介紹一個好用的線上工具,叫做STIX Visualizer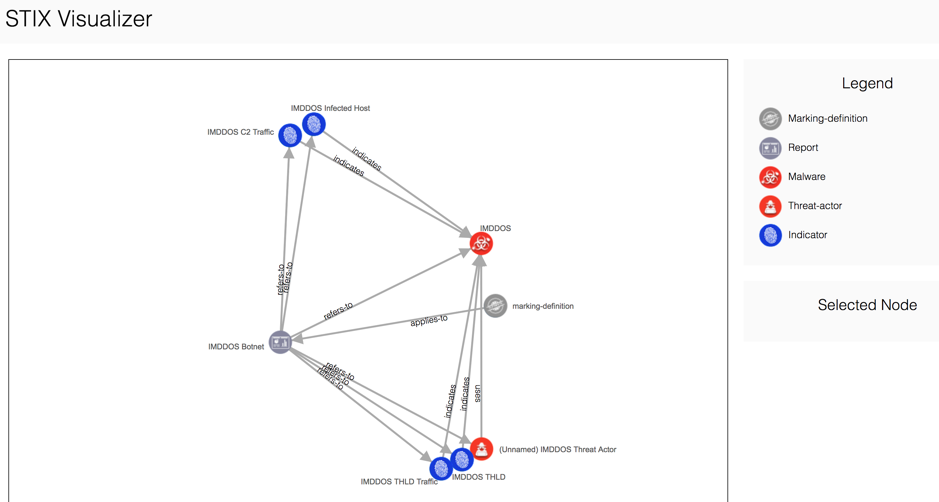
STIX Visualizer 可以將STIX2.0的json結構,經過萃取parsing後,轉換成網絡圖,可以了解到一個threat所帶出來的完整profile。
例如下圖是一個資安威脅報告以poisonivy.json流通,並透過STIX Visualizer繪製成的網絡圖。
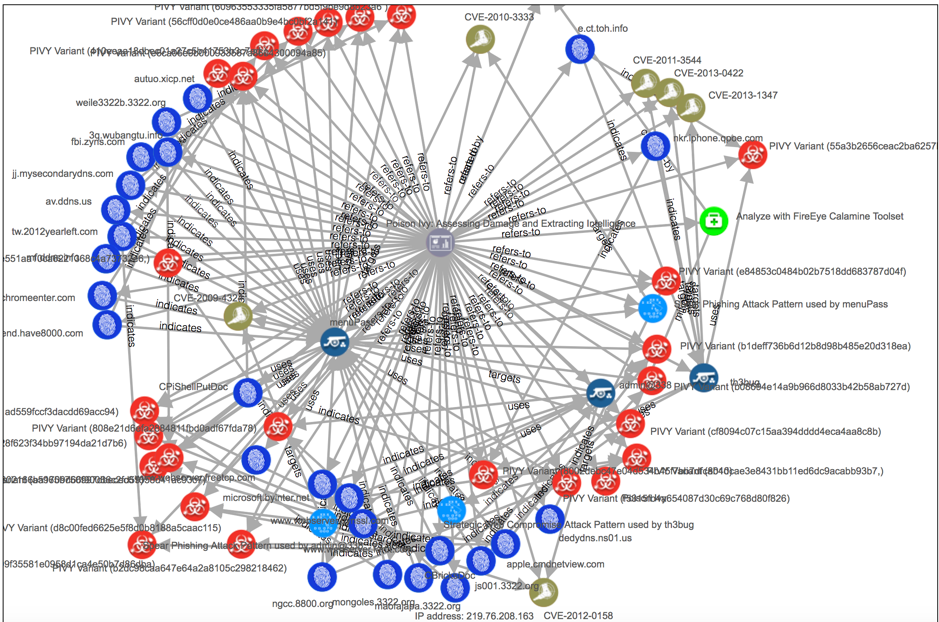
以下是SITX官網對於poisonivy報告範例的說明:
Fireeye's threat report on Poison Ivy covers how this remote access tool (RAT) was used by different campaigns and threat actors. In this converted report, there are several variants of PIVY malware represented by the Malware SDO, as well as Campaign, Threat Actor, Attack Pattern, and Vulnerability objects. Relationship SROs help link the malware variants to the campaigns and threat actors and demonstrate the vulnerabilities PIVY exploits. The JSON representation is available for download.
STIX架構如下,為一個獨立且可再使用的架構,可將各角色之間的關係加以定義。連結箭頭表示各角色間的關係;星號表示該段關係可能會出現0到多次。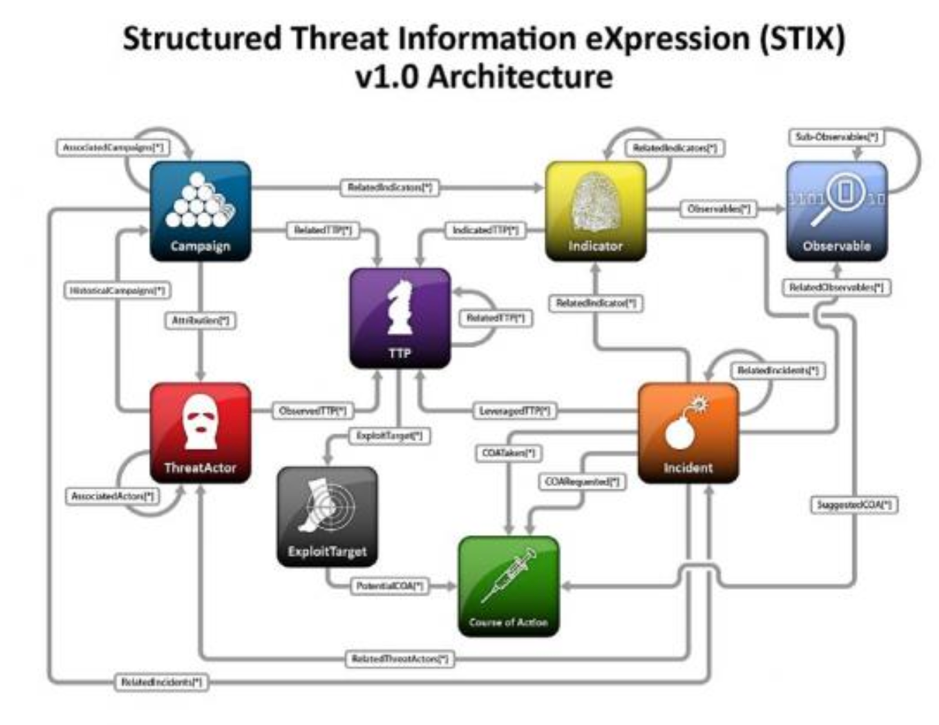
參考來源
poisonivy
https://github.com/oasis-open/cti-stix2-json-schemas/blob/master/examples/threat-reports/poisonivy.json
STIX 2.0 Threat Reports
https://oasis-open.github.io/cti-documentation/stix/examples
STIX
http://newsletter.ascc.sinica.edu.tw/news/read_news.php?nid=3010
