Easynews 4.4.1
先說結論: 期末測驗最有機會打穿的兩個套件
Easynews: 系統管理員只是檢查一個布林值(true/false)
Coppermine: Login to account就可上傳backdoor.php
但是先決條件是要先能登入網頁系統才能利用這個套件漏洞打他,可是模擬的受測方說沒有提供測試帳號。🤦♂️,感覺功力從1又落回0,後來我才知道模擬受測方是很認真的在模擬,實際檢測是會提供測試帳號待受測結束刪除,但這次模擬的就是真實呈現受測方不主動配合,甚至網上還有教學稽核員沒有問的不要說、沒有要的資料不要給。😢原來這是一個貓捉老鼠的遊戲!
┌──(kali㉿kali)-[~]
└─$ rhost='172.16.x.x'
※Nmap 工具參考指令:
• Port Scan:nmap -A -oN portscan.txt
• TCP SYN Scan:nmap -sS -oN tcpsynscan.txt
• UDP Scan:nmap -sU -oN udpscan.txt
這三個步驟是寫報告一定要做😮
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sS -T4 -p- $rhost
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-04 09:01 EDT
Nmap scan report for 172.16.x.x
Host is up (0.076s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Nmap done: 1 IP address (1 host up) scanned in 99.53 seconds
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sC -sV -O -p22,25,80,139,445 $rhost
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-04 09:06 EDT
Nmap scan report for 172.16.x.x
Host is up (0.018s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 f7:f5:89:d8:86:90:97:d7:8c:c5:99:6b:66:e7:8e:82 (RSA)
| 256 09:e1:a4:cb:03:b4:28:63:fd:db:f4:ae:f8:17:72:50 (ECDSA)
|_ 256 68:64:f8:7d:8f:8d:be:da:7e:a3:f3:3d:fb:a1:de:d5 (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: ubuntu.itop.com.tw, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Home - Your gallery name here
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 4.0 (90%), Linux 2.6.39 (89%), Linux 3.10 - 3.16 (89%), Linux 2.6.18 (88%), Linux 4.15 - 5.8 (88%), Linux 5.0 (88%), Linux 5.0 - 5.4 (88%), Linux 2.6.32 (88%), Linux 3.4 (88%), Linux 3.5 (88%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: ubuntu.itop.com.tw; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: UBUNTU, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_clock-skew: -15s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-10-04T13:06:04
|_ start_date: N/A
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 55.86 seconds
┌──(kali㉿kali)-[~]
└─$ whatweb $rhost
http://172.16.x.x [200 OK] Apache[2.4.41], Cookies[cpg16x_data], Coppermine[1.6.25 (stable)], Country[RESERVED][ZZ], HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[172.16.x.x], JQuery[1.12.4], Script[text/javascript], Title[Home - Your gallery name here]
Coppermine[1.6.25 (stable)]
1.First of All create php file content as and sequeze this file with zip.
$ cat >> test.php$ zip test.zip test.php
- Login to account
- Go to http://localhost/cpg1.6.x-1.6.25/pluginmgr.php
- Upload zip file
- Visit to php file http://localhost/cpg1.6.x-1.6.25/plugins/test.php
┌──(kali㉿kali)-[~]
└─$ nikto -host $rhost
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.16.x.x
+ Target Hostname: 172.16.x.x
+ Target Port: 80
+ Start Time: 2024-10-04 01:18:58 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.41 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ /: Cookie cpg16x_data created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /images: IP address found in the 'location' header. The IP is "127.0.1.1". See: https://portswigger.net/kb/issues/00600300_private-ip-addresses-disclosed
+ /images: The web server may reveal its internal or real IP in the Location header via a request to with HTTP/1.0. The value is "127.0.1.1". See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2000-0649
+ Apache/2.4.41 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ /admin.php?en_log_id=0&action=config: EasyNews version 4.3 allows remote admin access. This PHP file should be protected. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2006-5412
+ /admin.php?en_log_id=0&action=users: EasyNews version 4.3 allows remote admin access. This PHP file should be protected. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2006-5412
+ /admin.php: This might be interesting.
+ /logs/: This might be interesting.
+ /README: Uncommon header 'tcn' found, with contents: choice.
+ /README: README file found.
+ /update.php: Cookie PHPSESSID created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
+ /LICENSE.txt: License file found may identify site software.
+ /CHANGELOG.txt: A changelog was found.
+ /help.php: A help file was found.
+ /CHANGELOG.txt: Version number implies that there is a SQL Injection in Drupal 7, which can be used for authentication bypass (Drupalgeddon). See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3704 https://www.sektioneins.de/advisories/advisory-012014-drupal-pre-auth-sql-injection-vulnerability.html
+ 8109 requests: 5 error(s) and 18 item(s) reported on remote host
+ End Time: 2024-10-04 01:27:43 (GMT-4) (525 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
- Easynews doesn't properly check to ensure an administrator has been logged in with correct
- username and password information, it only checks if $admin[$en_login_id] == "true".
只要錯5次就被鎖5分鐘沒有辦法用暴力破解的方式解決,我試過密碼潑灑也不行,是針對IP進行鎖定不是帳號。
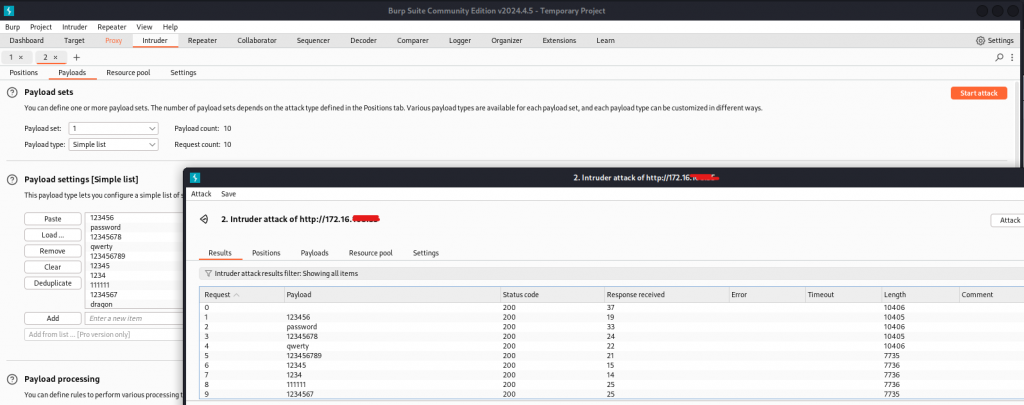
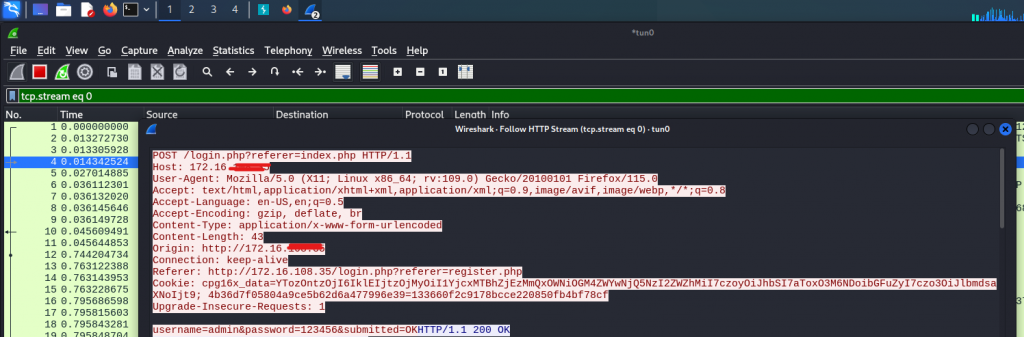
username=admin&password=123456&submitted=OKHTTP/1.1 200 OK
最後我只能用這條,以明碼傳送帳密作為結論依據。
再來是很弱的去寫他幾個套件過期,如果有發覺這是伏筆考驗如何跟受稽方要來一個測試帳號就好了!😒
本來想要再做些測試的,可是為了寫鐵人賽才重灌的虛擬機又掛了,我覺得就這樣結束吧。連網速都可以掉到宿主機500Mbps,虛擬機只有7Mbps,真的可憐我6年的x280,不過因為陸製品牌其實不管是去稽核或檢測也不適合帶,真是水到渠成的滿滿換機理由。😂
鐵人賽結束剛好10月初放榜是否有通過測驗,我發現如果單論HTB簡單到中級的靶機這樣的訓練是足夠的,可是遇到模擬檢測反而困在與受檢方溝通和報告的撰寫上。所以,參賽初期我就寫到這次參加佛心分享算是練習,我在撰寫報告需要引用的法條及撰寫語氣預計要朝訓練語言模型的方向進行,大致上Ollama + Llama3的組合(千問比較適合中文但是又卡在陸製的問題上)訓練出專門用來寫報告的語言模型參加正賽。
我看到有些人會特別寫一篇Day 31,但是真的累了就直接在這邊下結論。
這些都是2-8月間完成的,「0到1的攻擊手自學之旅」這一篇我自認為以剛入門的小白來說我訓練的過程以實作來說蠻夠用,鐵人賽只是讓我快速的將這幾個月累積的經驗進行一次不太完整的書面整理。接下來如同前面所寫過想要準備考幾張證照,也想要在過年前跟羊駝混熟,做個寫分項報告時可以將發現事項給出推薦法條和改善方法的報告產生器。這是我期末測驗遇到最困擾的地方,發現問題、研究方法、問題解決、提出貢獻,應該可以完整地寫一篇2025鐵人賽。
再來就是我已經用dodomenvpn折扣碼買了兩年,等這次連載結束預期會去HackerOne | #1刷戰績培養手感,目標大概會長這樣,但想到還要準備美金帳戶也是挺麻煩的。
這些內容明年不管有沒有投稿鐵人賽,我也會先寫在自己的Medium,不然每天下班回來還要趕稿很累。😂
