今天要介紹的工具叫做挖鼻涕Wapiti,是用來掃描網頁的安全性,以黑盒的方式,也就是在不了解網頁內部如何實作的狀況下,模擬真實攻擊者的手法。以下是Wapiti涵蓋的偵測項目
先來看一下用法
__ __ _ _ _ _____
/ / /\ \ \__ _ _ __ (_) |_(_)___ /
\ \/ \/ / _` | '_ \| | __| | |_ \
\ /\ / (_| | |_) | | |_| |___) |
\/ \/ \__,_| .__/|_|\__|_|____/
|_|
Wapiti-3.0.4 (wapiti.sourceforge.io)
[*] Be careful! New moon tonight.
usage: wapiti [-h] [-u URL] [--scope {page,folder,domain,url,punk}]
[-m MODULES_LIST] [--list-modules] [--update] [-l LEVEL]
[-p PROXY_URL] [--tor] [-a CREDENTIALS]
[--auth-type {basic,digest,kerberos,ntlm,post}]
[-c COOKIE_FILE] [--skip-crawl] [--resume-crawl]
[--flush-attacks] [--flush-session] [--store-session PATH]
[--store-config PATH] [-s URL] [-x URL] [-r PARAMETER]
[--skip PARAMETER] [-d DEPTH] [--max-links-per-page MAX]
[--max-files-per-dir MAX] [--max-scan-time SECONDS]
[--max-attack-time SECONDS] [--max-parameters MAX] [-S FORCE]
[-t SECONDS] [-H HEADER] [-A AGENT] [--verify-ssl {0,1}]
[--color] [-v LEVEL] [-f FORMAT] [-o OUPUT_PATH]
[--external-endpoint EXTERNAL_ENDPOINT_URL]
[--internal-endpoint INTERNAL_ENDPOINT_URL]
[--endpoint ENDPOINT_URL] [--no-bugreport] [--version]
wapiti: error: one of the arguments -u/--url --list-modules --update is required
這邊用-o指定輸出資料夾,-f指定輸出格式為html,最後-u指定靶機上的頁面
wapiti -o wapiti_result -f html -u http://192.168.1.86/dvwa
掃描過程會逐漸更新資訊,最後將結果產生一個報表輸出到指定的位置
Note
========
This scan has been saved in the file /home/kali/.wapiti/scans/192.168.1.86_folder_335476bb.db
[*] Wapiti found 3 URLs and forms during the scan
[*] Loading modules:
backup, blindsql, brute_login_form, buster, cookieflags, crlf, csp, csrf, exec, file, htaccess, http_headers, methods, nikto, permanentxss, redirect, shellshock, sql, ssrf, wapp, xss, xxe
Problem with local wapp database.
Downloading from the web...
[*] Launching module csp
CSP is not set
[*] Launching module http_headers
Checking X-Frame-Options :
X-Frame-Options is not set
Checking X-XSS-Protection :
X-XSS-Protection is not set
Checking X-Content-Type-Options :
X-Content-Type-Options is not set
Checking Strict-Transport-Security :
Strict-Transport-Security is not set
[*] Launching module cookieflags
Checking cookie : PHPSESSID
HttpOnly flag is not set in the cookie : PHPSESSID
Secure flag is not set in the cookie : PHPSESSID
Checking cookie : security
HttpOnly flag is not set in the cookie : security
Secure flag is not set in the cookie : security
[*] Launching module exec
[*] Launching module file
[*] Launching module sql
[*] Launching module xss
[*] Launching module ssrf
[*] Asking endpoint URL https://wapiti3.ovh/get_ssrf.php?id=glpejm for results, please wait...
[*] Launching module redirect
[*] Launching module blindsql
[*] Launching module permanentxss
Report
------
A report has been generated in the file wapiti_result
Open wapiti_result/192.168.1.86_10042021_1417.html with a browser to see this report.
可以透過open來將輸出結果以瀏覽器開啟
open wapiti_result/192.168.1.86_10042021_1417.html
報表一打開就是所有被掃瞄出的問題的統計結果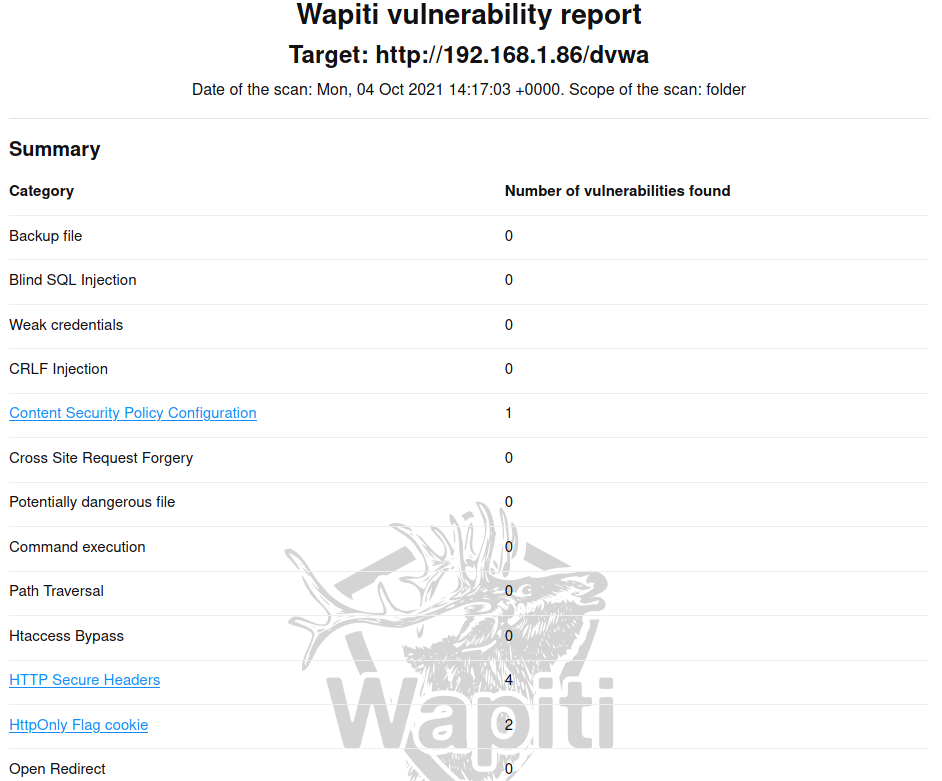
點擊藍底的超連結項目或是直接往報表下面捲動,都可以看到每個問題的詳細資訊,而且還有建議的解決方案並且附上參考連結,感覺很不錯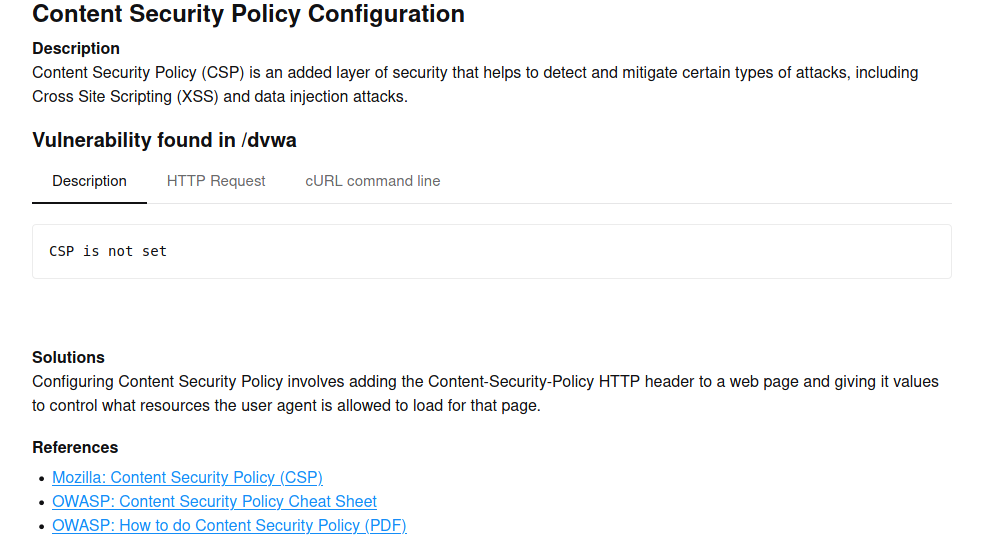
另外掃描過的目標,如果再掃一次,可能會發現第二次掃描很快就結束了,這是因為有一些資料已經先被記錄下來,有點像cache的機制,但是是以sqlite的形式放在/home/kali/.wapiti之下
