這篇主要是Writeup,今天目標來把這個課程結束掉,解以下四題
網址 : https://cryptohack.org/courses/intro/xor0/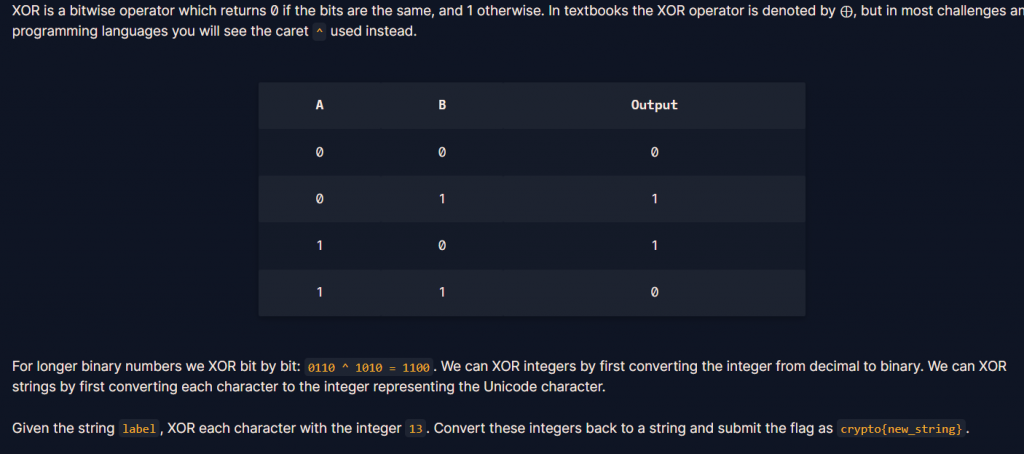
目標為把題目給的"label"跟13做xor,所以要先把label每個字符利用ord()轉成Unicode,之後再一個一個跟13做xor
a = "label"
b = 13
a_num = []
xor_num = []
for i in a : # chr to num
a_num.append(ord(i))
for i in a_num : # get xor_num
xor_num.append(chr(i ^ b))
#flag = crypto{xor_num}
print("crypto{",end="")
for i in xor_num:
print(i,end="")
print("}")
a_num.append(變數)是把變數丟到a_num串列的最後面
之後發現惹更精簡的寫法,可利用python的生成式來寫
新串列名稱 = [生成的項目 for 從迭代物件裡取出的項目 in 可迭代的物件]
from pwn import *
a = "label"
b = 13
a_num =[ord(i) for i in a]
xor_ab = [i ^ b for i in a_num]
xor_string = "".join(chr(i) for i in xor_ab)
print("crypto{"+xor_string+"}")
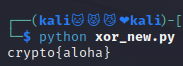
flag : crypto{aloha}
---
網址 : https://cryptohack.org/courses/intro/xor1/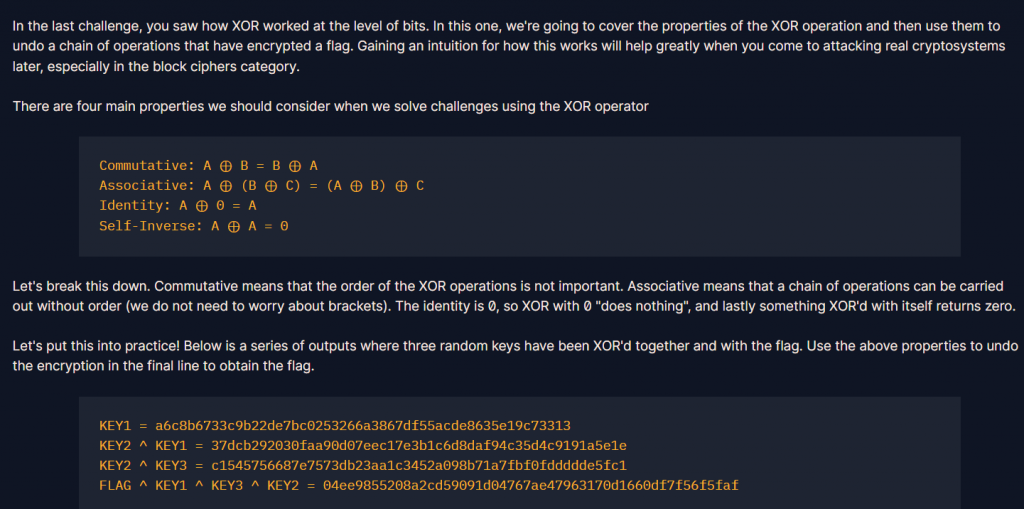
a ^ a = 0、a ^ 0 = a,所以key2 ^ key1 ^ key1 會 = key2
因為key1 ^ key1 = 0 -> key2 ^ 0 = key2
由此可推最後flag = flag_k123 ^ key1 ^ key2 ^ key3
#key1 = "a6c8b6733c9b22de7bc0253266a3867df55acde8635e19c73313"
#key2 ^ key1 = "37dcb292030faa90d07eec17e3b1c6d8daf94c35d4c9191a5e1e"
#key2 ^ key3 = "c1545756687e7573db23aa1c3452a098b71a7fbf0fddddde5fc1"
#flag ^ key1 ^ key2 ^ key3 ="04ee9855208a2cd59091d04767ae47963170d1660df7f56f5faf"
from pwn import *
key1 = bytes.fromhex("a6c8b6733c9b22de7bc0253266a3867df55acde8635e19c73313")
key1_2 = bytes.fromhex("37dcb292030faa90d07eec17e3b1c6d8daf94c35d4c9191a5e1e")
key2_3 = bytes.fromhex("c1545756687e7573db23aa1c3452a098b71a7fbf0fddddde5fc1")
flag_k123 = bytes.fromhex("04ee9855208a2cd59091d04767ae47963170d1660df7f56f5faf")
flag = xor(flag_k123, key2_3, key1)
print(flag.decode())
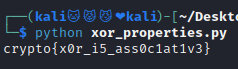
flag : crypto{x0r_i5_ass0c1at1v3}
---
網址 : https://cryptohack.org/courses/intro/xorkey0/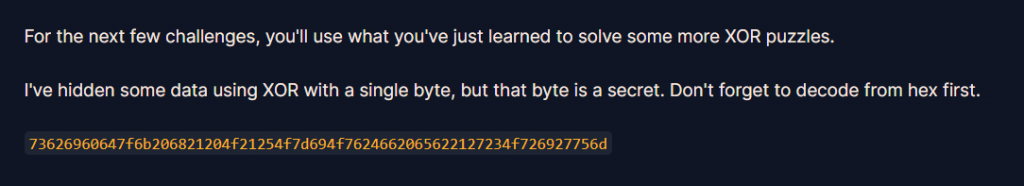
從題目看出他用了某一個字元去跟flag做xor,然後得出"73626960647f6b206821204f21254f7d694f7624662065622127234f726927756d"字串,所以可以用迴圈去爆破,之後如果xor出來的字串有crypto就輸出
from pwn import *
a = bytes.fromhex("73626960647f6b206821204f21254f7d694f7624662065622127234f726927756d")
for i in range(256):
result = xor(a,i).decode()
keyword = "crypto"
if keyword in result:
print(result)
break
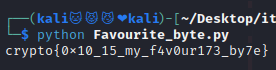
flag : crypto{0x10_15_my_f4v0ur173_by7e}
---
網址 : https://cryptohack.org/courses/intro/xorkey1/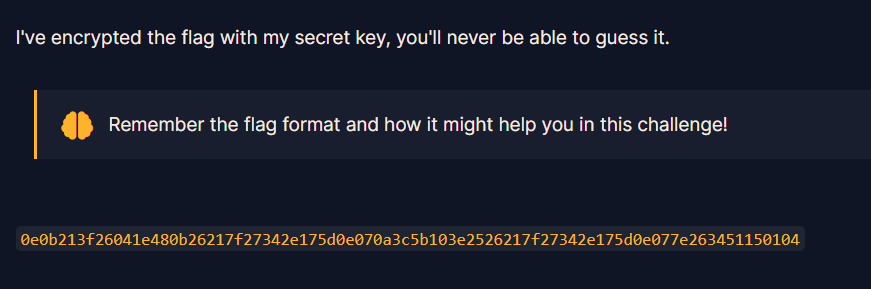
這題很狠,啥都沒給,就給了一個flag xor secret key的結果,不過他提示了我們要記住flag的格式。因為xor是位元運算,就是一個一個bit去做xor得出結果,而且我們知道flag前面一定是"crypto{",代表說我們可以推出他secretkey前面的7個字元
from pwn import *
str = bytearray.fromhex("0e0b213f26041e480b26217f27342e175d0e070a3c5b103e2526217f27342e175d0e077e263451150104")
keyword = b"crypto{"
#secret ^ crypto{ = str[:7]
#str[:7] ^ crypto{ = secret
for i in range(0, len(keyword)):
print(xor(str[i], keyword[i]).decode(),end="")
bytearray.fromhex代表將十六進位數字的字串string 轉換為字節陣列
之後我們得出"myXORke" 可猜測完整secretkey為"myXORkey",所以我們直接把"myXORkey"跟str做xor得出flag
from pwn import *
str = bytes.fromhex("0e0b213f26041e480b26217f27342e175d0e070a3c5b103e2526217f27342e175d0e077e263451150104")
print(xor(str, b"myXORkey").decode())
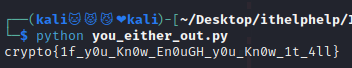
flag : crypto{1f_y0u_Kn0w_En0uGH_y0u_Kn0w_1t_4ll}
經過昨天理解了xor,今天解題蠻順利的,除了最後兩題要稍微想一下,也順利完成了Introduction to CryptoHack 的課程!!!╰(°▽°)╯
明天預計會進入下一個課程 - MODULAR ARITHMETIC接觸模運算
python 列表生成式 : https://ithelp.ithome.com.tw/articles/10274315
