在使用 Volatility 2 分析 Win10 記憶體時,會出現 Cannot find nt!ObGetObjectType 問題,需要傳入cookie 才能解決,今天會分享為什麼會出現這個問題,並且如何解決
下載連結:
Volatility 2 : https://github.com/volatilityfoundation/volatility
Volatility 3 : https://github.com/volatilityfoundation/volatility3
經典的記憶體分析工具,利用指令可以分析 memory dump 中的關鍵訊息,像是進程、網路連線、檔案......等等。
基本的操作這邊推薦可以直接上網查有人整理好的指令doc
而Volatility分為2與3版,差別就是一個是要使用 python2 執行,另一個是用 python3 執行,並且現在Volatility 2 已經沒有在維護了,但是一些 Plugin 的完整度在目前為止還是比 Volatility 3 還要高並且豐富,所以有些人還是會比較會偏向使用 Volatility 2 ,今天分享會主要使用 Volatility 2
如果你在 Win10 的記憶體 dump 使用 Volatility 2 的 psscan 時,有可能會出現以下的錯誤
$ vol.py -f MemoryDump.mem --profile=Win10x64_19041 psscan
Volatility Foundation Volatility Framework 2.6.1
Offset(P) Name PID PPID PDB Time created Time exited
------------------ ---------------- ------ ------ ------------------ ------------------------------ ------------------------------
WARNING : volatility.debug : Cannot find nt!ObGetObjectType
WARNING : volatility.debug : Cannot find nt!ObGetObjectType
Traceback (most recent call last):
File "/usr/local/bin/vol.py", line 192, in <module>
main()
File "/usr/local/bin/vol.py", line 183, in main
command.execute()
File "/usr/local/lib/python2.7/dist-packages/volatility/commands.py", line 147, in execute
func(outfd, data)
File "/usr/local/lib/python2.7/dist-packages/volatility/plugins/filescan.py", line 428, in render_text
for eprocess in data:
File "/usr/local/lib/python2.7/dist-packages/volatility/poolscan.py", line 252, in scan
skip_type_check = skip_type_check)
File "/usr/local/lib/python2.7/dist-packages/volatility/plugins/overlays/windows/windows.py", line 1258, in get_object
return self.get_object_top_down(struct_name, object_type, skip_type_check)
File "/usr/local/lib/python2.7/dist-packages/volatility/plugins/overlays/windows/windows.py", line 1231, in get_object_top_down
header.get_object_type() == object_type):
File "/usr/local/lib/python2.7/dist-packages/volatility/plugins/overlays/windows/win7.py", line 155, in get_object_type
return self.type_map.get(int(self.TypeIndex), '')
File "/usr/local/lib/python2.7/dist-packages/volatility/plugins/overlays/windows/win10.py", line 334, in TypeIndex
return ((addr >> 8) ^ cook ^ indx) & 0xFF
TypeError: unsupported operand type(s) for ^: 'int' and 'NoneType'
這個錯誤是因為win10.py 中在執行時在return ((addr >> 8) ^ cook ^ indx) & 0xFF這段程式出現了 NoneType 的變數。
根據這篇文章的分析,可以知道說 Win 10 的 TypeIndex 被混淆過,並且是根據
Index = TypeIndex ^ 2nd least significate byte of OBJECT_HEADER address ^ nt!ObHeaderCookie
這樣的公式進行混淆,nt!ObGetObjectType 的功用就是將TypeIndex 進行解混淆並回傳解混淆的TypeIndex。
因為 Volatility 2 是開源的,可以去看一下 win10.py 的sourcecode
class _OBJECT_HEADER_10(win8._OBJECT_HEADER):
@property
def TypeIndex(self):
"""Wrap the TypeIndex member with a property that decodes it
with the nt!ObHeaderCookie value."""
cook = obj.VolMagic(self.obj_vm).ObHeaderCookie.v()
addr = self.obj_offset
indx = int(self.m("TypeIndex"))
return ((addr >> 8) ^ cook ^ indx) & 0xFF
這邊就可以明顯的看到這三個變數分別代表什麼,並且利用這三個變數解混淆
那這邊就是因為 Volatlity2 讀不到 nt!ObHeaderCookie,因此 cookie 會是NoneType , 而如果你有在Volatility 2下過 -h 有可能會看過可以下--cookie。
$ vol.py -h
Volatility Foundation Volatility Framework 2.6.1
Usage: Volatility - A memory forensics analysis platform.
Options:
-h, --help list all available options and their default values.
Default values may be set in the configuration file
(/etc/volatilityrc)
--conf-file=/home/yunshiuan/.volatilityrc
User based configuration file
-d, --debug Debug volatility
--plugins=PLUGINS Additional plugin directories to use (colon separated)
--info Print information about all registered objects
--cache-directory=/home/yunshiuan/.cache/volatility
Directory where cache files are stored
--cache Use caching
--tz=TZ Sets the (Olson) timezone for displaying timestamps
using pytz (if installed) or tzset
-f FILENAME, --filename=FILENAME
Filename to use when opening an image
--profile=WinXPSP2x86
Name of the profile to load (use --info to see a list
of supported profiles)
-l LOCATION, --location=LOCATION
A URN location from which to load an address space
-w, --write Enable write support
--dtb=DTB DTB Address
--shift=SHIFT Mac KASLR shift address
--output=text Output in this format (support is module specific, see
the Module Output Options below)
--output-file=OUTPUT_FILE
Write output in this file
-v, --verbose Verbose information
--physical_shift=PHYSICAL_SHIFT
Linux kernel physical shift address
--virtual_shift=VIRTUAL_SHIFT
Linux kernel virtual shift address
-g KDBG, --kdbg=KDBG Specify a KDBG virtual address (Note: for 64-bit
Windows 8 and above this is the address of
KdCopyDataBlock)
--force Force utilization of suspect profile
-k KPCR, --kpcr=KPCR Specify a specific KPCR address
--cookie=COOKIE Specify the address of nt!ObHeaderCookie (valid for
Windows 10 only)
那這個就是讓我們放 nt!ObHeaderCookie 的 address 給 Volatility 2 , 因此接下來只要獲取到nt!ObHeaderCookie 位置的 cookie 應該就可以解決這個問題了。而 nt!ObHeaderCookie 在 ntoskrnl.exe 中可以找到。
因此我們現在要把memory 中的ntoskrnl.exe dump出來,volatility 2 有一個很猛的 moddump Plugin ,他可以將 Kernel Driver 全部 dump 出來
$ vol.py -f MemoryDump.mem --profile=Win10x64_19041 moddump --dump-dir ./
Volatility Foundation Volatility Framework 2.6.1
Module Base Module Name Result
------------------ -------------------- ------
0xfffff8076221a000 ntoskrnl.exe OK: driver.fffff8076221a000.sys
0xfffff80762070000 hal.dll OK: driver.fffff80762070000.sys
0xfffff80767340000 ucx01000.sys OK: driver.fffff80767340000.sys
0xfffff80764530000 NETIO.SYS OK: driver.fffff80764530000.sys
0xfffff80767570000 UsbHub3.sys OK: driver.fffff80767570000.sys
0xfffff80767020000 USBPORT.SYS OK: driver.fffff80767020000.sys
0xfffff80767db0000 vm3dmp.sys OK: driver.fffff80767db0000.sys
0xfffff807643c0000 ndis.sys OK: driver.fffff807643c0000.sys
0xfffff807679d0000 cldflt.sys OK: driver.fffff807679d0000.sys
0xfffff80767a80000 bindflt.sys OK: driver.fffff80767a80000.sys
0xfffff80763fe0000 EhStorClass.sys OK: driver.fffff80763fe0000.sys
0xfffff807635f0000 CI.dll OK: driver.fffff807635f0000.sys
0xfffff80763c00000 pdc.sys OK: driver.fffff80763c00000.sys
0xfffff80767af0000 rspndr.sys OK: driver.fffff80767af0000.sys
0xfffff80767210000 e1i65x64.sys OK: driver.fffff80767210000.sys
0xfffff80763e00000 vsock.sys OK: driver.fffff80763e00000.sys
0xfffff80767440000 rdpbus.sys OK: driver.fffff80767440000.sys
0xfffff80774a50000 tcpipreg.sys OK: driver.fffff80774a50000.sys
0xfffff8077a5f0000 ad_driver.10.sys OK: driver.fffff8077a5f0000.sys
0xfffff80765670000 cdrom.sys OK: driver.fffff80765670000.sys
0xfffff80774c80000 mpsdrv.sys OK: driver.fffff80774c80000.sys
0xfffff80763eb0000 storahci.sys OK: driver.fffff80763eb0000.sys
0xfffff8077a4c0000 condrv.sys OK: driver.fffff8077a4c0000.sys
0xfffff80765ad0000 watchdog.sys OK: driver.fffff80765ad0000.sys
0xfffff807656f0000 Beep.SYS OK: driver.fffff807656f0000.sys
0xfffff80764b70000 mup.sys OK: driver.fffff80764b70000.sys
0xfffff80767d90000 serenum.sys OK: driver.fffff80767d90000.sys
0xfffff80763b50000 msisadrv.sys OK: driver.fffff80763b50000.sys
0xfffff80762160000 FLTMGR.SYS OK: driver.fffff80762160000.sys
0xfffff80767390000 vmgencounter.sys OK: driver.fffff80767390000.sys
0xfffff80763fb0000 stornvme.sys OK: driver.fffff80763fb0000.sys
0xfffff807635c0000 werkernel.sys OK: driver.fffff807635c0000.sys
0xfffff80765720000 dxgkrnl.sys OK: driver.fffff80765720000.sys
0xfffff807637f0000 WMILIB.SYS OK: driver.fffff807637f0000.sys
0xfffff80763d90000 volmgrx.sys Error: Cannot acquire AS
0xfffff80774a20000 Ndu.sys OK: driver.fffff80774a20000.sys
0xfffff80763ef0000 storport.sys OK: driver.fffff80763ef0000.sys
0xfffff80767990000 wcifs.sys OK: driver.fffff80767990000.sys
0xfffff80763c50000 partmgr.sys OK: driver.fffff80763c50000.sys
0xfffff80767870000 dxgmms2.sys OK: driver.fffff80767870000.sys
0xfffff80766e80000 kdnic.sys OK: driver.fffff80766e80000.sys
0xfffff80767b70000 peauth.sys OK: driver.fffff80767b70000.sys
0xfffff80764aa0000 volsnap.sys OK: driver.fffff80764aa0000.sys
0xfffff80763b10000 IntelTA.sys OK: driver.fffff80763b10000.sys
0xfffff807676c0000 HIDPARSE.SYS OK: driver.fffff807676c0000.sys
0xfffff80767cd0000 umbus.sys OK: driver.fffff80767cd0000.sys
0xfffff80767720000 dump_storport.sys OK: driver.fffff80767720000.sys
0xfffff807673b0000 BATTC.SYS OK: driver.fffff807673b0000.sys
0xfffff80766da0000 dfsc.sys OK: driver.fffff80766da0000.sys
0xfffff80763b20000 WindowsTr...roxy.sys OK: driver.fffff80763b20000.sys
0xfffff80764b10000 rdyboost.sys OK: driver.fffff80764b10000.sys
0xfffff80763d50000 PCIIDEX.SYS OK: driver.fffff80763d50000.sys
0xfffff80766f80000 afunix.sys OK: driver.fffff80766f80000.sys
0xfffff80767da0000 vm3dmp_loader.sys OK: driver.fffff80767da0000.sys
0xfffff80764ba0000 iorate.sys OK: driver.fffff80764ba0000.sys
0xfffff80767420000 NdisVirtualBus.sys OK: driver.fffff80767420000.sys
0xfffff80766dd0000 CompositeBus.sys OK: driver.fffff80766dd0000.sys
0xfffff80774a00000 mmcss.sys OK: driver.fffff80774a00000.sys
0xfffff80764000000 fileinfo.sys OK: driver.fffff80764000000.sys
0xfffff80764610000 tcpip.sys OK: driver.fffff80764610000.sys
0xfffff807637a0000 WDFLDR.SYS OK: driver.fffff807637a0000.sys
0xfffff80766c20000 rdbss.sys OK: driver.fffff80766c20000.sys
0xfffff80762080000 kdcom.dll OK: driver.fffff80762080000.sys
0xfffff80766ca0000 csc.sys OK: driver.fffff80766ca0000.sys
0xfffffb54a32b0000 win32k.sys Error: Cannot acquire AS
0xfffff807674e0000 USBD.SYS OK: driver.fffff807674e0000.sys
0xfffffb54a2c00000 win32kbase.sys OK: driver.fffffb54a2c00000.sys
0xfffff80763af0000 WindowsTrustedRT.sys OK: driver.fffff80763af0000.sys
0xfffff80774ca0000 mrxsmb.sys OK: driver.fffff80774ca0000.sys
0xfffff80767d20000 kbdclass.sys OK: driver.fffff80767d20000.sys
0xfffff80766d40000 nsiproxy.sys OK: driver.fffff80766d40000.sys
0xfffff80767560000 ksthunk.sys OK: driver.fffff80767560000.sys
0xfffff80765b70000 crashdmp.sys OK: driver.fffff80765b70000.sys
0xfffff80763b30000 pcw.sys OK: driver.fffff80763b30000.sys
0xfffff807643b0000 Fs_Rec.sys Error: Cannot acquire AS
0xfffff807649c0000 fvevol.sys OK: driver.fffff807649c0000.sys
0xfffff807635e0000 ntosext.sys OK: driver.fffff807635e0000.sys
0xfffff80764c00000 CLASSPNP.SYS OK: driver.fffff80764c00000.sys
0xfffff80766bf0000 winhvr.sys OK: driver.fffff80766bf0000.sys
0xfffff80762130000 PSHED.dll OK: driver.fffff80762130000.sys
0xfffff80763e20000 vmci.sys OK: driver.fffff80763e20000.sys
0xfffff80767430000 swenum.sys OK: driver.fffff80767430000.sys
0xfffff80767660000 hidusb.sys OK: driver.fffff80767660000.sys
0xfffff80766b20000 netbios.sys OK: driver.fffff80766b20000.sys
0xfffff80766ea0000 CimFS.SYS OK: driver.fffff80766ea0000.sys
0xfffff80774ac0000 HTTP.sys OK: driver.fffff80774ac0000.sys
0xfffff80767ab0000 lltdio.sys OK: driver.fffff80767ab0000.sys
0xfffff807670d0000 portcls.sys OK: driver.fffff807670d0000.sys
0xfffff807656e0000 Null.SYS Error: Cannot acquire AS
0xfffff80767cf0000 i8042prt.sys OK: driver.fffff80767cf0000.sys
0xfffff80763910000 mssecflt.sys OK: driver.fffff80763910000.sys
0xfffff80766f20000 netbt.sys OK: driver.fffff80766f20000.sys
0xfffff80766b40000 Vid.sys OK: driver.fffff80766b40000.sys
0xfffff80762150000 BOOTVID.dll OK: driver.fffff80762150000.sys
0xfffff80767760000 dump_stornvme.sys OK: driver.fffff80767760000.sys
0xfffff80763d70000 volmgr.sys OK: driver.fffff80763d70000.sys
0xfffff80763990000 ACPI.sys OK: driver.fffff80763990000.sys
0xfffff807636e0000 cng.sys OK: driver.fffff807636e0000.sys
0xfffff80766fa0000 ahcache.sys OK: driver.fffff80766fa0000.sys
0xfffff80774d90000 vmmemctl.sys OK: driver.fffff80774d90000.sys
0xfffff80767b10000 msquic.sys OK: driver.fffff80767b10000.sys
0xfffff807621d0000 cmimcext.sys OK: driver.fffff807621d0000.sys
0xfffff80766df0000 fastfat.SYS OK: driver.fffff80766df0000.sys
0xfffff80763400000 clipsp.sys OK: driver.fffff80763400000.sys
0xfffff807637c0000 SleepStudyHelper.sys OK: driver.fffff807637c0000.sys
0xfffff80764020000 Wof.sys OK: driver.fffff80764020000.sys
0xfffff80763e70000 ataport.SYS OK: driver.fffff80763e70000.sys
0xfffff80764a90000 volume.sys OK: driver.fffff80764a90000.sys
0xfffff807670a0000 HDAudBus.sys OK: driver.fffff807670a0000.sys
0xfffff807656b0000 filecrypt.sys OK: driver.fffff807656b0000.sys
0xfffff807638e0000 acpiex.sys OK: driver.fffff807638e0000.sys
0xfffff80766ef0000 TDI.SYS OK: driver.fffff80766ef0000.sys
0xfffff8077a4e0000 vmhgfs.sys OK: driver.fffff8077a4e0000.sys
0xfffff80765b10000 BasicRender.sys OK: driver.fffff80765b10000.sys
0xfffff80767d50000 mouclass.sys OK: driver.fffff80767d50000.sys
0xfffff80763d40000 intelide.sys OK: driver.fffff80763d40000.sys
0xfffffb54a3350000 cdd.dll Error: Cannot acquire AS
0xfffff80767960000 luafv.sys OK: driver.fffff80767960000.sys
0xfffff80774c50000 bowser.sys OK: driver.fffff80774c50000.sys
0xfffff807676e0000 mouhid.sys OK: driver.fffff807676e0000.sys
0xfffff807677b0000 dump_dumpfve.sys OK: driver.fffff807677b0000.sys
0xfffff807673d0000 intelppm.sys OK: driver.fffff807673d0000.sys
0xfffff80765be0000 Msfs.SYS OK: driver.fffff80765be0000.sys
0xfffff8077a550000 WdFilter.sys OK: driver.fffff8077a550000.sys
0xfffff80766ff0000 tap0901.sys OK: driver.fffff80766ff0000.sys
0xfffff80774da0000 srvnet.sys OK: driver.fffff80774da0000.sys
0xfffff807640d0000 Ntfs.sys OK: driver.fffff807640d0000.sys
0xfffff80763e40000 mountmgr.sys OK: driver.fffff80763e40000.sys
0xfffff80767450000 usbhub.sys OK: driver.fffff80767450000.sys
0xfffff80767a60000 storqosflt.sys OK: driver.fffff80767a60000.sys
0xfffff80767680000 HIDCLASS.SYS OK: driver.fffff80767680000.sys
0xfffff80763c90000 spaceport.sys OK: driver.fffff80763c90000.sys
0xfffff807672a0000 USBXHCI.SYS OK: driver.fffff807672a0000.sys
0xfffff80766ec0000 tdx.sys OK: driver.fffff80766ec0000.sys
0xfffff80766ad0000 pacer.sys OK: driver.fffff80766ad0000.sys
0xfffff80765700000 vmrawdsk.sys OK: driver.fffff80765700000.sys
0xfffff80767000000 usbuhci.sys OK: driver.fffff80767000000.sys
0xfffff80763550000 msrpc.sys Error: Cannot acquire AS
0xfffff80763b60000 pci.sys OK: driver.fffff80763b60000.sys
0xfffff80767ad0000 mslldp.sys OK: driver.fffff80767ad0000.sys
0xfffff80767170000 ks.sys OK: driver.fffff80767170000.sys
0xfffff80766d90000 gpuenergydrv.sys OK: driver.fffff80766d90000.sys
0xfffff807673a0000 CmBatt.sys OK: driver.fffff807673a0000.sys
0xfffff807645d0000 ksecpkg.sys OK: driver.fffff807645d0000.sys
0xfffff80763be0000 vdrvroot.sys OK: driver.fffff80763be0000.sys
0xfffff807671f0000 usbehci.sys OK: driver.fffff807671f0000.sys
0xfffff80763800000 Wdf01000.sys OK: driver.fffff80763800000.sys
0xfffff80764be0000 disk.sys OK: driver.fffff80764be0000.sys
0xfffff80766d70000 mssmbios.sys OK: driver.fffff80766d70000.sys
0xfffff80774d40000 mrxsmb20.sys OK: driver.fffff80774d40000.sys
0xfffff807677d0000 dxgmms1.sys OK: driver.fffff807677d0000.sys
0xfffff80767d70000 serial.sys OK: driver.fffff80767d70000.sys
0xfffff80766ab0000 vwififlt.sys OK: driver.fffff80766ab0000.sys
0xfffff807620c0000 CLFS.SYS OK: driver.fffff807620c0000.sys
0xfffff807656d0000 tbs.sys OK: driver.fffff807656d0000.sys
0xfffff80764900000 fwpkclnt.sys OK: driver.fffff80764900000.sys
0xfffff80766f10000 ws2ifsl.sys OK: driver.fffff80766f10000.sys
0xfffff80763520000 ksecdd.sys OK: driver.fffff80763520000.sys
0xfffff80765b30000 Npfs.SYS OK: driver.fffff80765b30000.sys
0xfffff80767140000 drmk.sys OK: driver.fffff80767140000.sys
0xfffff80766d60000 npsvctrig.sys OK: driver.fffff80766d60000.sys
0xfffff80764980000 wfplwfs.sys OK: driver.fffff80764980000.sys
0xfffff80767d40000 vmmouse.sys OK: driver.fffff80767d40000.sys
0xfffff807637d0000 WppRecorder.sys OK: driver.fffff807637d0000.sys
0xfffff80761de0000 mcupdate.dll OK: driver.fffff80761de0000.sys
0xfffff8077a3f0000 srv2.sys OK: driver.fffff8077a3f0000.sys
0xfffff80766a00000 afd.sys OK: driver.fffff80766a00000.sys
0xfffff80763970000 SgrmAgent.sys OK: driver.fffff80763970000.sys
0xfffff80767620000 usbccgp.sys OK: driver.fffff80767620000.sys
0xfffff80763c30000 CEA.sys OK: driver.fffff80763c30000.sys
0xfffff80767700000 vmusbmouse.sys OK: driver.fffff80767700000.sys
0xfffff80767850000 monitor.sys OK: driver.fffff80767850000.sys
0xfffff80763e60000 atapi.sys OK: driver.fffff80763e60000.sys
0xfffff80763a80000 intelpep.sys OK: driver.fffff80763a80000.sys
0xfffff80762090000 tm.sys OK: driver.fffff80762090000.sys
0xfffff80766e60000 bam.sys OK: driver.fffff80766e60000.sys
0xfffffb54a2ee0000 win32kfull.sys Error: Cannot acquire AS
0xfffff807674f0000 HdAudio.sys OK: driver.fffff807674f0000.sys
0xfffff80766b00000 ndiscap.sys OK: driver.fffff80766b00000.sys
0xfffff80765af0000 BasicDisplay.sys OK: driver.fffff80765af0000.sys
第一個就是ntoskrnl.exe ,把它拿去反編譯之後找到 ObGetObjectType 接下來把前面的8 bytes 的 opcode 記住
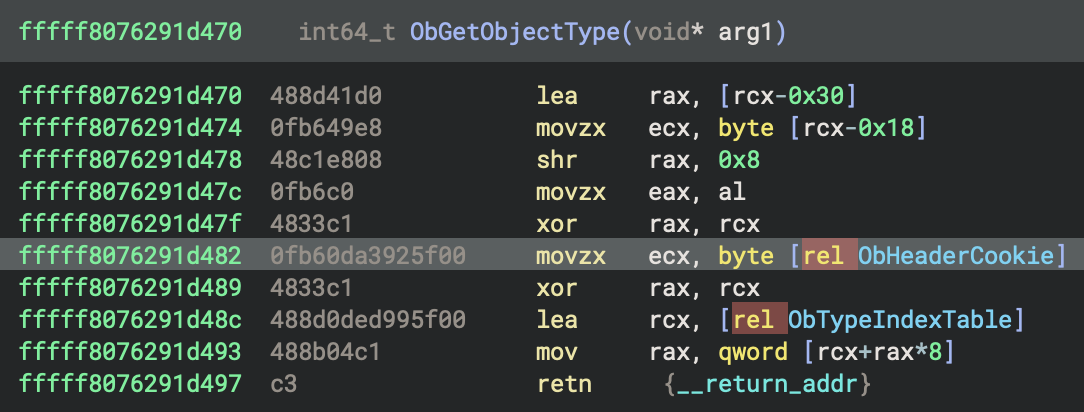
接下來用yarascan 把他從記憶體中的位置抓出來
$ sudo python2.7 vol.py -f ../temp_extract_dir/MemoryDump.mem --profile=Win10x64_19041 yarascan -K -Y "{48 8D 41 D0 0F B6 49 E8}"
Volatility Foundation Volatility Framework 2.6.1
Rule: r1
Owner: ntoskrnl.exe
0xf8076291d470 48 8d 41 d0 0f b6 49 e8 48 c1 e8 08 0f b6 c0 48 H.A...I.H......H
0xf8076291d480 33 c1 0f b6 0d a3 92 5f 00 48 33 c1 48 8d 0d ed 3......_.H3.H...
0xf8076291d490 99 5f 00 48 8b 04 c1 c3 cc cc cc cc cc cc cc cc ._.H............
0xf8076291d4a0 48 83 ec 58 8a 84 24 a0 00 00 00 c7 44 24 48 01 H..X..$.....D$H.
0xf8076291d4b0 00 00 00 88 44 24 40 8b 84 24 98 00 00 00 89 44 ....D$@..$.....D
0xf8076291d4c0 24 38 8b 84 24 90 00 00 00 89 44 24 30 48 8b 84 $8..$.....D$0H..
0xf8076291d4d0 24 88 00 00 00 48 89 44 24 28 48 8b 84 24 80 00 $....H.D$(H..$..
0xf8076291d4e0 00 00 48 89 44 24 20 e8 14 00 00 00 48 83 c4 58 ..H.D$......H..X
0xf8076291d4f0 c3 cc cc cc cc cc cc cc cc cc cc cc cc cc cc cc ................
0xf8076291d500 4c 8b dc 49 89 5b 08 49 89 73 10 4d 89 4b 20 4d L..I.[.I.s.M.K.M
0xf8076291d510 89 43 18 57 41 54 41 55 41 56 41 57 48 83 ec 70 .C.WATAUAVAWH..p
0xf8076291d520 48 8b da 48 8b f9 45 33 ed 4d 89 6b b0 4d 89 6b H..H..E3.M.k.M.k
0xf8076291d530 b8 65 48 8b 04 25 88 01 00 00 48 89 44 24 60 44 .eH..%....H.D$`D
0xf8076291d540 8a b8 32 02 00 00 45 84 ff 0f 84 07 94 12 00 49 ..2...E........I
0xf8076291d550 8b 4b 28 48 b8 00 00 ff ff ff 7f 00 00 48 3b c8 .K(H.........H;.
0xf8076291d560 48 0f 43 c8 8b 01 89 01 44 8b a4 24 d0 00 00 00 H.C.....D..$....
接下來知道 ntoskrnl.exe 的位置在0xf8076291d470後我們就可以寫 script 幫我我們提取ObHeaderCookie
回去看反編譯出來的ObGetObjectType,我們的目標是movzx ecx, byte [rel ObHeaderCookie] 這段
$ sudo python2.7 vol.py -f ../temp_extract_dir/MemoryDump.mem --profile=Win10x64_19041 volshell
Volatility Foundation Volatility Framework 2.6.1
Current context: System @ 0xffffad8185883180, pid=4, ppid=0 DTB=0x1ad002
Welcome to volshell! Current memory image is:
file:///home/yunshiuan/temp_extract_dir/MemoryDump.mem
To get help, type 'hh()'
>>> addr = 0xf8076291d470
>>> for m in getmods():
... nt_mod = m
... break
...
>>> mode = distorm3.Decode64Bits
>>> data = nt_mod.obj_vm.read(addr, 100)
>>> ops = distorm3.Decompose(addr, data, mode)
>>> for op in reversed(ops):
... if (op.size == 7 and 'FLAG_RIP_RELATIVE' in op.flags and len(op.operands) == 2 and op.operands[0].type == 'Register' and op.operands[1].type == 'AbsoluteMemory' and op.operands[1].size == 8):
... addr2 = op.address + op.size + op.operands[1].disp
...
>>> cookie = obj.Object("unsigned int", offset = addr2, vm = nt_mod.obj_vm)
>>> hex(cookie)
'0x9be88324L'
>>> exit()
這個script 簡單來說
movzx ecx, byte [rel ObHeaderCookie]指令
op.size == 7:指令長度為 7 位元組'FLAG_RIP_RELATIVE' in op.flags:使用 RIP相對定址len(op.operands) == 2:有 2 個運算元op.operands[0].type== 'Register':第一個運算元是暫存器op.operands[1].type == 'AbsoluteMemory':第二個運算元是記憶體位址op.operands[1].size== 8:記憶體運算元大小為 8 位元組addr2 = op.address + op.size + op.operands[1].disp
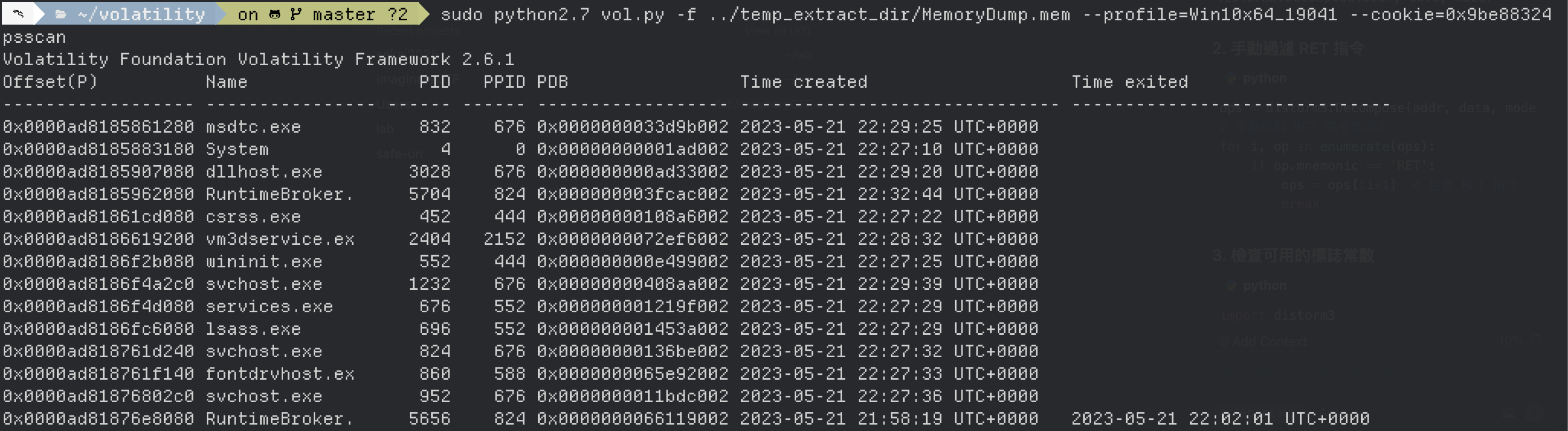
提取後我們知道cookie 的值為0x9be88324,最後再下一次 psscan 帶上剛剛抓的cookie
sudo python2.7 vol.py -f ../temp_extract_dir/MemoryDump.mem --profile=Win10x64_19041 --cookie=0x9be88324 psscan
發現成功執行
其實今天分享了的這個問題,但是其實只要改用Volatility 3 就都不會有問題了,而且在研究這個問題的過程中因為 Volatility 2 支援的函式庫都太舊了導致踩了不少坑,所以今天的分享如果你是 Volatility 2 的忠實信徒,這個方式應該可以幫助你在分析 Win 10 的記憶體時遇到這個問題可以直接解決
https://www.osdfcon.org/presentations/2020/Jamie-Levy_Troubleshooting-Memory.pdf
https://github.com/volatilityfoundation/volatility/issues/436
