請問大大
我使用nessus針對公司的ad主機做弱點掃描,報告出來是
SSL Version 2 and 3 Protocol Detection
但是我已經使用Nartac的IIS Crypto工具之類的工具來禁用不安全的選項。
也在登錄檔內檢查
HKey_Local_Machine \ System \ CurrentControlSet \ Control \ SecurityProviders \ SCHANNEL \ Protocols\SSL 2.0\Server-->DWORD設定為0
也用zenmap軟體去檢測443,3389這兩個port都是關閉的
Starting Nmap 7.70 ( https://nmap.org ) at 2020-07-08 17:11 ¥x¥_?D·CRE?!
Nmap scan report for xx.xx.xx.xx
Host is up (0.0010s latency).
PORT STATE SERVICE
443/tcp closed https
MAC Address: 00:00:00:00:00:00 (Microsoft)
Nmap done: 1 IP address (1 host up) scanned in 2.88 seconds
Starting Nmap 7.70 ( https://nmap.org ) at 2020-07-08 17:08 ¥x¥_?D·CRE?!
Nmap scan report for xx.xx.xx.xx
Host is up (0.0010s latency).
PORT STATE SERVICE
3389/tcp closed ms-wbt-server
MAC Address: 00:00:00:00:00:00 (Microsoft)
Nmap done: 1 IP address (1 host up) scanned in 2.91 seconds
今日有找到問題,但是登錄檔內找不到資料,不知要如何關閉
Starting Nmap 7.70 ( https://nmap.org ) at 2020-07-09 10:46 ¥x¥_?D·CRE?!
PORT STATE SERVICE
8089/tcp open unknown
| ssl-enum-ciphers:
| SSLv3:
| ciphers:
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 1024) - D
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 1024) - A
| compressors:
| DEFLATE
| NULL
| cipher preference: client
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
| CBC-mode cipher in SSLv3 (CVE-2014-3566)
| Weak certificate signature: SHA1
| TLSv1.0:
| ciphers:
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 1024) - D
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 1024) - A
| compressors:
| DEFLATE
| NULL
| cipher preference: client
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
| Weak certificate signature: SHA1
| TLSv1.1:
| ciphers:
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 1024) - D
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 1024) - A
| compressors:
| DEFLATE
| NULL
| cipher preference: client
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
| Weak certificate signature: SHA1
| TLSv1.2:
| ciphers:
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 1024) - D
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 1024) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 1024) - A
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 1024) - A
| compressors:
| DEFLATE
| NULL
| cipher preference: client
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
| Weak certificate signature: SHA1
|_ least strength: D

SSL 不一定只被掛在 443/3389 port 上, 任何 tcp port 都可以被掛上 SSL 憑證, 所以先列出你到底有哪些 port 打開了?
通常 AD 主機最有可能的是開了 LDAPS 的 636/3269...
其他還有: tcp 5722, 9389, 424, 3268...
雷神大大,我有找到那個8089 port,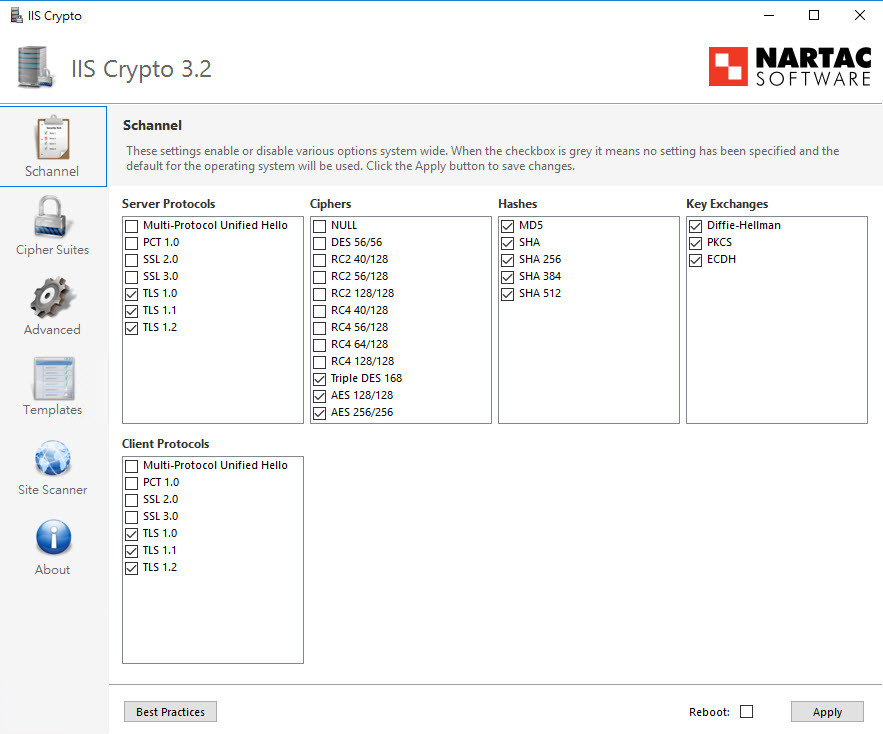
也依照網路教學方式去修改登陸檔,但是我再ad上的登錄檔沒有看到相對應的位置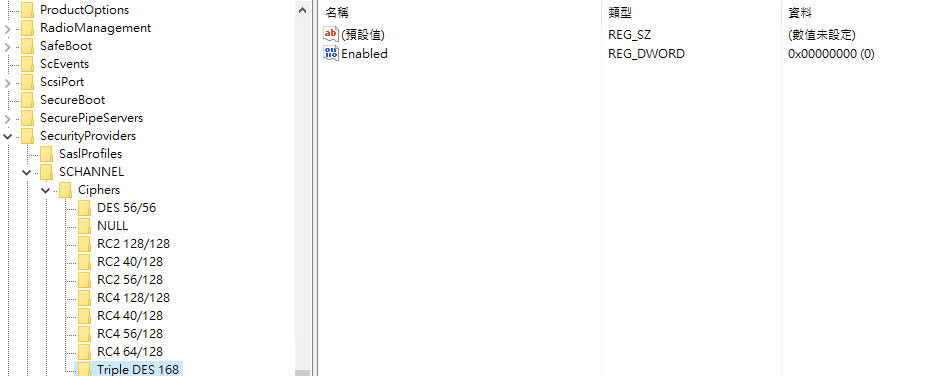 我看預設都是關閉的,再次重新弱掃,還是有出現,這該如何是好><
我看預設都是關閉的,再次重新弱掃,還是有出現,這該如何是好><
先確認一下, tcp 8089 是誰開啟的? 若不是微軟自己開啟的, 你去設定那些對他都無效....(印象中 AD 應該沒有這個 port 才對啊?)
要找到控制 8089 的軟體去修改才對, 並不是通通都歸微軟管...(您是否還多裝了 VMware 相關的軟體?)
除非那個 port 是 IIS 產生的, 那樣用上面那個 IIS Crypto 應該可以關得掉才對?...(TLS 1.0/1.1, MD5/SHA1 都要關掉才行)
謝謝雷神大大的建議
我剛找到了當初有安裝splunk與nagios這兩套監聽軟體,發現是Splunkd management port: 8089,ad裡面如果使用內建防火牆規則將這個port關閉,那會不會導致 splunk server 監聽不到這台ad?另外發現nagios的port 5666 也是跟8089一樣的問題,不知道將這兩個port加入防火牆不允許的規則中會不會有問題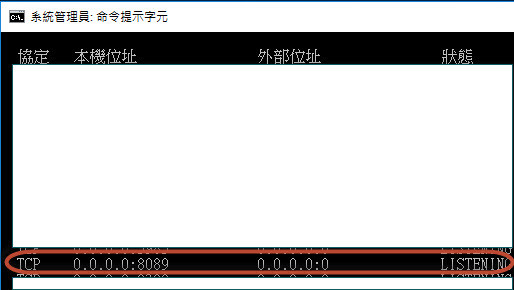
你關掉的話, 這兩套軟體可能會無法正常工作;
Splunk 可以調整 8089 關掉 SSLv3:
How to disable SSLv3 on port 8090
請參考最後一篇回文的內容..
Nagios 則是在 2018/1/23 已經修正過此問題:
Security Vulnerabilities on Nagios Port 5666
先查是否你們的版本太舊? 或者是新版又出現此問題, 那就要去找是否有更新的修正版本?
如果都無法改正的話, 當然只好關掉才能合規了....
好的,謝謝雷神大大的建議
SSLv2/SSLv3的弱點除了https外也可能是smtps/pop3s/imaps或smtp/pop3/imap over TLS造成的,要關對地方才有用,不過除非外面能連上AD那台主機,不然修好SMB相關弱點的priority應該遠高於關SSLv2或SSLv3吧![]() ....
....