今天會介紹另一個network forensic 工具-Zui ,另外也會介紹一下 Zui 當中使用到的 Zeek 以及Suricata pcap分析工具
下載連結:https://zui.brimdata.io/docs
Zui 它的前身是Brim , 是一款用於網路流量分析的工具,它提供了使用者友善的圖形化介面,可以讓使用者能夠快速分析與視覺化大量網路流量
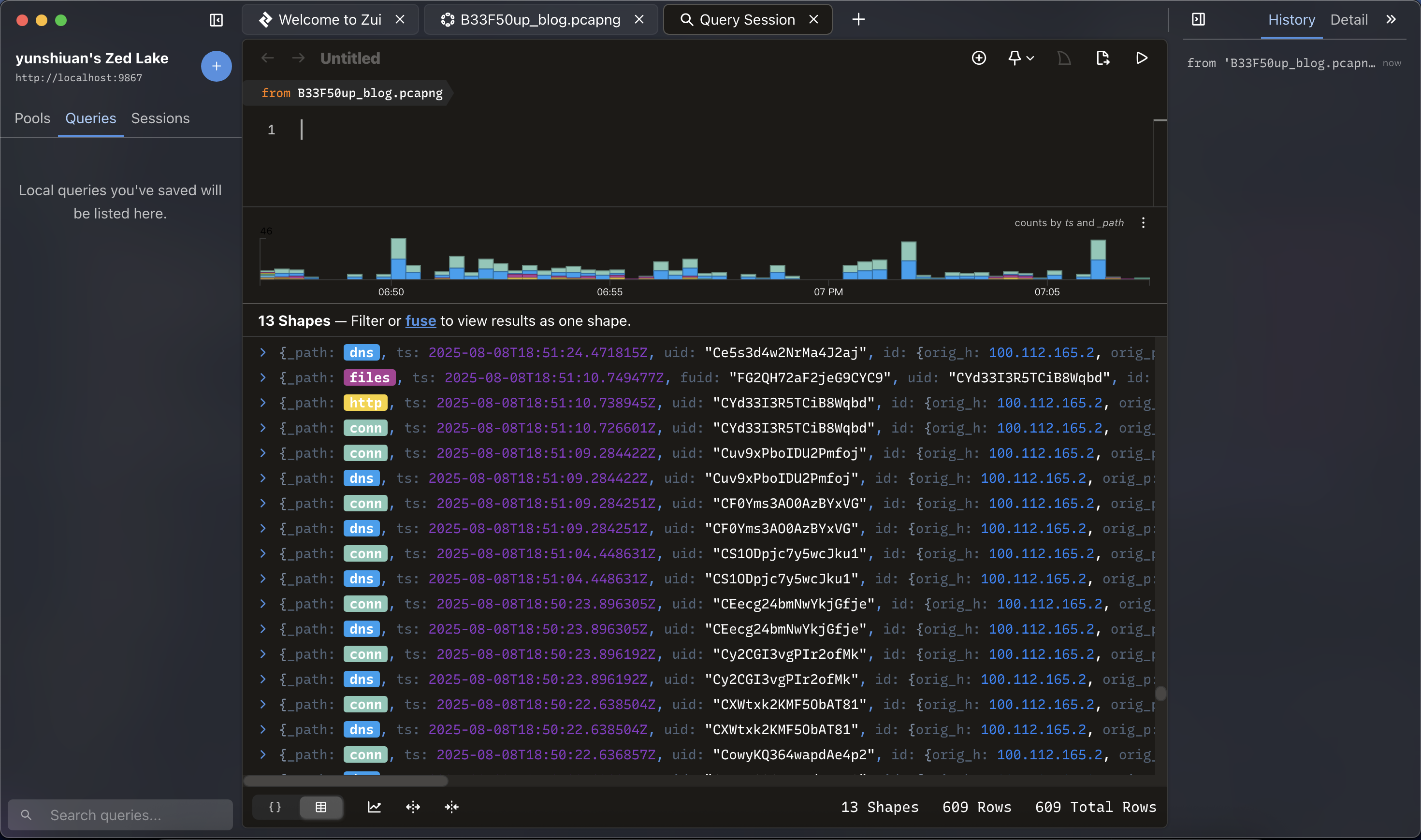
這個工具裡面整合了兩個網路封包分析工具,分別是Zeek、Suricata
連結:https://github.com/zeek/zeek
Zeek 是一個開源的網路安全監控工具,以強大的資料記錄功能聞名。它能將原始的 pcap 封包檔轉換成結構化的日誌,方便在 Zeek 內查詢與分析,快速提供網路行為的概覽。
指令如下
zeek -C -r B33F50up_blog.pcapng
他會產生以下檔案
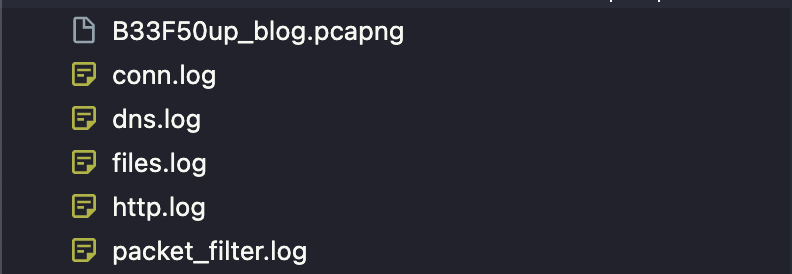
以下是http.log 的形式
#separator \x09
#set_separator ,
#empty_field (empty)
#unset_field -
#path http
#open 2025-09-27-22-26-52
#fields ts uid id.orig_h id.orig_p id.resp_h id.resp_p trans_depth method host uri referrer version user_agent origin request_body_len response_body_len status_code status_msg info_code info_msg tags username password proxied orig_fuids orig_filenames orig_mime_types resp_fuids resp_filenames resp_mime_types
#types time string addr port addr port count string string string string string string string count count count string count string set[enum] string string set[string] vector[string] vector[string] vector[string] vector[string] vector[string] vector[string]
1754678828.272075 CAuRo91flufxXutAke 100.112.165.2 60665 192.168.1.125 5000 1 GET 192.168.1.125:5000 / - 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 - 0 24859 200 OK - - (empty) - - - - - - FA9Bk7Ikrr1LVrys - text/html
1754678857.820963 CIRhMK1X97Z1MzFRD1 100.112.165.2 60676 192.168.1.125 5000 1 POST 192.168.1.125:5000 /ping http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 15 727 200 OK - - (empty) - - - FIUrzJ3sbt6deYBXf3 - text/plain FyILV9CHbcmUMGtc6 - text/json
1754678865.293310 CZnidTF5LIgaMzbRe 100.112.165.2 60677 192.168.1.125 5000 1 POST 192.168.1.125:5000 /system http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 141 185 200 OK - - (empty) - - - Fvs6lg41SIyuYsReh2 - - FqFYD91bNrEWRNR501 - text/json
1754679070.738945 CWlCIn4qK2ntw6CuJl 100.112.165.2 60757 192.168.1.125 5000 1 GET 192.168.1.125:5000 / - 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 - 0 24859 200 OK - - (empty) - - - - - - FG2QH72aF2jeG9CYC9 - text/html
1754679165.228123 C5V1Fn3nYAvFuSQeE 100.112.165.2 60778 192.168.1.125 5000 1 POST 192.168.1.125:5000 /system http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 141 287 200 OK - - (empty) - - - FnwtMr2TZ1qIS6LLmj - - Fq827u4xABcX563I21 - text/json
1754679173.669096 CWXpsv3zrBE7Lx66Sg 100.112.165.2 60779 192.168.1.125 5000 1 POST 192.168.1.125:5000 /system http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 144 13177 200 OK - - (empty) - - - FxvTqN3Pid7VWQP7y3 - - Fi4rGH32Y4P77kznf3 - text/json
1754679180.268390 Co6odn3WTbf9HKGcO6 100.112.165.2 60780 192.168.1.125 5000 1 POST 192.168.1.125:5000 /ping http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 15 728 200 OK - - (empty) - - - FYW00SjDihqYC30xe - text/plain FQGbYm3SH1rsO8o9ng - text/json
1754679196.383809 CGjLWoznypKV0Pgt 100.112.165.2 60809 192.168.1.125 5000 1 POST 192.168.1.125:5000 /ping http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 16 738 200 OK - - (empty) - - - FVCJDglco6ai9lzi4 - text/plain FB2a4L3x3ZELSSdCQ1 - text/json
1754679223.696243 C0s1KA7ZrfQvnIpj 100.112.165.2 60865 192.168.1.125 5000 1 POST 192.168.1.125:5000 /ping http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 30 851 200 OK - - (empty) - - - FA2p79sD6MkhyaCEb - text/plain FwUGICEULGQRyBs78 - text/json
1754679257.891805 CtwrhY2Kw9bscBOsX7 100.112.165.2 60874 192.168.1.125 5000 1 POST 192.168.1.125:5000 /ping http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 34 755 200 OK - - (empty) - - - FybSTDKXBk5dCiaYl - text/plain F55jsD1S1vWW8IVBY4 - text/json
1754679265.650887 CFgfqH2IasZxXsovkd 100.112.165.2 60875 192.168.1.125 5000 1 POST 192.168.1.125:5000 /ping http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 30 869 200 OK - - (empty) - - - FtvRcZ3D5kRIP1ijy5 - text/plain FTYdr5iKtJX11Efma - text/json
1754679315.090163 CEAuN63ly0lHS2zRrj 100.112.165.2 60895 192.168.1.125 5000 1 POST 192.168.1.125:5000 /ping http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 30 869 200 OK - - (empty) - - - Fyt7jP30AEKPs4C0Uj - text/plain F0zHt852ycC25Gpkf - text/json
1754679319.217264 CRWcyt2bda4K3g6Xub 100.112.165.2 60912 192.168.1.125 5000 1 POST 192.168.1.125:5000 /ping http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 36 900 200 OK - - (empty) - - - FUAgus1sr4pPeGnidg - text/plain FqnOWw20dfXD0koyIi - text/json
1754679354.845803 CulPOq3A9IP8ab4Zqd 100.112.165.2 60981 192.168.1.125 5000 1 POST 192.168.1.125:5000 /ping http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 48 769 200 OK - - (empty) - - - FZw17aZHAnZltVkJ - text/plain FQvAYSOVPIbUCfRm7 - text/json
1754679406.575000 C9iy0scrJKJuDpi07 100.112.165.2 61207 192.168.1.125 5000 1 POST 192.168.1.125:5000 /ping http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 49 2621 200 OK - - (empty) - - - FiejrYnJjwTaJ5db7 - text/plain FKZoSb4yddnL4uzkZf - text/json
1754679827.575533 CV2dqm3aNuGOi4EC0h 100.112.165.2 63113 192.168.1.125 5000 1 POST 192.168.1.125:5000 /ping http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 36 912 200 OK - - (empty) - - - FDaXYp2bh8hJpHMYCi - text/plain FdsBU41nDrcCQ9mTV9 - text/json
1754679851.757452 CWSzgl4AsTyJVyRpJf 100.112.165.2 63213 192.168.1.125 5000 1 POST 192.168.1.125:5000 /ping http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 44 800 200 OK - - (empty) - - - FAGwfWDdjCLhcrZX2 - text/plain F89dhl1uFy7r4oRtf - text/json
1754679859.655497 C0LErP2jTxCqKmUESd 100.112.165.2 63216 192.168.1.125 5000 1 POST 192.168.1.125:5000 /ping http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 47 781 200 OK - - (empty) - - - FoNYJj2QlLyZkd9tEe - text/plain FUaGCH2RbcOlDQcaOi - text/json
1754679875.655339 CqC0qj2SMoQnSfaju6 100.112.165.2 63217 192.168.1.125 5000 1 POST 192.168.1.125:5000 /ping http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 31 762 200 OK - - (empty) - - - FRGjia4iHeyPzIDRC3 - text/plain FwGgDTGi2gHDik2P5 - text/json
1754679999.499748 CtN1Vk4RrwIRGOgwHc 100.112.165.2 63280 192.168.1.125 5000 1 POST 192.168.1.125:5000 /ping http://192.168.1.125:5000/ 1.1 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 http://192.168.1.125:5000 142 836 200 OK - - (empty) - - - FFJx4j4PnbpIi0mfD6 - text/plain FYpDmc37JMpCuz4Zac - text/json
#close 2025-09-27-22-26-52
另外他也會根據 pcap 檔產生其他log ,參考網址:https://docs.zeek.org/en/master/logs/index.html
連結:https://suricata.io/
Suricata 是一個開源的入侵偵測系統(IDS)與入侵防禦系統(IPS),以深度封包檢測、流量分析與威脅偵測聞名。能使用 Suricata 的龐大規則集快速評估網路資料並辨識異常。
指令如下
suricata -r B33F50up_blog.pcapng
他會產生四個檔案
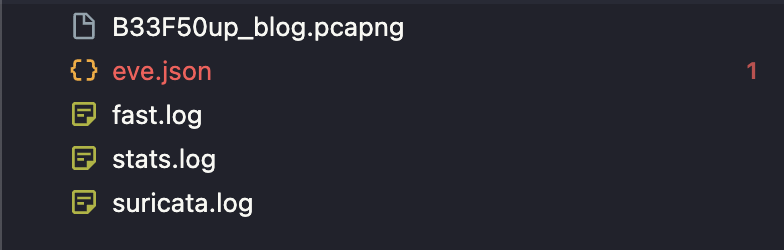
以下是 fast.log 資訊
08/09/2025-02:53:47.165861 [**] [1:2019284:3] ET ATTACK_RESPONSE Output of id command from HTTP server [**] [Classification: Potentially Bad Traffic] [Priority: 2] {TCP} 192.168.1.125:5000 -> 100.112.165.2:60865
08/09/2025-02:56:49.767871 [**] [1:2002034:13] ET ATTACK_RESPONSE Possible /etc/passwd via HTTP (linux style) [**] [Classification: Information Leak] [Priority: 2] {TCP} 192.168.1.125:5000 -> 100.112.165.2:61207
總結來說 Zui 的做法是先用 brimcap 將 pcap 送到 Zeek/Suricata 做 summary/log,在 Zui 內用 correlation view、alert 視窗、或 detail pane 分析事件與原始封包。
所以只要將pcap 封包丟進去 zeek ,他就會開始進行分析
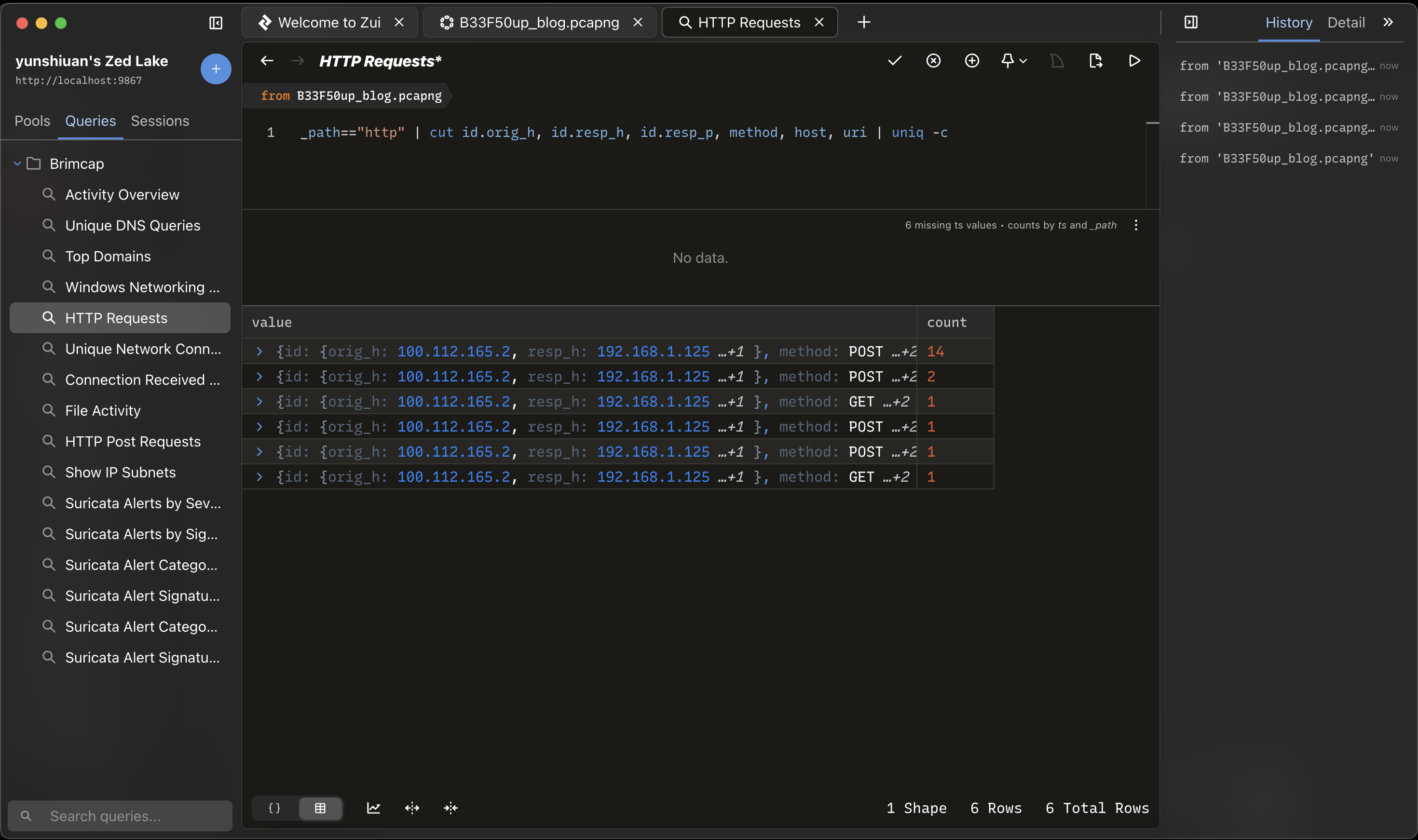
分析完後按下Query Pool 就可以看到視覺化的頁面

另外 Zui 使用 Zed(或稱 Zed query / SuperSQL)來做過濾與轉換查詢可以更快處理大量資料
以下分享幾個操作
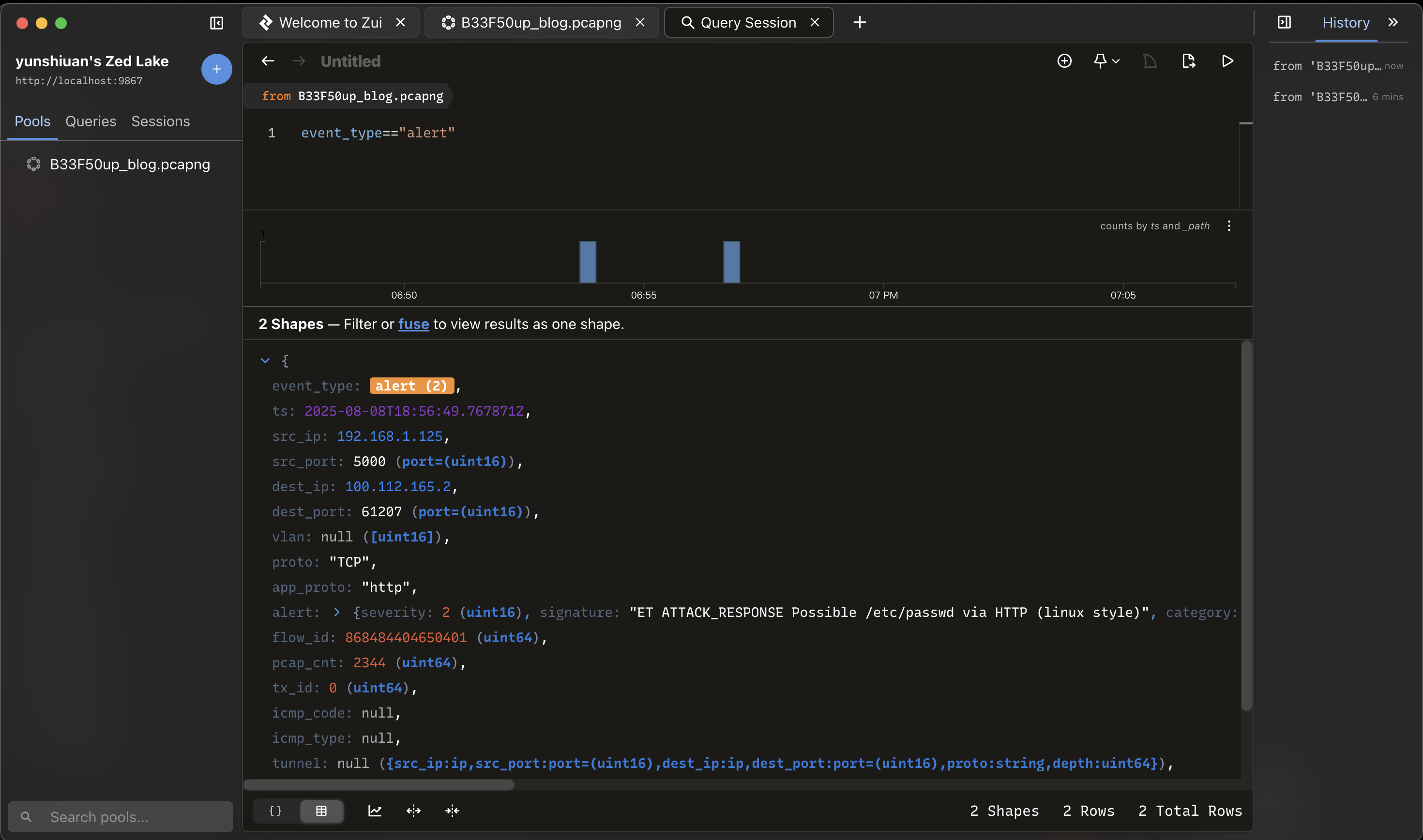
首先可以篩選出Suricata 警報
event_type=="alert" #可篩選出 Suricata 警報
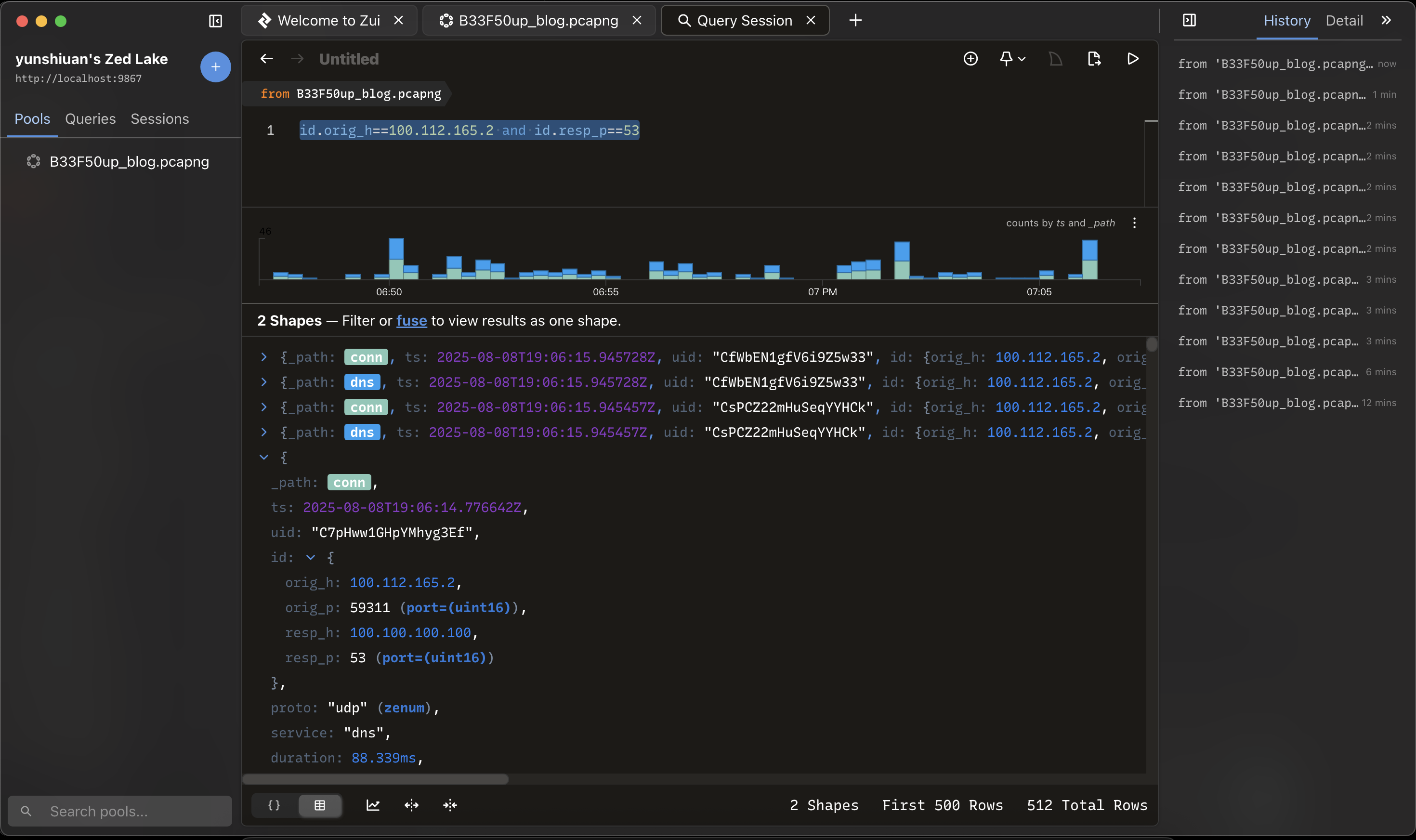
也有像wireshark 一樣可以篩選 ip scr or ip dst
id.orig_h==100.112.165.2 and id.resp_p==53 #來源ip = 100.112.165.2 目標port = 53
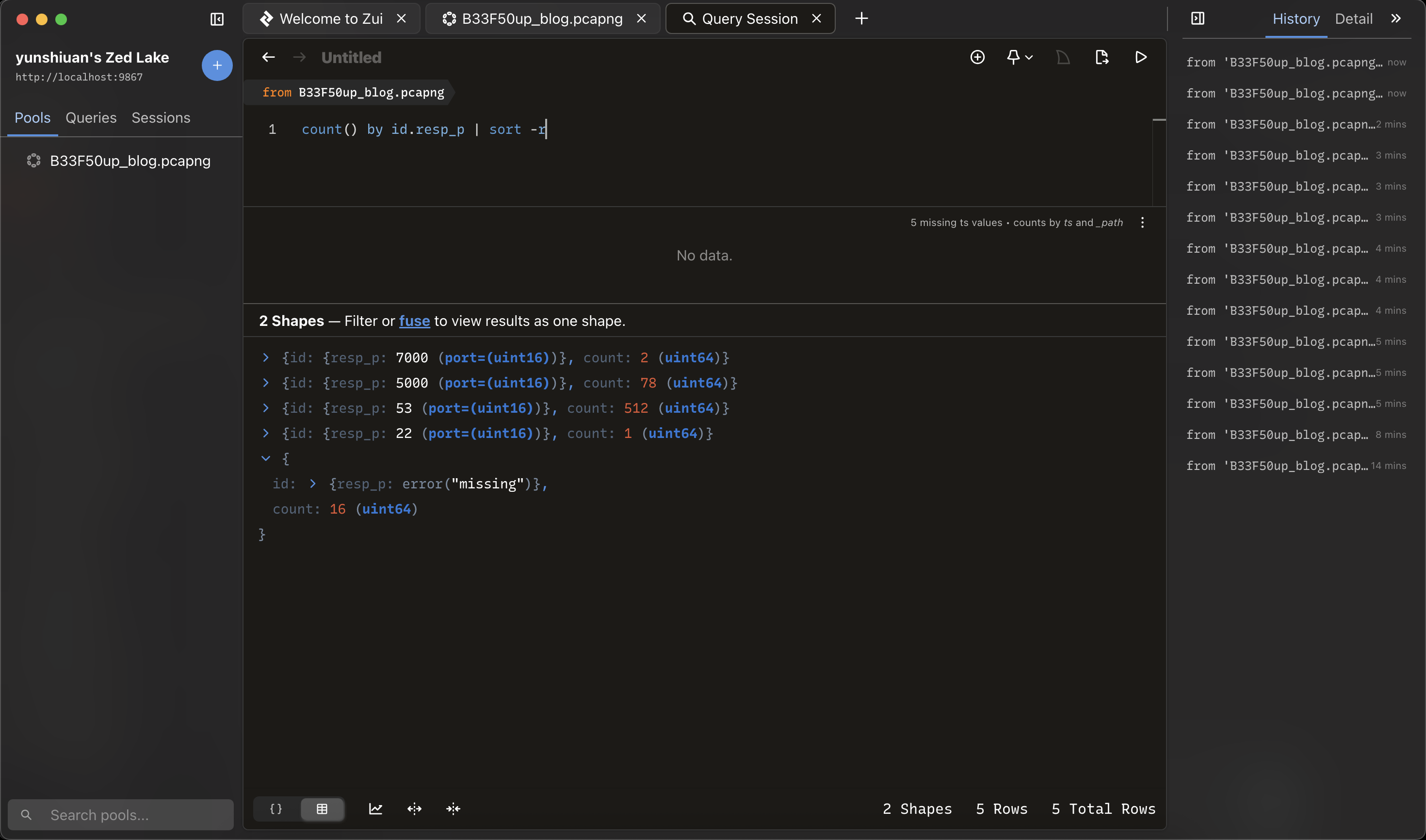
另外他也可以進行統計與排序
count() by id.resp_p | sort -r # 對目標port 進行統計,並降冪排序
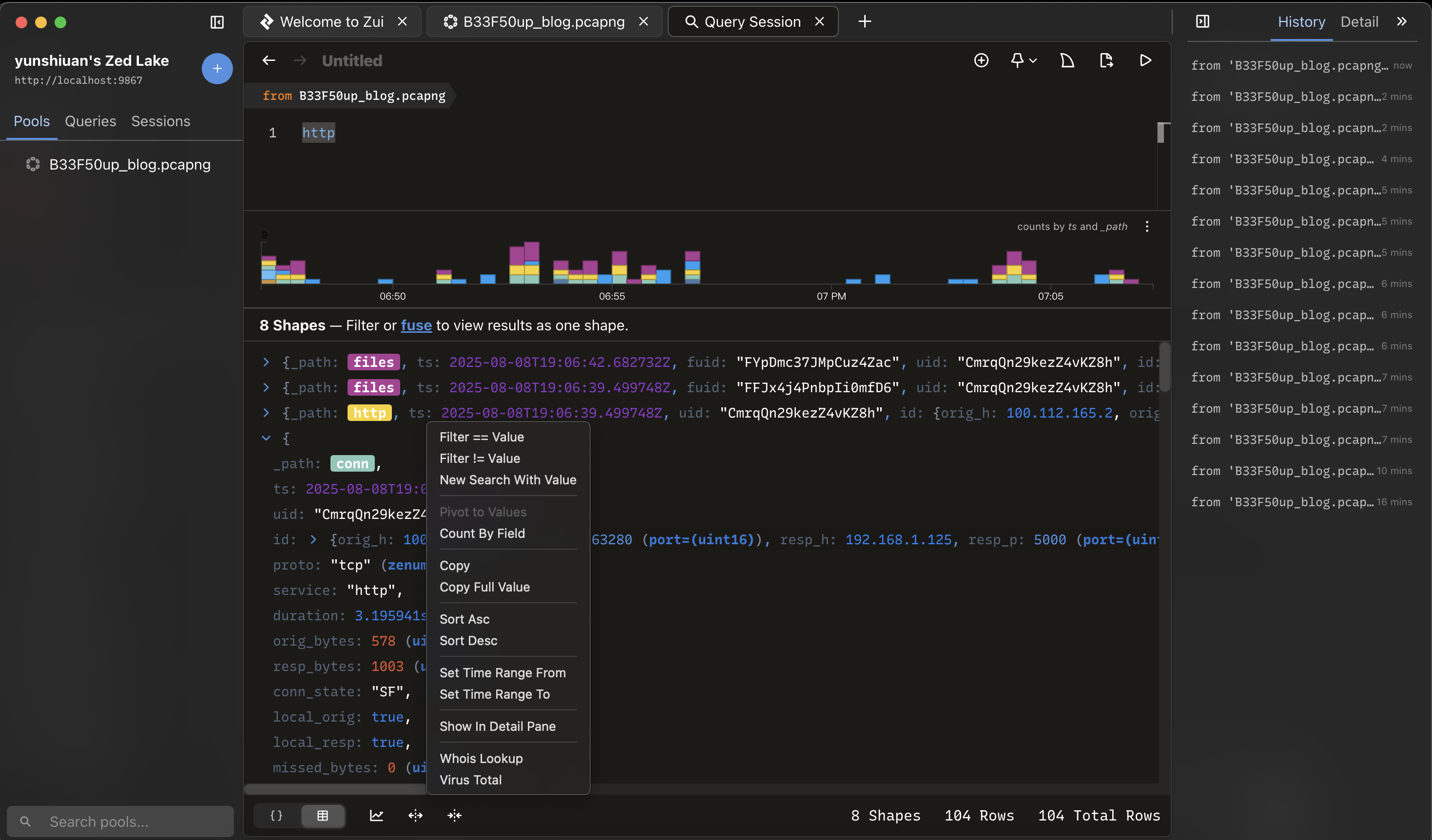
對你想要篩選的資料按右鍵可以自動生成查詢指令
最後也可以下載官方提供預先寫好的查詢
連結:https://github.com/brimdata/brimcap?tab=readme-ov-file#brimcap-queries
下載後queries.json 後按下+的藍色按鈕,點選Import Queries
把剛剛下載的json 檔丟進去,就會匯入預先寫好的query
今天介紹了Zui 以及其中 Zeek 與Suricata功能,也有分享 Zui 的基本操作,Zui 在解一些CTF 題時也會有奇效,雖然沒辦法查看詳細封包內容,但在快速查詢可疑行為或可疑流量時會很好用。
