今天繼續來做權限管理,試著用 Audit Logs 擷取需要的權限來建立客製化的 IAM 角色。
問了 Gemini 發現可以用 Audit Logs 來記錄用到的權限,所以設定了以下:
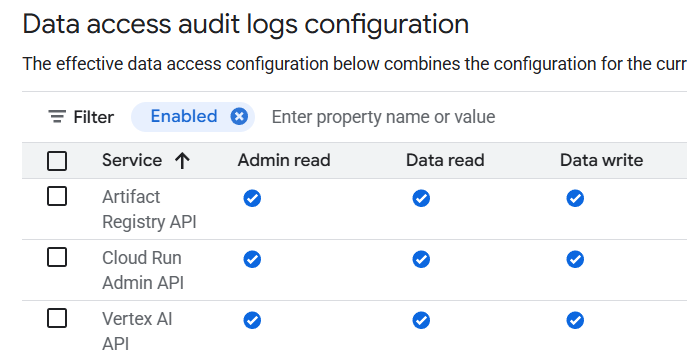
然後就可以從 Logs Explorer 下 Filter 來過濾:
protoPayload.authenticationInfo.principalEmail="xxxxx@xxxxxx.iam.gserviceaccount.com"
這時候觸發 Cloud Build 進行部屬和進行 API 測試,就會將需要的權限記錄進 Logs Explorer 。我將記錄到的 Log 存成文字檔然後用指令來擷取權限清單:
$ cat log.txt | awk 'match($0, /method:[^,]*,/) {print substr($0, RSTART, RLENGTH) }' | sort | uniq
method: "Docker-FinishUpload",
method: "Docker-GetManifest",
method: "Docker-HeadBlob",
method: "Docker-PutManifest",
method: "Docker-StartUpload",
method: "google.cloud.aiplatform.v1.ReasoningEngineExecutionService.QueryReasoningEngine",
method: "google.cloud.aiplatform.v1.ReasoningEngineExecutionService.StreamQueryReasoningEngine",
method: "google.cloud.aiplatform.v1.ReasoningEngineService.GetReasoningEngine",
method: "google.cloud.run.v1.Services.GetService",
method: "google.cloud.run.v1.Services.ReplaceService",
method: "google.longrunning.Operations.WaitOperation",
method: "iam.serviceAccounts.actAs",
請 Gemini 幫我依照這些權限來建立角色,產生了一個 YAML:
title: "Cloud Run and Reasoning Engine Deployer"
description: "Custom role for deploying Cloud Run services and interacting with Reasoning Engines, including Artifact Registry access."
stage: "GA"
permissions:
- artifactregistry.repositories.uploadArtifacts
- artifactregistry.repositories.downloadArtifacts
- aiplatform.reasoningEngines.query
- aiplatform.reasoningEngines.streamQuery
- aiplatform.reasoningEngines.get
- run.services.get
- run.services.update
- longrunning.operations.wait
- iam.serviceAccounts.actAs
然後用 gcloud iam roles create 就可以建立:
gcloud iam roles create CloudRunAndReasoningEngineDeployer --project=... \
--file=custom-deployer-role.yaml
但是一開始產生的設定檔是錯的,把錯誤訊息給 Gemini 看後就會修改成以下:
title: "Cloud Run and Reasoning Engine Deployer"
description: "Custom role for deploying Cloud Run services and interacting with Reasoning Engines, including Artifact Registry access."
stage: "GA"
includedPermissions:
- artifactregistry.repositories.uploadArtifacts
- artifactregistry.repositories.downloadArtifacts
- aiplatform.reasoningEngines.query
- aiplatform.reasoningEngines.get
- run.services.get
- run.services.update
- iam.serviceAccounts.actAs
也就是把 permissions 改成 includedPermissions ,和把 aiplatform.reasoningEngines.query 與 longrunning.operations.wait 砍掉。
最後只要到 IAM 頁面指定角色給 Service Account 就可以了。改完的當下 Security 燈泡還是沒有熄滅,可能需要些時間,明天再看看,接下來把 Agent Engine 也做一次。
這次 Audit Log 多加一個 Google Cloud Storage ,因為 Agent 會被包到 Bucket 內:
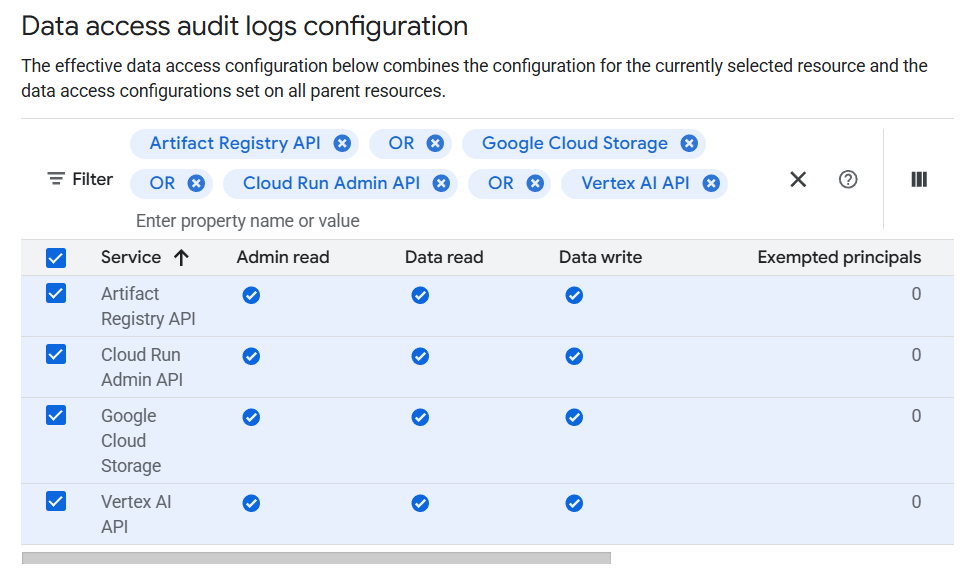
錄下來少很多權限:
method: "google.cloud.aiplatform.v1.ReasoningEngineService.GetReasoningEngine",
method: "google.cloud.aiplatform.v1.ReasoningEngineService.UpdateReasoningEngine",
method: "storage.buckets.get",
method: "storage.objects.create",
method: "storage.objects.get",
一樣請 Gemini 幫我建立角色設定檔:
title: "Reasoning Engine and Storage Accessor"
description: "Custom role for getting/updating Reasoning Engines and managing Storage objects."
stage: "GA"
includedPermissions:
- aiplatform.reasoningEngines.get
- aiplatform.reasoningEngines.update
- storage.buckets.get
- storage.objects.create
- storage.objects.get
下指令建立角色:
gcloud iam roles create ReasoningEngineStorageAccessor --project=... \
--file=reasoning-engine-storage-role.yaml
最後建立 Service Account 然後指定角色就可以了。
不過 iam.serviceAccounts.actAs 這個權限看起來很可疑,查了一下這個權限可以像 sudo 一樣獲得較高的權限來操作,所以要再看看怎麼限制他。
