接下來都會採用 CMD的方式來進行設定,方便操作,所以我們需要先有一台可以下CMD的機器,我們這部分先用 CloudShell 來進行設定。
AWS CloudShell 是一個 瀏覽器內建的命令列環境。
你登入 AWS Console 後,就能直接使用 AWS CLI、Python、PowerShell 等工具,
不需要額外安裝或設定憑證。
透過畫面上右上角開啟
#!/bin/bash
set -e
STACK_NAME="MyVpcStack"
TEMPLATE_FILE="vpc-template.yaml"
REGION="ap-northeast-1"
# === 產生 CloudFormation YAML ===
cat > $TEMPLATE_FILE << 'EOF'
AWSTemplateFormatVersion: 2010-09-09
Description: VPC with 2 AZs, 2 Public Subnets, 4 Private Subnets, 1 NAT Gateway, and 1 IGW
Parameters:
VpcCidr:
Type: String
Default: 10.0.0.0/16
Resources:
VPC:
Type: AWS::EC2::VPC
Properties:
CidrBlock: !Ref VpcCidr
EnableDnsSupport: true
EnableDnsHostnames: true
Tags:
- Key: Name
Value: MyVpc
InternetGateway:
Type: AWS::EC2::InternetGateway
AttachGateway:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
VpcId: !Ref VPC
InternetGatewayId: !Ref InternetGateway
PublicSubnet1:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPC
CidrBlock: 10.0.1.0/24
AvailabilityZone: !Select [ 0, !GetAZs '' ]
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: PublicSubnet1
PublicSubnet2:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPC
CidrBlock: 10.0.2.0/24
AvailabilityZone: !Select [ 1, !GetAZs '' ]
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: PublicSubnet2
PrivateSubnet1:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPC
CidrBlock: 10.0.3.0/24
AvailabilityZone: !Select [ 0, !GetAZs '' ]
Tags:
- Key: Name
Value: PrivateSubnet1
PrivateSubnet2:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPC
CidrBlock: 10.0.4.0/24
AvailabilityZone: !Select [ 1, !GetAZs '' ]
Tags:
- Key: Name
Value: PrivateSubnet2
PrivateSubnet3:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPC
CidrBlock: 10.0.5.0/24
AvailabilityZone: !Select [ 0, !GetAZs '' ]
Tags:
- Key: Name
Value: PrivateSubnet3
PrivateSubnet4:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPC
CidrBlock: 10.0.6.0/24
AvailabilityZone: !Select [ 1, !GetAZs '' ]
Tags:
- Key: Name
Value: PrivateSubnet4
PublicRouteTable:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: PublicRT
PublicRoute:
Type: AWS::EC2::Route
DependsOn: AttachGateway
Properties:
RouteTableId: !Ref PublicRouteTable
DestinationCidrBlock: 0.0.0.0/0
GatewayId: !Ref InternetGateway
PublicSubnet1RouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PublicSubnet1
RouteTableId: !Ref PublicRouteTable
PublicSubnet2RouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PublicSubnet2
RouteTableId: !Ref PublicRouteTable
NatEIP:
Type: AWS::EC2::EIP
Properties:
Domain: vpc
NatGateway:
Type: AWS::EC2::NatGateway
Properties:
AllocationId: !GetAtt NatEIP.AllocationId
SubnetId: !Ref PublicSubnet1
Tags:
- Key: Name
Value: NatGateway
PrivateRouteTable:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: PrivateRT
PrivateRoute:
Type: AWS::EC2::Route
Properties:
RouteTableId: !Ref PrivateRouteTable
DestinationCidrBlock: 0.0.0.0/0
NatGatewayId: !Ref NatGateway
PrivateSubnet1RouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PrivateSubnet1
RouteTableId: !Ref PrivateRouteTable
PrivateSubnet2RouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PrivateSubnet2
RouteTableId: !Ref PrivateRouteTable
PrivateSubnet3RouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PrivateSubnet3
RouteTableId: !Ref PrivateRouteTable
PrivateSubnet4RouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PrivateSubnet4
RouteTableId: !Ref PrivateRouteTable
Outputs:
VpcId:
Value: !Ref VPC
Description: VPC ID
PublicSubnet1:
Value: !Ref PublicSubnet1
PublicSubnet2:
Value: !Ref PublicSubnet2
PrivateSubnet1:
Value: !Ref PrivateSubnet1
PrivateSubnet2:
Value: !Ref PrivateSubnet2
PrivateSubnet3:
Value: !Ref PrivateSubnet3
PrivateSubnet4:
Value: !Ref PrivateSubnet4
EOF
# === 修改檔案權限 ===
chmod 644 $TEMPLATE_FILE
# === 顯示操作指引 ===
echo "✅ CloudFormation YAML 模板已生成並保存為 $TEMPLATE_FILE"
echo "請使用以下命令來部署 CloudFormation Stack:"
echo "aws cloudformation create-stack --stack-name $STACK_NAME --template-body file://$TEMPLATE_FILE --capabilities CAPABILITY_NAMED_IAM --region $REGION"
這裡透過cloudformation IAC的方式進行建置,可以在cloudformaction 觀察目前建置的進度。
建置完畢後執行以下直令呼叫 cloudformation
aws cloudformation create-stack --stack-name $STACK_NAME --template-body file://$TEMPLATE_FILE --capabilities CAPABILITY_NAMED_IAM --region $REGION
最後就可以於 console 看到相關建置的資源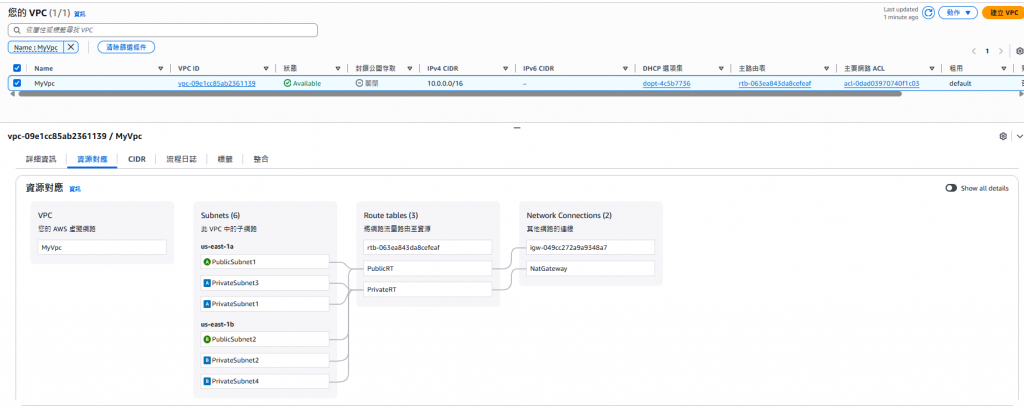
# 更新系統並安裝必要的工具
sudo yum update -y
sudo yum install -y curl
# 下載最新版本的 kubectl
curl -LO "https://dl.k8s.io/release/v1.24.0/bin/linux/amd64/kubectl"
# 給 kubectl 文件賦予執行權限
chmod +x ./kubectl
# 移動 kubectl 到 /usr/local/bin 目錄
sudo mv ./kubectl /usr/local/bin/
# 驗證安裝
kubectl version --client
kubectl 就像是 Kubernetes 的遙控器,讓你輕鬆操控集群中的所有資源,不管是部署應用還是查看狀態,只需一條命令,集群盡在你掌控中!
# for ARM systems, set ARCH to: `arm64`, `armv6` or `armv7`
ARCH=amd64
PLATFORM=$(uname -s)_$ARCH
curl -sLO "https://github.com/eksctl-io/eksctl/releases/latest/download/eksctl_$PLATFORM.tar.gz"
# (Optional) Verify checksum
curl -sL "https://github.com/eksctl-io/eksctl/releases/latest/download/eksctl_checksums.txt" | grep $PLATFORM | sha256sum --check
tar -xzf eksctl_$PLATFORM.tar.gz -C /tmp && rm eksctl_$PLATFORM.tar.gz
sudo install -m 0755 /tmp/eksctl /usr/local/bin && rm /tmp/eksctl
eksctl 是一個命令行工具,用於簡化 Amazon EKS(Elastic Kubernetes Service)集群的創建、管理和配置,讓你像開關燈一樣輕鬆操作 Kubernetes 集群!
到這裡就已經準備好後續我們要建置EKS基礎相關的工具啦~~
