閱讀一篇論文State of the Art Analysis of Defense Techniques against Advanced Persistent Threats摘要其重點如下:
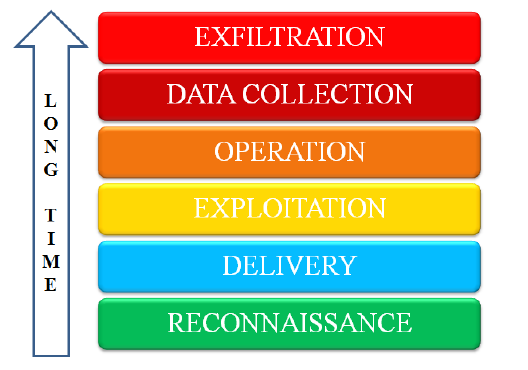
首先簡介一下APT流程包含:
Reconnaissance偵查:了解環境、人員、有價資源、防護機制
Delivery傳遞:透過各種管道,如社交工程、usb、email、釣魚網站,植入惡意程式
Exploitation滲透:持行惡意程式,感染主機,並且主動進行橫向擴散
Operation操作:Hacking動作,包含提權、擴散、毀跡等
Data Collection資料蒐集:蒐集機敏資料,如資料庫、智慧財產資料、信用卡/系統帳密
Exfiltration滲出:將這些資料在通訊行為縝密的偽裝下,一點一點地流出。
使用來偵測APT的資料,文獻所整理出有幫助的特徵包含:packet capture (PCAP)網路封包、TCP attributes
將偵測APT的問題視為建立一個異常分類演算法的問題anomaly classification algorithm.
方法選擇:推薦使用K- Nearest Neighbors and the Correlation-based algorithm.
作者對商用資安廠商所提供的防護機制做了一個比較表如下
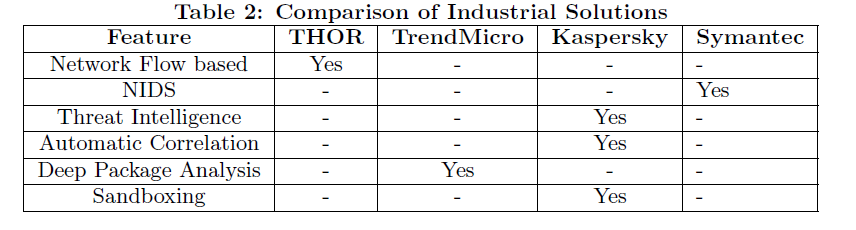
有效做法為發展混合型防護機制,包含誘捕系統用來早期偵測以及誤導攻擊者,搭配網路流量監控、多層式的過濾偵測方法,以及持續累積已知威脅攻擊情資,並且推薦發展智慧化的APT 生命週期產生器,作為監控周期的單位。
Quote: “The proposal for a better industrial products will be to use a hybrid system that encompasses the features of honey pots for early detection and misleading for systems which are regularly monitored by a security team, fractal analysis for IT infrastructures involving heavy traffic flows and globally distributed network by backing up with a distributed multi staged detection system, system and attack intelligence for industrial systems and intrusion kill chains clubbed with context behavior in case of middle-sized implementation.”
參考來源
State of the Art Analysis of Defense Techniques against Advanced Persistent Threats
https://www.net.in.tum.de/fileadmin/TUM/NET/NET-2017-09-1/NET-2017-09-1_09.pdf

不曉得有沒有人用 ML 去做 ATT&CK....
整個/全部應該很難,但是部分階段例如Lateral Movement是有的