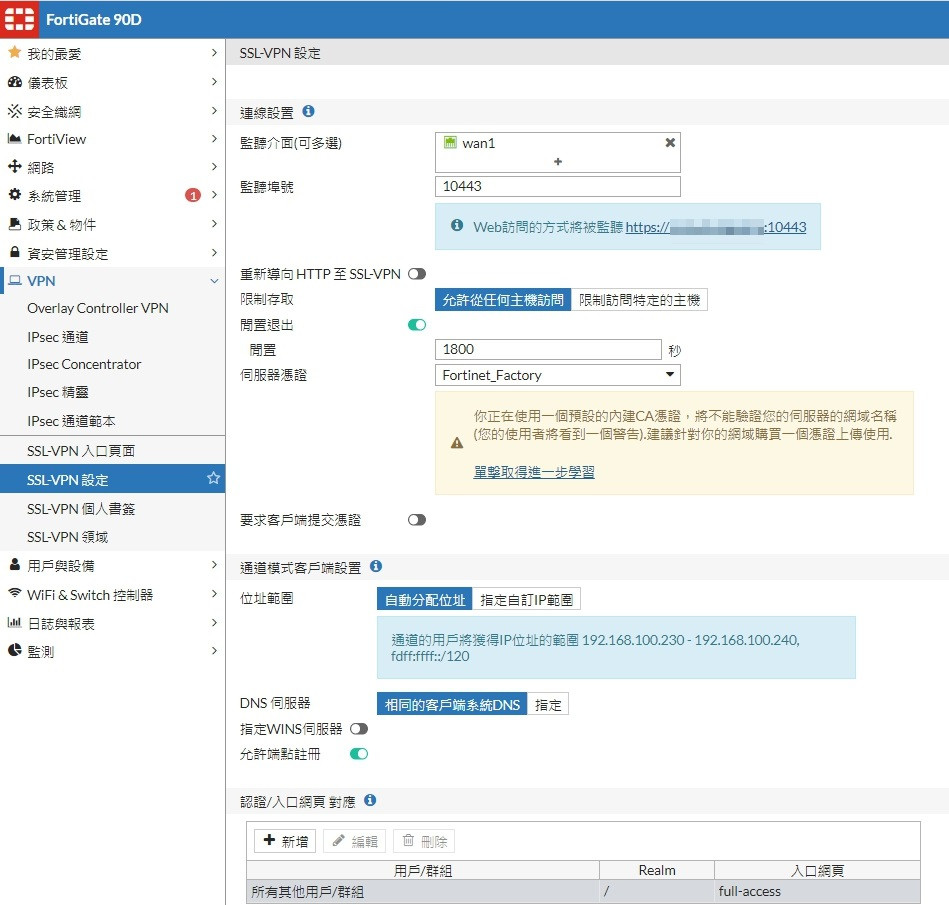
你自己也接SSLVPN
SSLVPN 別用SPLIT TUNNEL
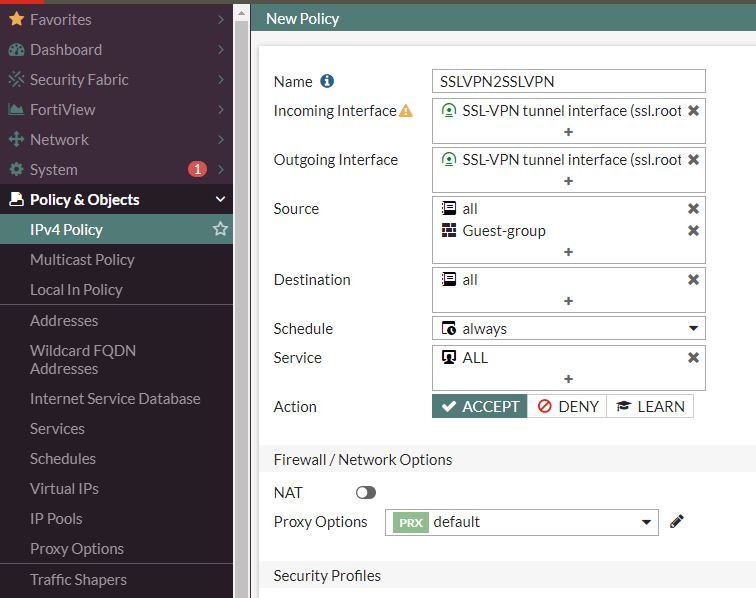
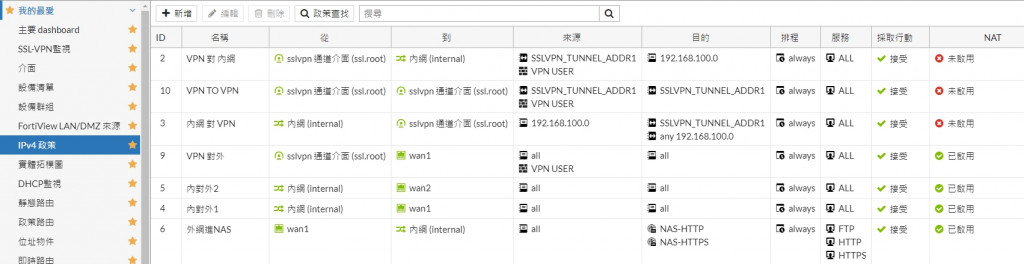
Firewall policy :
SSLVPN to SSLVPN, service any, allow
NO NAT ENABLE
我關了 SPLIT TUNNEL 直接無法對外...
不知道是不是政策要加啥~
我有加一條 ssl.root介面對Wan1的 但還是出不去...
但是!!....這個狀況下還是看不到遊戲房間....
這是開著切分通道的設定結圖(關了就出不去了...)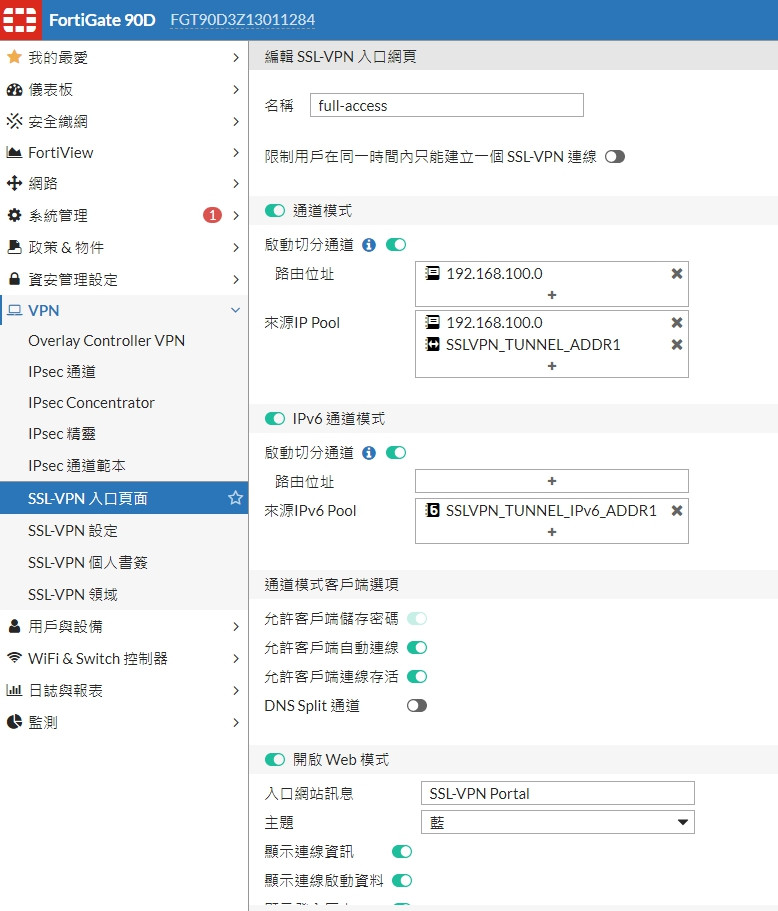
然後我有把NAT關了...也不行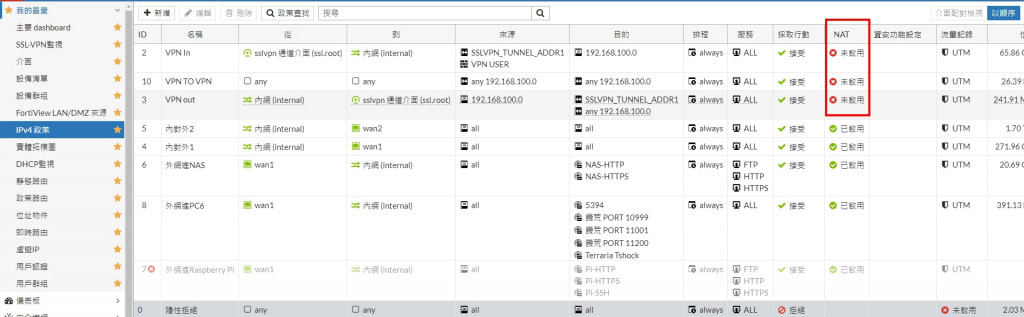
不知道你是不是說這裡
我中間那條 VPN TO VPN 的 介面 any to any
應該等效你說的規則吧
是否我還需要截哪個設定比較清楚
別用SPLIT TUNNEL:
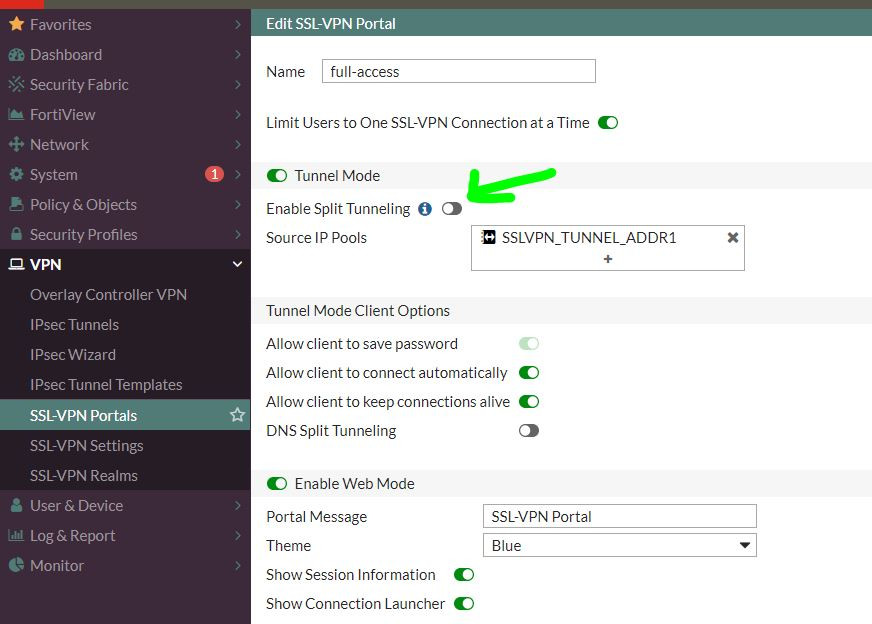
SSLVPN To SSLVPN + NO NAT SAMPLE:
SSLVPN TO WAN SAMPLE, 到WAN的要NAT:
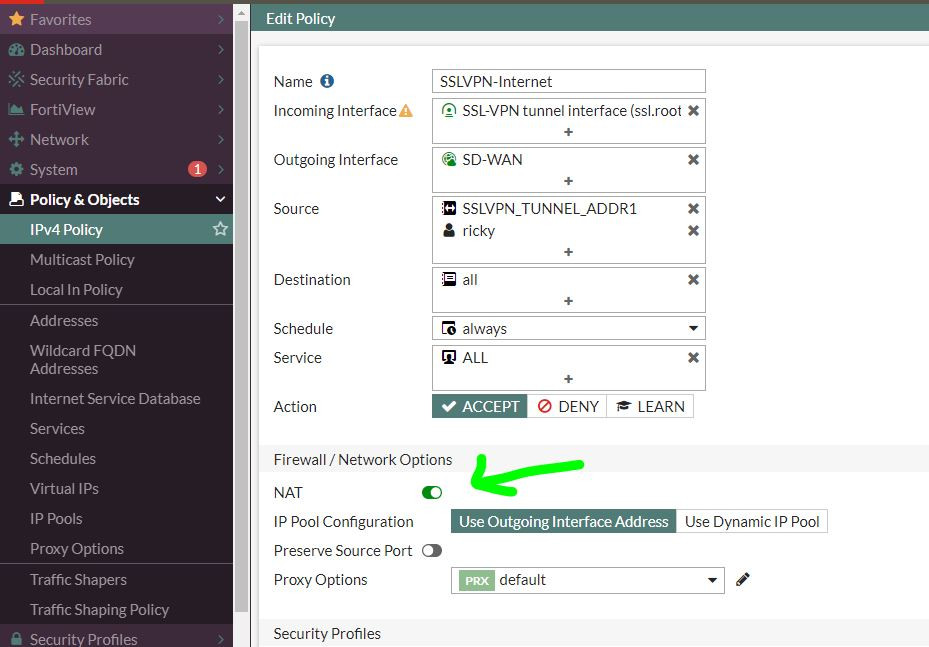
關 SPLIT TUNNEL 的事情我剛才試出來了
我剛才 VPN 對 WAN1 也把NAT關了 所以整個斷網XD
不過這樣對目前的狀況還是沒解...
不過我以前就有發現一個怪事
VPN(A) ping VPN(B) 互相是不通的
內網 ping 任意 VPN 階通
VPN跟VPN之間 好像還是有隔離的狀況
政策路由已經被我加了一堆也不是通XD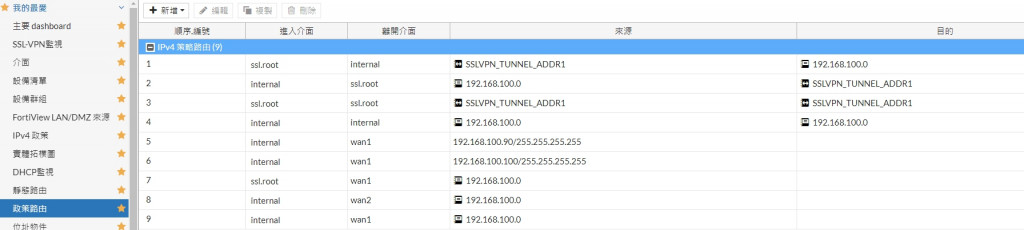
其實這個也是我困惑的一個地方
為什麼我 VPN to VPN 都是不通的...
這個地方我也不知道該怎麼抓包比較好...
FG指令沒這麼熟都是google的XD
不知道上面V4設定有沒有哪裡有誤
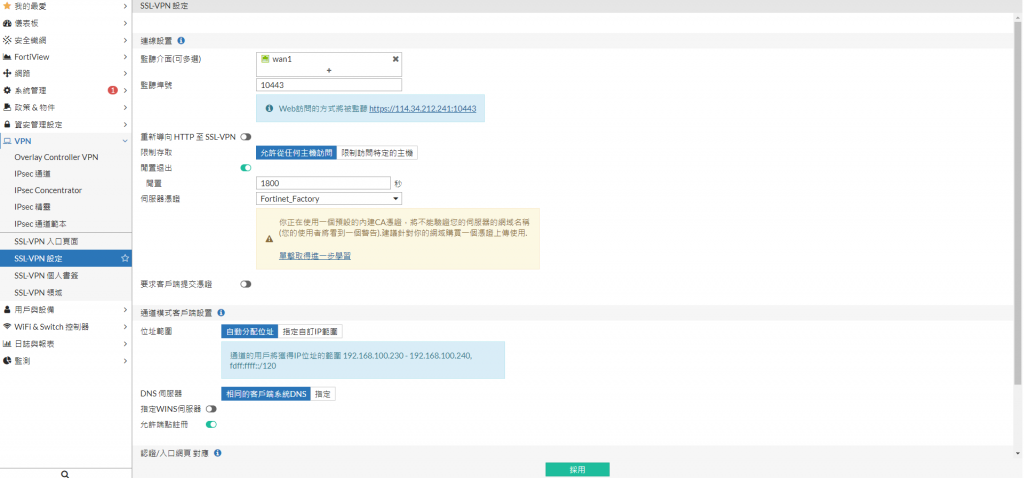
附上兩張VPN目前的設定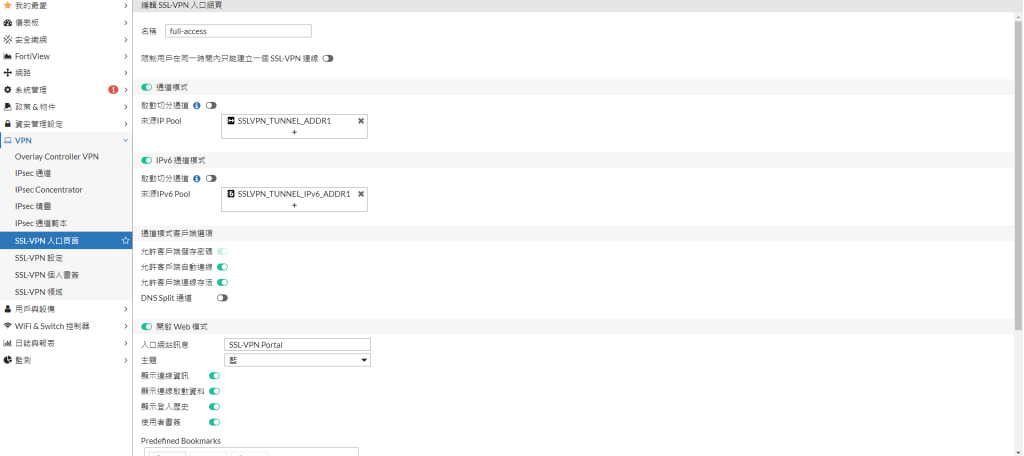
dia sni packet any "host X.X.X.X and host Y.Y.Y.Y" 4 0
X.X.X.X 是 VPN PC A
Y.Y.Y.Y 是 VPN PC B
抓到的包好像沒什麼用...訊息好少T..T
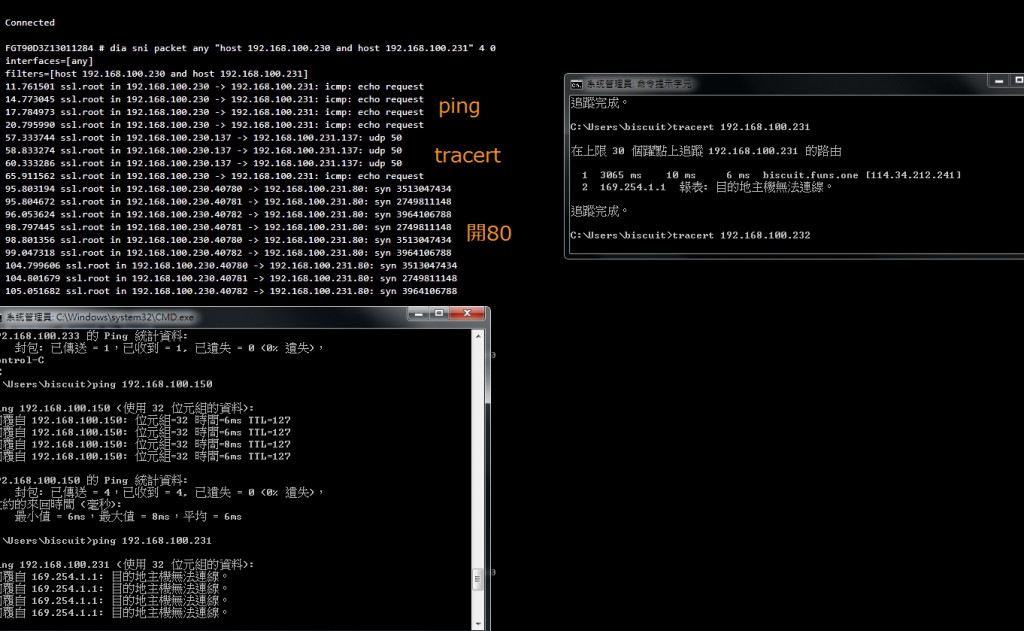
很明顯出問題了, 跑到WAN那邊去了
你干掉你所有PBR再說吧.
讚!! 真的被政策路由搞到 VPN to VPN 把
把VPN相關的政策路由刪了 VPN to VPN 之間正常了!!
不過可惜本案的遊戲的問題還沒解...
之前VPN to VPN 不通的怪問題我也被弄很久...大感謝
我想起來為什麼我會設政策路由了
不過好像要下 internal -> ssl.root
如果沒有這個 內網 -> VPN 不會通
(應該跑出去了)
VPN -> 內網
(預設通)
發現在 IPv4政策
下 內網 -> VPN 跟 VPN -> 內網 是完全沒用的
啟用/停用 都沒用處
你作為SERVER電腦的 跟 玩家 的電腦都分別DEBUG一下
在 玩家 -> SERVER電腦 連遊戲時才好DEBUG
dia sni packet any "host X.X.X.X" 4 0
dia sni packet any "host Y.Y.Y.Y" 4 0