口號:「程式會動不代表安全;套件能裝不代表無毒。」
在 repo 放入最小可運行範例(含幾個「故意舊版」的依賴)
本機與 CI 兩路掃描:
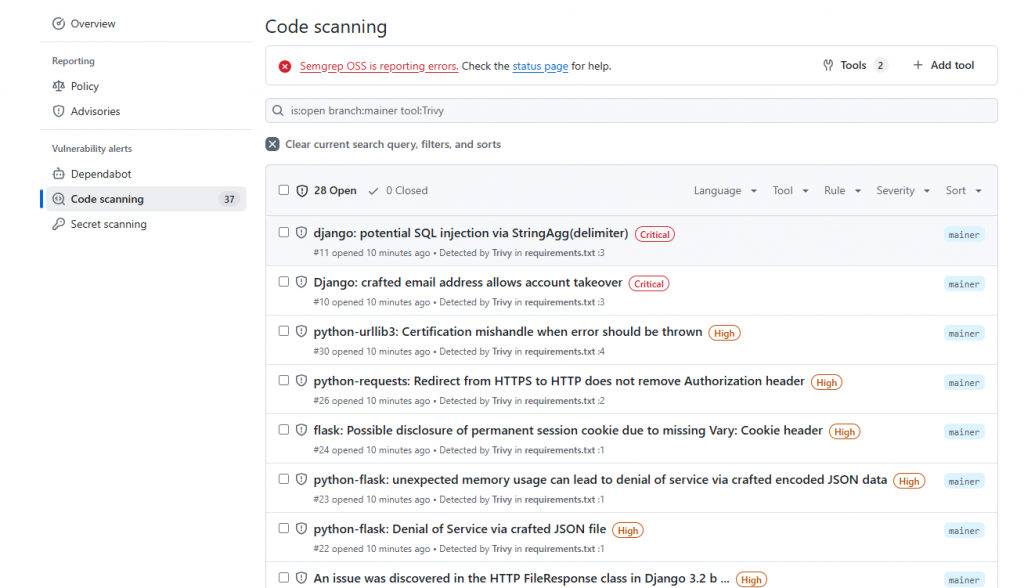
pip-audit 快速檢查requirements.txt、產出 SARIF → 上傳到 GitHub → Security → Code scanning alerts
打開 Dependabot,自動幫你盯套件並開 PR
D:.
│ README.md
│ requirements.txt #新增(舊版的依賴)
│
├─.github
│ └─workflows
│ ci.yml
│ dependabot.yml #新增
│ deploy-pages.yml
│ sast-semgrep.yml
│ sca.yml #新增
│
├─.semgrep
│ custom-rules.yml
│
└─site
index.html
vuln.js
SCA 只要有依賴清單(如
requirements.txt)就能掃。我們這裡用 Python 範例,故意放幾個舊版套件,保證 CI 有 Findings。
requirements.txtflask==0.12
requests==2.19.0
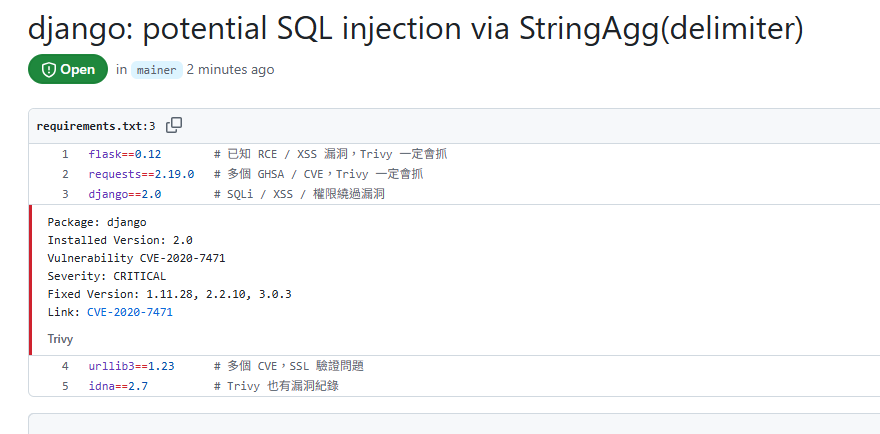
django==2.0
這些都是已知有漏洞的舊版本,會觸發 SCA 報告。
(⚠️ 真實專案請保持更新,不要用這些舊版!)
pip install pip-audit
pip-audit -r requirements.txt
Found 30 known vulnerabilities in 5 packages
Name Version ID Fix Versions
-------- ------- ------------------- --------------------
flask 0.12 PYSEC-2019-179 1.0
flask 0.12 PYSEC-2018-66 0.12.3
flask 0.12 PYSEC-2023-62 2.2.5,2.3.2
requests 2.19.0 PYSEC-2018-28 2.20.0
requests 2.19.0 PYSEC-2023-74 2.31.0
requests 2.19.0 GHSA-9wx4-h78v-vm56 2.32.0
requests 2.19.0 GHSA-9hjg-9r4m-mvj7 2.32.4
django 2.0 PYSEC-2019-18 1.11.19,2.0.12,2.1.7
django 2.0 PYSEC-2021-98 2.2.24,3.1.12,3.2.4
django 2.0 PYSEC-2018-6 1.8.19,1.11.11,2.0.3
django 2.0 PYSEC-2018-2 1.11.15,2.0.8
django 2.0 PYSEC-2018-4 2.0.2
django 2.0 PYSEC-2018-5 1.8.19,1.11.11,2.0.3
django 2.0 PYSEC-2019-17 1.11.18,2.0.10,2.1.5
django 2.0 GHSA-vfq6-hq5r-27r6 1.11.27,2.2.9,3.0.1
django 2.0 GHSA-hmr4-m2h5-33qx 1.11.28,2.2.10,3.0.3
django 2.0 GHSA-6c3j-c64m-qhgq 2.1.9,2.2.2
django 2.0 GHSA-8x94-hmjh-97hq 3.2.15,4.0.7
django 2.0 GHSA-rrqc-c2jx-6jgv 4.2.16,5.0.9,5.1.1
django 2.0 GHSA-7xr5-9hcq-chf9 4.2.22,5.1.10,5.2.2
idna 2.7 PYSEC-2024-60 3.7
urllib3 1.23 PYSEC-2021-108 1.26.5
urllib3 1.23 PYSEC-2019-133 1.24.2
urllib3 1.23 PYSEC-2019-132 1.24.3
urllib3 1.23 PYSEC-2020-148 1.25.9
urllib3 1.23 PYSEC-2023-192 1.26.17,2.0.6
urllib3 1.23 PYSEC-2023-207 1.24.2
urllib3 1.23 PYSEC-2023-212 1.26.18,2.0.7
urllib3 1.23 GHSA-34jh-p97f-mpxf 1.26.19,2.2.2
urllib3 1.23 GHSA-pq67-6m6q-mj2v 2.5.0
pip-audit 會比對 PyPI 資料庫並輸出已知漏洞與修補建議。上面顯示:requirements.txt 裡的套件版本(flask 0.12、requests 2.19.0、django 2.0、idna 2.7、urllib3 1.23)都有已知漏洞。
在 .github/workflows/sca.yml 新增:
name: DevSecOps – SCA (Trivy)
on:
push:
branches: [ "main", "mainer" ]
pull_request:
branches: [ "main", "mainer" ]
workflow_dispatch:
jobs:
sca:
runs-on: ubuntu-latest
permissions:
contents: read
security-events: write
env:
TRIVY_DB_REPOSITORY: ghcr.io/aquasecurity/trivy-db:2
TRIVY_JAVA_DB_REPOSITORY: ghcr.io/aquasecurity/trivy-java-db:1
TRIVY_TIMEOUT: 5m
steps:
- name: Checkout
uses: actions/checkout@v4
- name: Trivy SCA (requirements → SARIF)
uses: aquasecurity/trivy-action@0.24.0
with:
scan-type: fs
scan-ref: ./requirements.txt #
scanners: vuln
vuln-type: library
severity: MEDIUM,HIGH,CRITICAL
ignore-unfixed: true
format: sarif
output: trivy.sarif
limit-severities-for-sarif: true
exit-code: '0'
- name: Trivy SCA (table for debug)
uses: aquasecurity/trivy-action@0.24.0
with:
scan-type: fs
scan-ref: ./requirements.txt
scanners: vuln
vuln-type: library
severity: LOW,MEDIUM,HIGH,CRITICAL
ignore-unfixed: false
format: table
output: '-'
- name: Count vulnerabilities
run: |
COUNT=$(jq '.runs[0].results | length' trivy.sarif)
echo "Detected $COUNT vulnerabilities"
- name: Upload SARIF to GitHub Security tab
uses: github/codeql-action/upload-sarif@v3
with:
sarif_file: trivy.sarif
.github/dependabot.yml:version: 2
updates:
- package-ecosystem: "pip"
directory: "/"
schedule:
interval: "weekly"
open-pull-requests-limit: 5
- package-ecosystem: "github-actions"
directory: "/"
schedule:
interval: "weekly"
重點:Dependabot 不是「自動幫你升級 repo」→ 而是「自動幫你開 PR 提醒」,讓你有機會檢查相容性、跑 CI 測試,再決定要不要合併。
severity 拉到 MEDIUM,HIGH,CRITICAL,或控制只在 PR 時阻擋。做這段的時候一直卡問題
相對位置錯誤->讓requirement沒被抓到
版本的原因,用法不對
