威脅情資分析是徹底暸解攻擊事件最重要的步驟。
有很多分析方法,例如 5W1H、Cyber Kill Chain、Diamond Model,
這邊只講 5W1H
情資應用面向:
之前資安大會上我記得一家廠商有提到整個資安在公司的分層,
我找到那篇新聞,
裏面有一張圖片就列出整個資安框架可以分成
https://www.ithome.com.tw/news/139567
我隨機從上一篇架上好的 OpenCTI 挑一筆事件
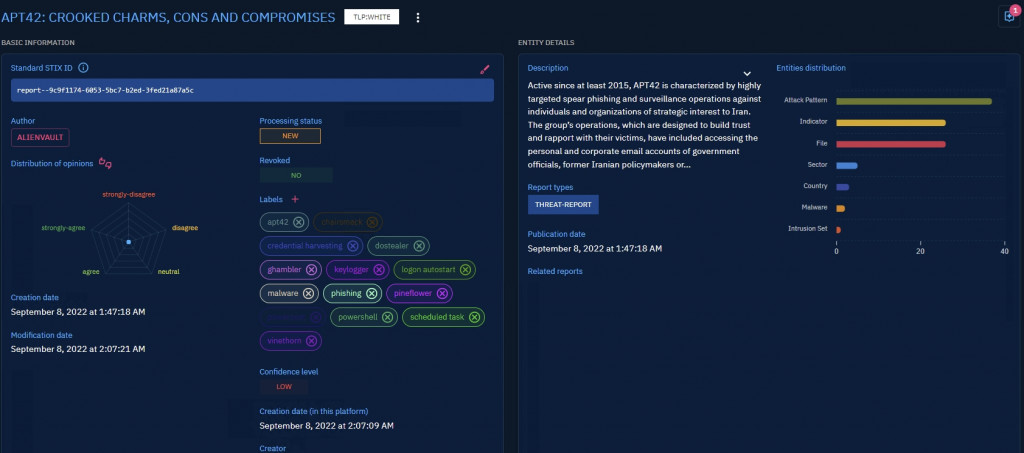
APT42: CROOKED CHARMS, CONS AND COMPROMISES
Active since at least 2015, APT42 is characterized by highly targeted spear phishing and surveillance operations against individuals and organizations of strategic interest to Iran. The group’s operations, which are designed to build trust and rapport with their victims, have included accessing the personal and corporate email accounts of government officials, former Iranian policymakers or political figures, members of the Iranian diaspora and opposition groups, journalists, and academics who are involved in research on Iran. After gaining access, the group has deployed mobile malware capable of tracking victim locations, recording phone conversations, accessing videos and images, and extracting entire SMS inboxes.
資料來源:從 AlienVault 導入 openCTI
https://otx.alienvault.com/pulse/6318d926f7c25668ebeba114
根據 5w1h
明天也分析另外一個事件,應該會偏向 IoC 追蹤。
