我不知道看官的答案是什麼,我的是安安、呵呵,去洗澡馬上提高路由器的安全措施,因為它是24小時連網的第一關,敵人會24小時湧上來敲門,不過"祖國的"會有午餐跟晚餐時間![]() 。
。
凡是走過linux的大大們,回答都不外乎:
所以今天要在Bosley身上完成這3件事,第一件事還算簡單,可以用web介面完成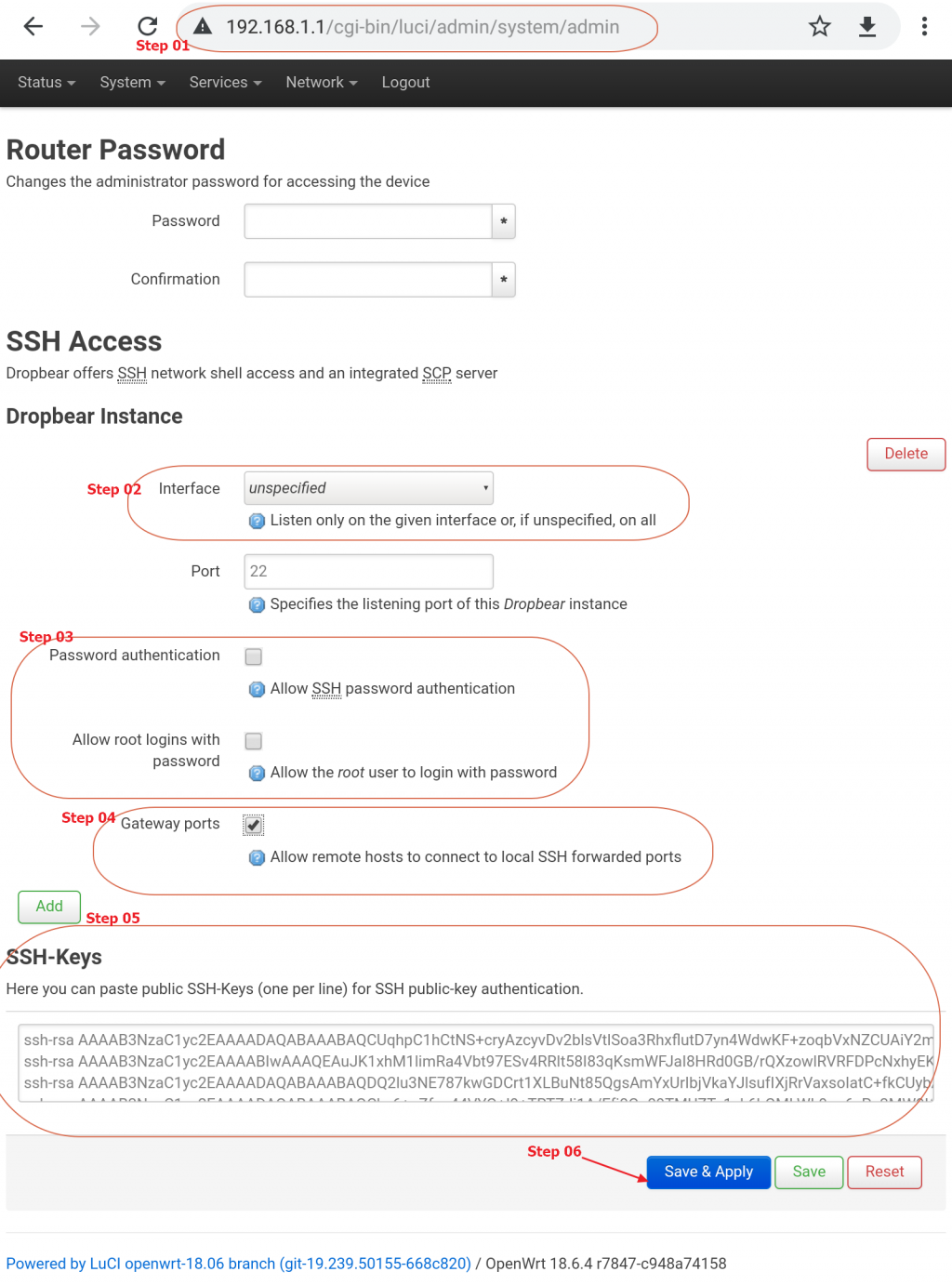
安裝相關套件
opkg update
opkg install shadow-useradd shadow-groupadd shadow-usermod sudo shadow bash
然後增加帳號,如果你要增加我的帳號icekimo到你的機器我也不反對,不然就換成你各位的名字
mkdir -p /home/icekimo
useradd icekimo -U -d /home/icekimo -s /bin/bash
groupadd --system sudo
usermod -a -G sudo icekimo
然後把自己變成不用密碼的sudoer
visudo
## Uncomment to allow members of group sudo to execute any command
%sudo ALL=(ALL) NOPASSWD: ALL
接下來請不要忘記在自己家目錄放入.ssh/authorized_keys,這很重要,不然你自己進不去就好笑了。
最後第三項事情就有點複雜了。
Openwrt這類嵌入式linux,最愛的搭檔不是GNU系列,而是busybox、ash、dropbear這類短小精幹的閹割特化版程式。假使各位沒有經過後面幾天的手賤換成OpenSSH,在ash與dropbear的搭檔下,我推薦beardropper這個腳本,會幫你把熊孩子bear丟drop到門外,thanks to robzr ,that’s awesome。
首先補上套件讓內建(busybox偽裝)的wget會處理ssl,當然如果是後面幾天編譯出來天生神力的wget版本,就可以省掉這步驟。
opkg install libustream-openssl ca-certificates ca-bundle
然後跑作者寫的安裝腳本(真貼心!!裡面也一樣一堆wget,注意這裡會處理https重導)
wget -qO- http://rawgit.com/robzr/bearDropper/master/install.sh | sh
# My example
root@Bosley:/home/icekimo# wget -qO- http://rawgit.com/robzr/bearDropper/master/
install.sh | sh
Retrieving and installing latest version
Processing historical log data (this can take a while)
Running in entire mode
Starting background process
Starting bearDropper
root@Bosley:/home/icekimo#
調整一下/etc/config/bearDropper
config bearDropper
# mode used if no mode is specified on command line; see bearDropper -h for help.
option defaultMode entire
# failure attempts from a given IP required to trigger a ban
option attemptCount 5
# time period during which attemptCount must be exceeded in order to trigger a ban
option attemptPeriod 12h
# how long a ban exist once the attempt threshold is exceeded
option banLength 1w
# My example
root@Bosley:/home/icekimo# vi /etc/config/bearDropper
root@Bosley:/home/icekimo# /etc/init.d/bearDropper reload
Stopping bearDropper 4079
Starting bearDropper
root@Bosley:/home/icekimo#
然後把記錄檔加大,vi /etc/config/system
config system
option ttylogin '0'
option log_size '1024'
啟動服務
/etc/init.d/bearDropper start
好了,今天功課做完了希望開洞給人打的時間不多,可以安心睡覺了。什麼,你看完昨天刷機跟著做以後,就真的洗洗睡到今天?好吧,那我給你看一點東西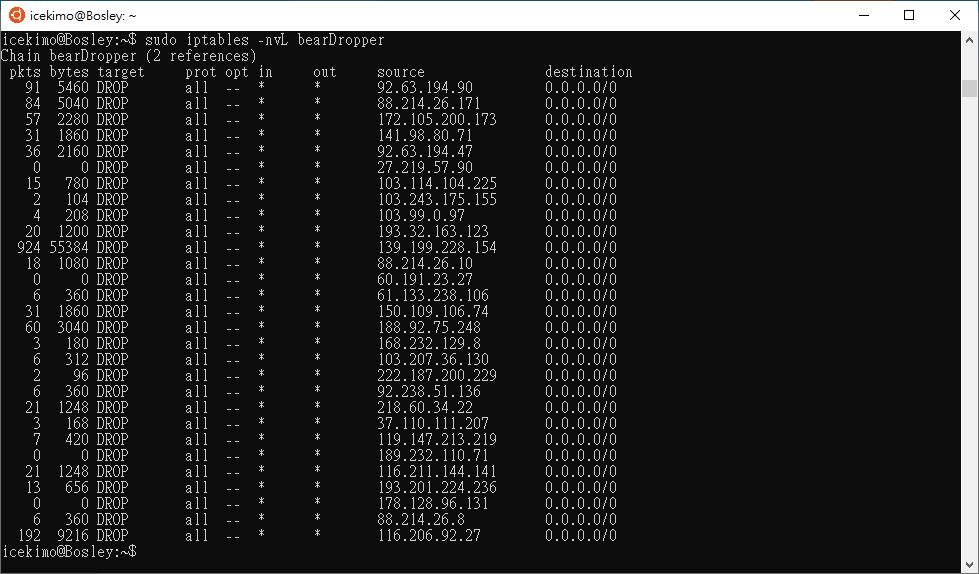
各位,這世界是殘酷的,不要認為安全會從天上掉下來,國防預算只有買的好不好,沒有該不該。
『但是還有沒有可以再加強的呢?』如果老闆問你這句話,K他正所謂隨著時間的流逝,安全的準備應該越來越多。是,有的。加強黑名單阻擋,把世界上知名的壞人都擋掉,這樣就省事多了。這就叫做RBL blocking。
如果你素行不良,多有結怨,老闆人品又不好身處在中華民國的保護,隔壁有個上班就會搞你的牆國,你可以斟酌自己路由器的能力,增加這個神奇的功能。但是我必須提出使用警告,使用防火牆功能一定會影響效能的,不要幻想你的小盒子openwrt什麼都可以做這樣跟台灣的慣老闆沒有兩樣。這功能一樣是robzr帶來的。讓我們歡迎sub2rbl。
首先安裝指令參考如下
opkg install ipset kmod-ipt-ipset curl ca-certificates
wget -O /etc/config/sub2rbl http://rawgit.com/robzr/sub2rbl/master/config/sub2rbl
wget -O /usr/sbin/sub2rbl http://rawgit.com/robzr/sub2rbl/master/sub2rbl
chmod 755 /usr/sbin/sub2rbl
echo /usr/sbin/sub2rbl >> /etc/firewall.user
echo '0 */6 * * * /usr/sbin/sub2rbl' >> /etc/crontabs/root
/etc/init.d/cron enable
# And to watch it in action, for the first run, try:
sub2rbl -l 2 -f stdout
如果你看到我看到的,我想這應該就是對的
root@Bosley:/srv/ipk# sub2rbl -l 2 -f stdout
Creating ipset sub2rbl
Creating ipset sub2rbl_swing
Retrieving RBL (https://rbldata.interserver.net/ip.txt)
RBL (https://rbldata.interserver.net/ip.txt) added 7050 entries
Retrieving RBL (https://lists.blocklist.de/lists/ssh.txt)
RBL (https://lists.blocklist.de/lists/ssh.txt) added 5523 entries
Retrieving RBL (https://lists.blocklist.de/lists/strongips.txt)
RBL (https://lists.blocklist.de/lists/strongips.txt) added 42 entries
Retrieving RBL (https://www.dragonresearchgroup.org/insight/sshpwauth.txt)
Error: retrieving RBL(https://www.dragonresearchgroup.org/insight/sshpwauth.txt): curl: (28) Connection timed out after 15000 milliseconds
Creating ipset sub2rbl-net
Creating ipset sub2rbl-net_swing
Retrieving RBL (https://www.spamhaus.org/drop/drop.txt)
RBL (https://www.spamhaus.org/drop/drop.txt) added 848 entries
Retrieving RBL (https://www.spamhaus.org/drop/edrop.txt)
RBL (https://www.spamhaus.org/drop/edrop.txt) added 115 entries
Inserting iptables rule for sub2rbl into chain input_wan_rule
Inserting iptables rule for sub2rbl into chain forwarding_wan_rule
Destroying ipset sub2rbl_swing
Inserting iptables rule for sub2rbl-net into chain input_wan_rule
Inserting iptables rule for sub2rbl-net into chain forwarding_wan_rule
Destroying ipset sub2rbl-net_swing
root@Bosley:/srv#
那麼實體的呢?不要忘記這是AP,凡是無線網路一律使用WPA2,以及強制TKIP與CCMP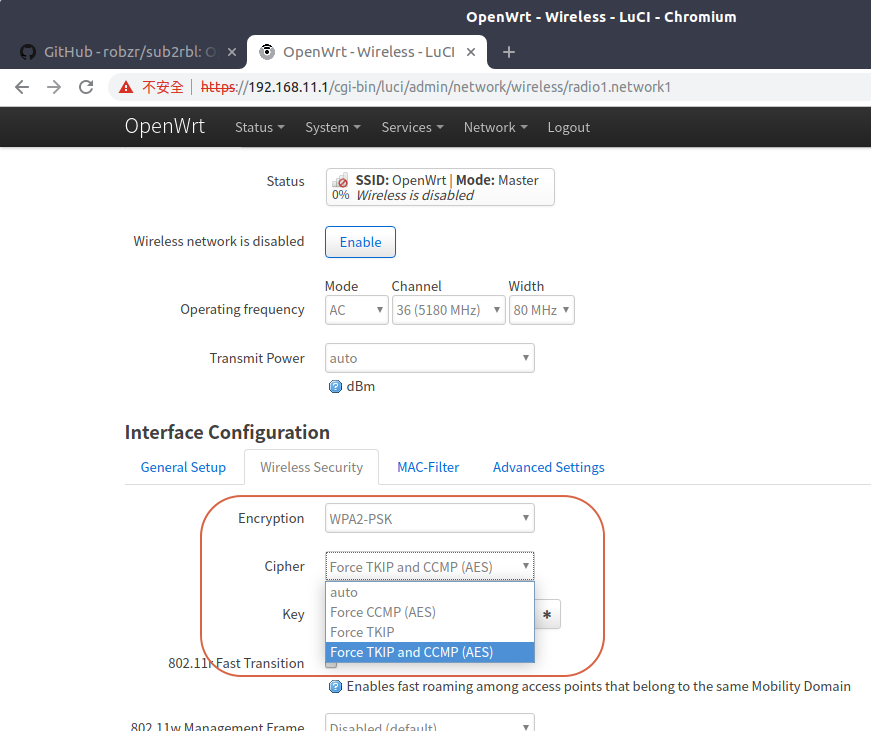
秉持著嚐鮮的精神,你可以學我勾起,如果你有重要到怕被人wardrive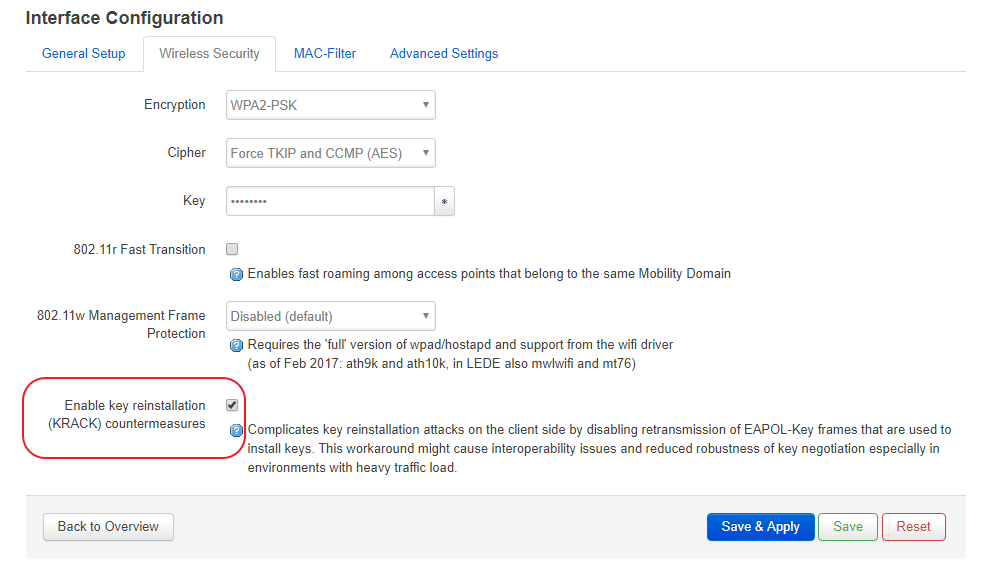
再來呢?就等明天揭曉囉。
