防火牆的本義,是指古代使用木製結構房屋時,為防止火災發生及蔓延,人們將石塊堆砌在房屋周圍做為屏障,這種防護建築就被稱為防火牆。現代網路時代參照此喻意,指隔離本機網路與外界網路或是區域網路間與網際網路的一道防禦系統,藉由控制、過濾、限制訊息來保護內部網路資料的安全。
(來源:防火牆)
網址:How firewalls work | Network firewall security | firewall security | TechTerms
(截圖來自影片)
防火牆的用途:使用者在上網時,常會有個資問題。防火牆防止hacker取得個資: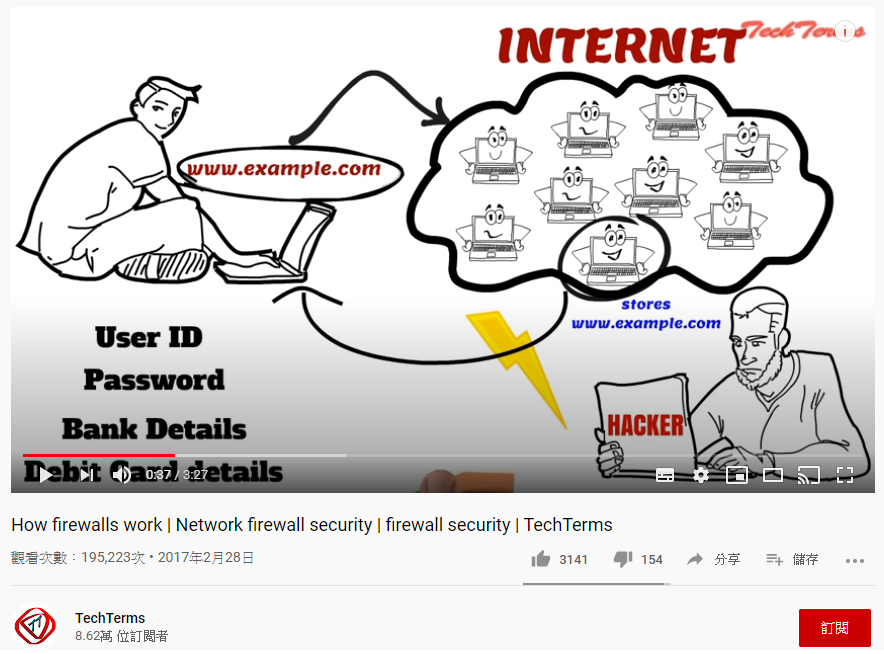
封包過濾就是用一個軟體查看所流經封包之標頭(header)﹐由此決定整個封包的命運。它或許會決定丟棄(DROP)這個封包(忽略它就如根本沒收到它一樣)﹐或是接收(ACCEPT)這個封包(讓這個封包通過)﹐或是其它更複雜的動作。
如圖,就是當網站要response使用者時,拒絕SAM這個駭客的封包,通過BOB的封包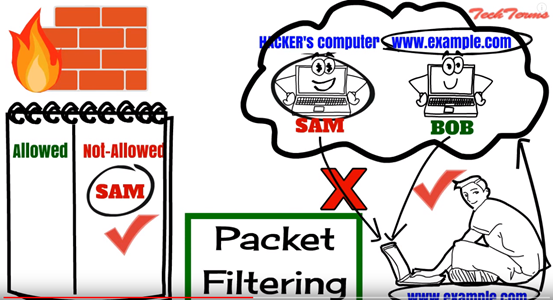
如圖:當Bob要連到youtube時,駭客不能取代youtube亂傳影音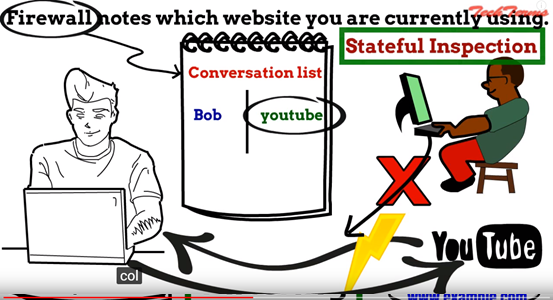
來源:
stateful inspection
dynamic packet filter
1 static packet filtering(封包過濾)(stateless)(狀態感知):
In static packet filtering, only the headers of packets are checked -- which means that an attacker can sometimes get information through the firewall simply by indicating "reply" in the header.
2 dynamic packet filtering(又稱Stateful inspection)(狀態檢視):
Stateful inspection, on the other hand, analyzes packets down to the application layer. By recording session information such as IP addresses and port numbers, a dynamic packet filter can implement a much tighter security posture than a static packet filter can.
Stateful inspection可以檢查像是IP addresses 或port numbers,比static packet filter安全
Stateful inspection monitors communications packets over a period of time and examines both incoming and outgoing packets. Outgoing packets that request specific types of incoming packets are tracked and only those incoming packets constituting a proper response are allowed through the firewall.
Stateful inspection檢查packets每隔一段時間,Outgoing packets被tracked(應該是指被記錄、被檢查),incoming packets要有proper response才能通過防火牆
In a firewall that uses stateful inspection, the network administrator can set the parameters to meet specific needs. In a typical network, ports are closed unless an incoming packet requests connection to a specific port and then only that port is opened. This practice prevents port scanning, a well-known hacking technique.
Port通常都關閉的,除非incoming packet要求connection to a specific port,然後只有那個specific port會開啟,這樣可以防止port scanning
接著文章舉了一個例子:
For example, assume that you wish to configure your firewall so that all users in your company are allowed out to the Internet, but only replies to users' data requests are let back in. With a static packet filter, you would need to permanently allow in replies from all external addresses, assuming that users were free to visit any site on the Internet. This kind of filter would allow an attacker to sneak information past the filter by making the packet look like a reply (which can be done by indicating "reply" in the packet header).
By tracking and matching requests and replies, a dynamic packet filter can screen for replies that don't match a request. When a request is recorded, the dynamic packet filter opens up a small inbound hole so only the expected data reply is let back through. Once the reply is received, the hole is closed. This dramatically increases the security capabilities of the firewall.
在一個公司裡,你允許你的員工都可以連到網際網路,但只會回應員工的要求(users' data requests)。
這會讓駭客製造一個假的回應(修改packet header)
但是如果是dynamic packet filter,可以讓request和reply有相關聯,只有那個reply屬於request,當request is recorded,opens up a small inbound hole,當the reply is received,the hole is closed。
1 代理伺服器用來連接一個網路(例:網際網路)到另一個特定子網(例:企業內網)的轉送者。這張圖fb代表代理伺服器,連接一個網路(Internet),和特定子網(使用者:John)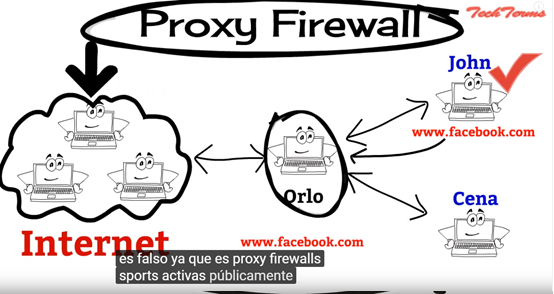
2 The difference is that in addition to intercepting Internet requests and responses, a proxy firewall also monitors incoming traffic for layer 7 protocols, such as HTTP and FTP.
代理伺服器不只有網路層的檢查,還有應用層的協定檢查,像是: HTTP and FTP
3 In addition to determining which traffic is allowed and which is denied, a proxy firewall uses stateful inspection technology and deep packet inspection to analyze incoming traffic for signs of attack.
Firewall用stateful inspection technology和deep packet inspection來防止駭客攻擊
什麼是deep packet inspection?
深度封包檢測(英語:Deep packet inspection,縮寫為 DPI)
簡單來說應該是:當傳送封包時,並沒有只看目的地的位址,還有查看封包的其他內容,像是有沒有不符規定的協定、病毒、垃圾郵件。
4 Proxy firewalls are considered to be the most secure type of firewall because they prevent direct network contact with other systems. (Because a proxy firewall has its own IP address, an outside network connection will never receive packets from the sending network directly.)
Proxy firewalls可能是比較安全的防火牆,防止網路直接地連接到其他系統,因為Proxy firewalls有專屬的IP address,外部網路不會直接地從使用者(送出資料的人)接收到封包
5 Having the ability to examine the entire network packet, rather than just the network address and port number, also means that a proxy firewall will have extensive logging capabilities -- a valuable resource for security administrators who are dealing with security incidents.
Proxy firewalls檢查全部的網路封包,而不是只有IP位址、port number,所以資安人員用Proxy firewalls來檢查網路安全
6 The added security offered by a proxy firewall has its drawbacks, however. Because a proxy firewall establishes an additional connection for each outgoing and incoming packet, the firewall can become a bottleneck, causing a degradation of performance or becoming a single point of failure. Additionally, proxy firewalls may only support certain popular network protocols, thereby limiting which applications the network can support.
proxy firewall也有缺點,因為為每個傳入和傳出的封包建立額外的連接,導致效能降低或a single point of failure,還有proxy firewall可能只支援幾種協定,限制了某些應用程式的支援
什麼是a single point of failure?
指系統中一旦失效,就會讓整個系統無法運作的部件
單點故障
Uncomplicated Firewall 的 ufw,意思就是簡單的、不複雜的防火牆,相對於 iptables 來說,ufw 是真的簡單很多了!ufw其實只是一個 iptables 的前端設定程式,最後的規則都還是會走 iptables ,而且比較複雜的功能還是要直接透過 iptables 才有辦法做到!
防火牆指令:
Ubuntu based GNU/Linux 上的防火牆 (ufw) 基本設定
以下是一些練習:
sudo ufw enable
開啟防火牆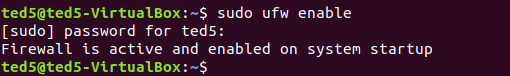
確認防火牆狀態
已啟用:Status: active
未啟用:Status: inactive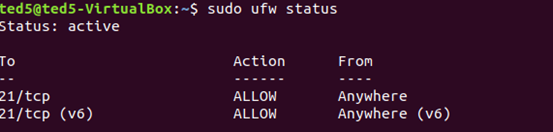
預設允許所有連入連線通過
sudo ufw default allow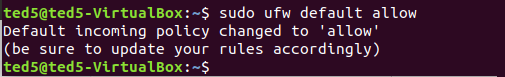
檢查incoming (連入) / outgoing (連出)的狀況
sudo ufw status verbose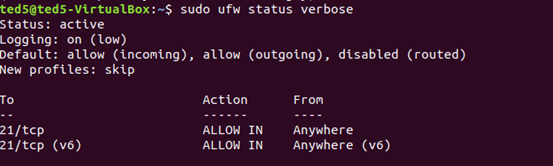
ufw <allow/deny>
ufw 允許 http(80 port)
ufw 允許 ftp (21 port)
(關於 port / serveice 的對應可以參考 /etc/services)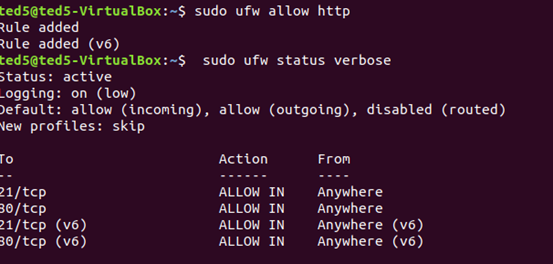
ufw 允許 ssh (22 port)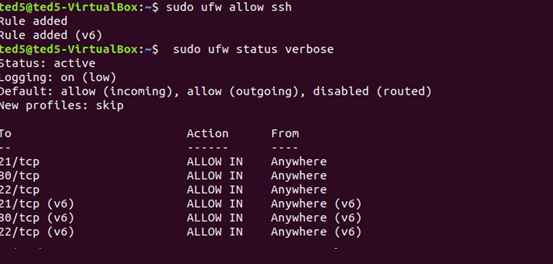
sudo ufw delete allow http/tcp
可以刪除http連線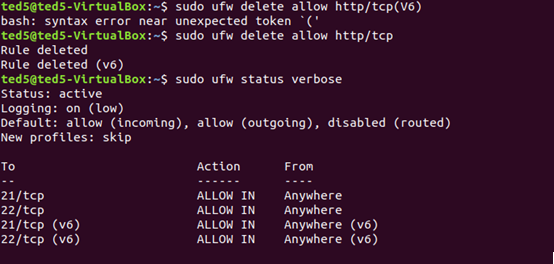
ufw allow / deny from / to ip
例: sudo ufw allow from 10.0.0.0/8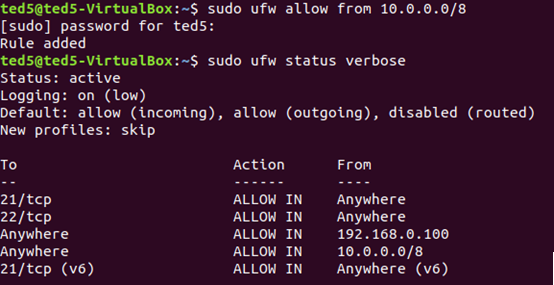
sudo ufw status numbered可以顯示編號,刪除時只要sudo ufw delete 5(編號)就可以了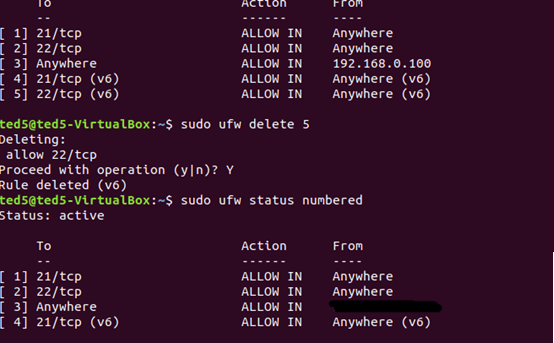
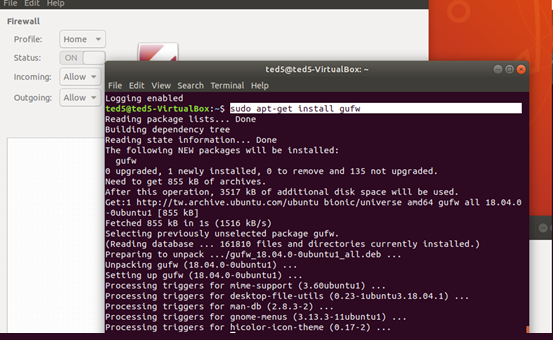
安裝防火牆圖形介面