今天的題目來自 BTLO 這個藍隊解題網站。
這題可有趣了,它是我在 BTLO 這個網站中所解的第一題,那時解完真的是一個「哇!長知識了」的感覺,而且他的題目其實蠻大雜燴的~所以剛好很適合作為硬碟鑑識的結束。
這個網站一題裡面會有很多小題
1. What is the text written on the recovered gif image?
2. Submit Flag1
3. Submit Flag2
4. Submit Flag3
5. What is the filesystem of the provided disk image?
6. What is the original filename of the recovered mp4 file?
提供了兩個檔案
使用 binwalk 看一下裡面有甚麼,發現裡面有 pdf、zip、圖片等等的檔案
binwalk recoverfiles.dd
## DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
1048576 0x100000 Linux EXT filesystem, blocks count: 2304, image size: 2359296, rev 1.0, ext4 filesystem data, UUID=20027131-e907-4aa4-a6c1-bdaa183a183a
5578752 0x552000 GIF image data, version "89a", 280 x 250
5677056 0x56A000 PDF document, version: "1.5"
5677398 0x56A156 Zlib compressed data, default compression
5677863 0x56A327 Zlib compressed data, default compression
5688175 0x56CB6F Zlib compressed data, default compression
5693440 0x56E000 Zip archive data, at least v2.0 to extract, name: word/numbering.xml
5693864 0x56E1A8 Zip archive data, at least v2.0 to extract, name: word/settings.xml
5694444 0x56E3EC Zip archive data, at least v2.0 to extract, name: word/fontTable.xml
5694885 0x56E5A5 Zip archive data, at least v2.0 to extract, name: word/styles.xml
5695743 0x56E8FF Zip archive data, at least v2.0 to extract, name: word/document.xml
5696451 0x56EBC3 Zip archive data, at least v2.0 to extract, name: word/_rels/document.xml.rels
5696766 0x56ECFE Zip archive data, at least v2.0 to extract, name: _rels/.rels
5697000 0x56EDE8 Zip archive data, at least v2.0 to extract, name: word/theme/theme1.xml
5698647 0x56F457 Zip archive data, at least v2.0 to extract, name: [Content_Types].xml
5699590 0x56F806 End of Zip archive, footer length: 22
10186752 0x9B7000 PNG image, 1760 x 857, 8-bit/color RGB, non-interlaced
10186843 0x9B705B Zlib compressed data, compressed
用 testdisk 可以看到檔案結構和檔案名稱,但沒辦法還原(因為檔案大小是 0)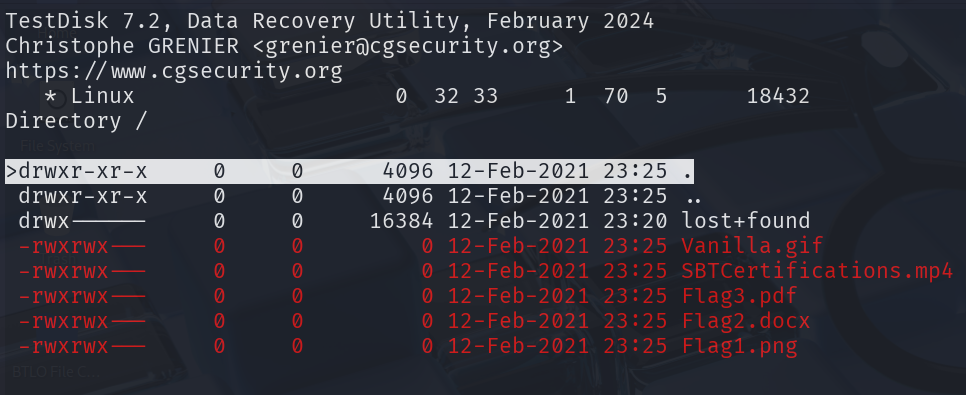
foremost recoverfiles.dd
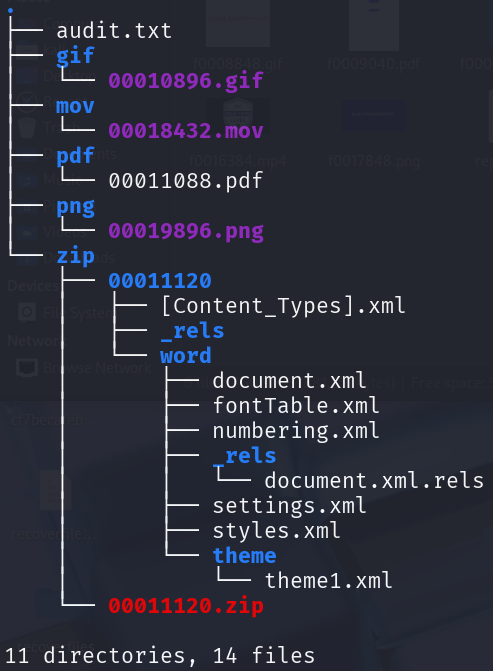
photorec recoverfiles.dd
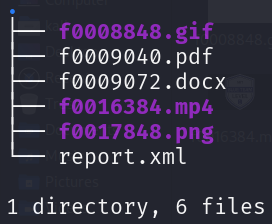

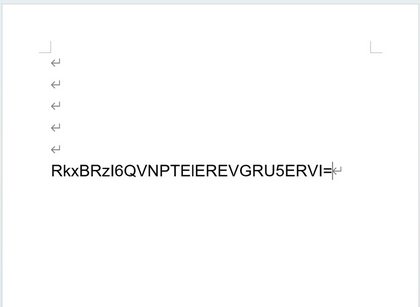
document.xml 中發現 base64 字串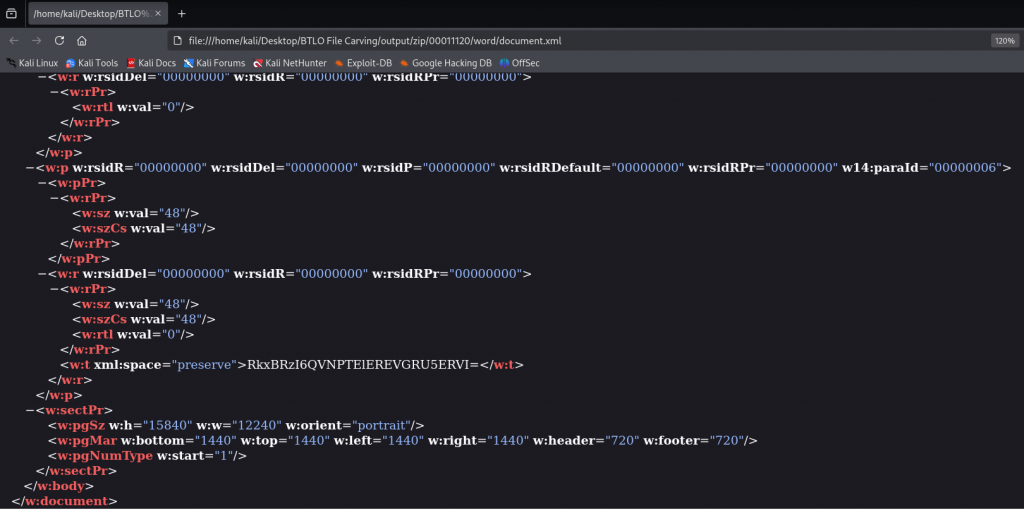
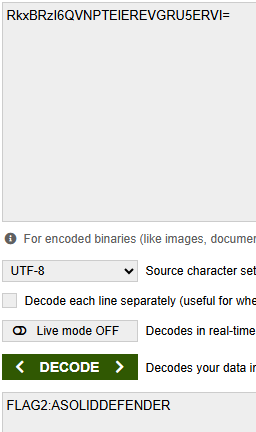
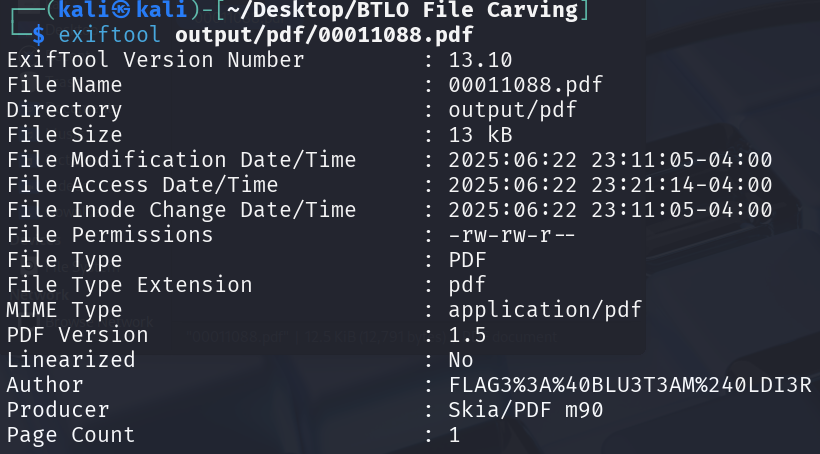
strings 00011088.pdf | grep -i "flag"
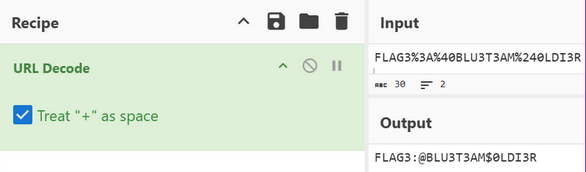
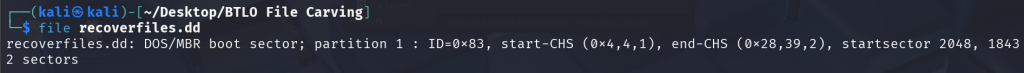
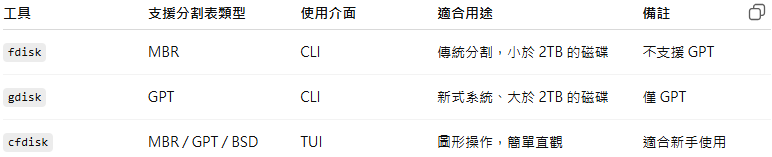
cfdisk recoverfiles.dd
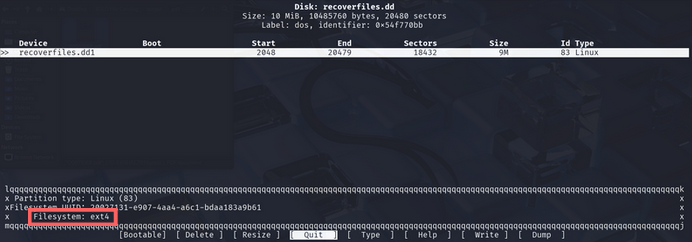
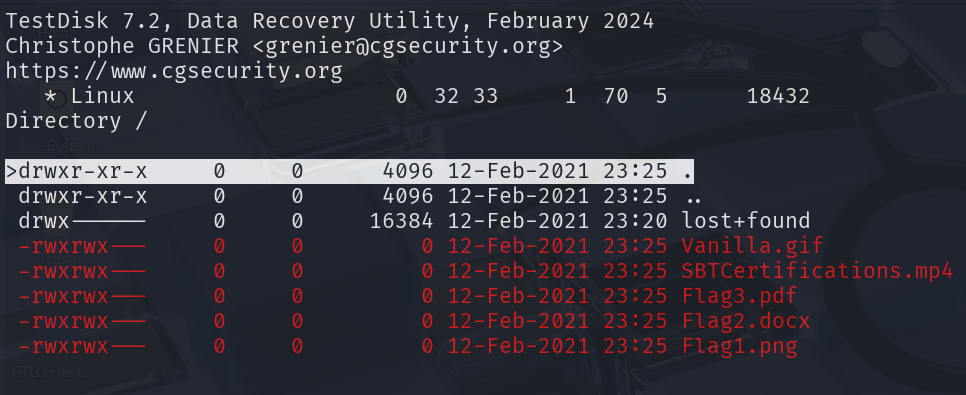
cfdisk 是一個在 Linux 系統中用來建立、刪除和修改磁碟裝置上分割區的指令。它提供了一個基於文字的圖形介面來顯示或操作磁碟分割。
不知道大家有沒有注意到,我昨天用 autopsy 時就是用這題的檔案下去做示範的,也就是說用 autopsy 基本上這題可以秒殺掉,有興趣的話大家可以自己去玩看看喔~
